11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 13 abril 2025

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.

10 top anti-phishing tools and services

11 Types of Cybersecurity Attacks You should Be Aware of - Sprinto

As biometrics adoption surges, anti-spoofing is non-negotiable

How do Phishing and Spoofing Attacks Impact Businesses?

11 Different Types of Malware Malware Protection And Prevention

Awareness Of Different Types Of Spoofing Attacks Can Keep Your

Privilege Escalation Attacks: Types, Examples, And Prevention
10 Steps to Cyber Security
Awareness Of Different Types Of Spoofing Attacks Can Keep Your
Why Cloudflare was protected against the SMS phishing attack that

Must Know Phishing Statistics In 2023 - Attacks And Breaches

15 Types of Cyber Attacks You Should Be Aware in 2023

Cyber Security Terms Everyone Should Know- ThriveDX

Network Protocols for Security Professionals
Recomendado para você
-
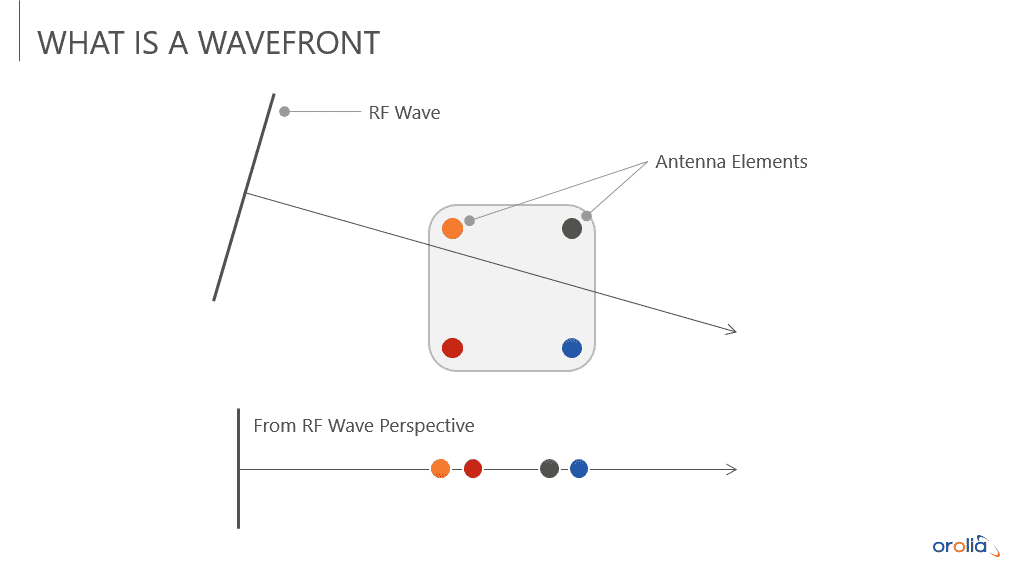 An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing13 abril 2025
An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing13 abril 2025 -
 Airline eCommerce Software & Digital Retailing Solutions13 abril 2025
Airline eCommerce Software & Digital Retailing Solutions13 abril 2025 -
 A comprehensive survey on radio frequency (RF) fingerprinting13 abril 2025
A comprehensive survey on radio frequency (RF) fingerprinting13 abril 2025 -
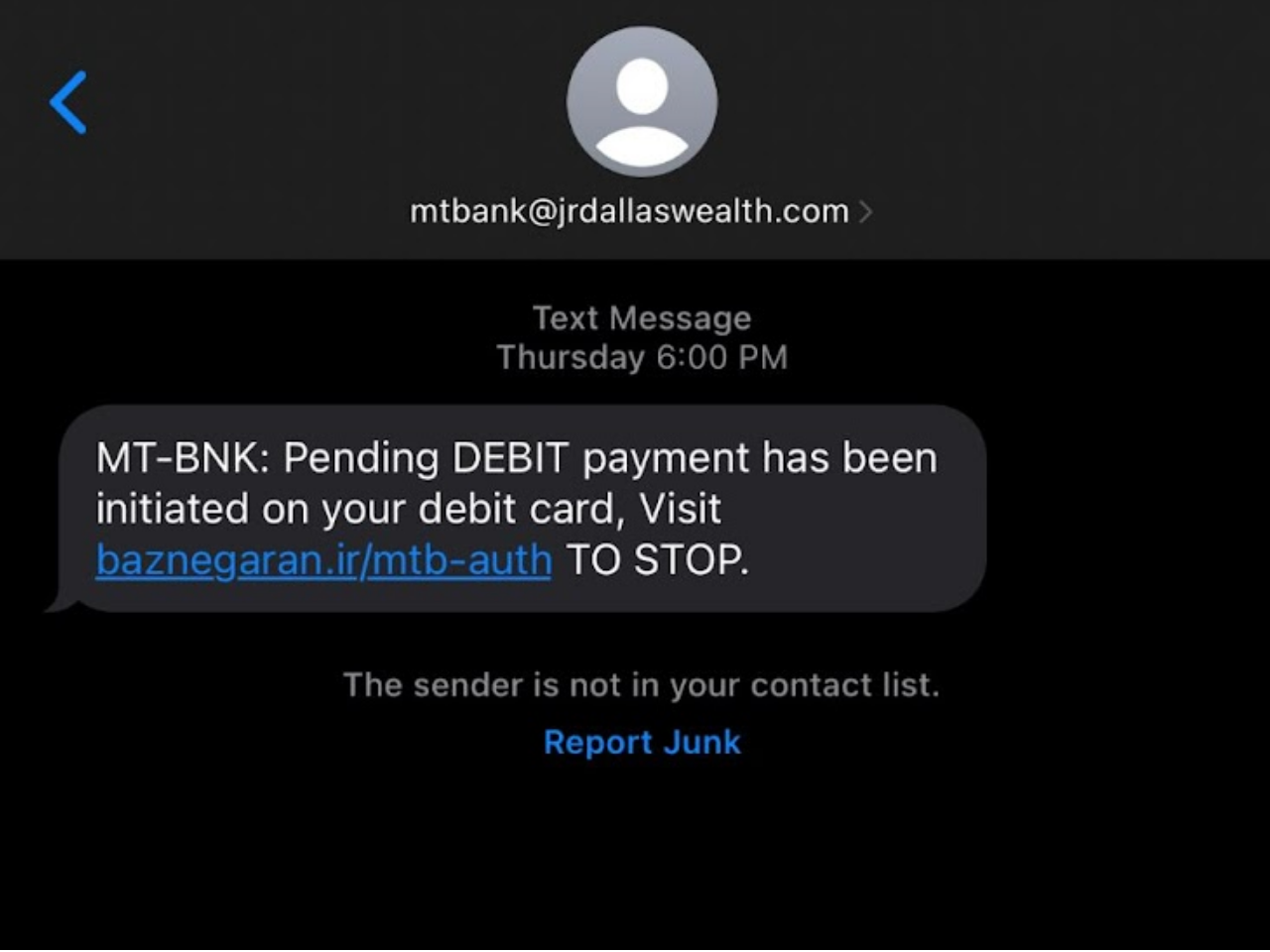 What Is Spoofing In Cybersecurity?13 abril 2025
What Is Spoofing In Cybersecurity?13 abril 2025 -
Red Engine Un Ban13 abril 2025
-
 Device Fingerprinting - SEON Docs13 abril 2025
Device Fingerprinting - SEON Docs13 abril 2025 -
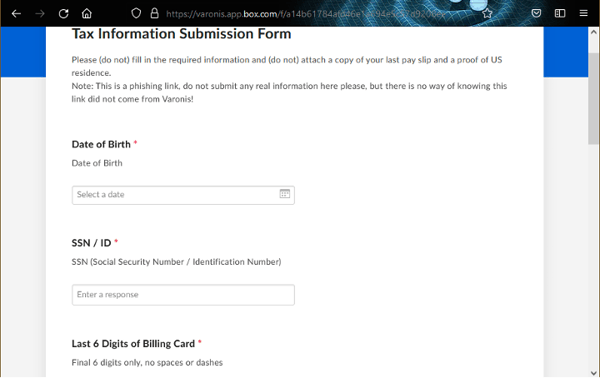 Spoofing SaaS Vanity URLs for Social Engineering Attacks13 abril 2025
Spoofing SaaS Vanity URLs for Social Engineering Attacks13 abril 2025 -
Cracked Hwid Spoofer13 abril 2025
-
![Release] Warzone Spoofer](https://imgur.com/ByHppzY.jpg) Release] Warzone Spoofer13 abril 2025
Release] Warzone Spoofer13 abril 2025 -
 How Do MAC Spoofing Attacks Work?13 abril 2025
How Do MAC Spoofing Attacks Work?13 abril 2025
você pode gostar
-
 1k ROBUX GIVEAWAY pls donate !roblox - creamyybunny on Twitch13 abril 2025
1k ROBUX GIVEAWAY pls donate !roblox - creamyybunny on Twitch13 abril 2025 -
 Sora yori mo Tooi Basho by asevc Kawaii anime, Anime shows, Anime love13 abril 2025
Sora yori mo Tooi Basho by asevc Kawaii anime, Anime shows, Anime love13 abril 2025 -
FNF Classic Hit: Friday Night – Apps on Google Play13 abril 2025
-
 Hello! This is my first and official shirt on Roblox! Feel free to give feedback! : r/roblox13 abril 2025
Hello! This is my first and official shirt on Roblox! Feel free to give feedback! : r/roblox13 abril 2025 -
 Wayne, Total Drama Wiki13 abril 2025
Wayne, Total Drama Wiki13 abril 2025 -
 Hot take: Despite his writing failing to make him anywhere as cool as canon Vergil, DmC Vergil still has a cool design and Empty is an amazing theme song. : r/DevilMayCry13 abril 2025
Hot take: Despite his writing failing to make him anywhere as cool as canon Vergil, DmC Vergil still has a cool design and Empty is an amazing theme song. : r/DevilMayCry13 abril 2025 -
 Do quilombo à floresta: guia de plantas da Mata Atlântica no Vale13 abril 2025
Do quilombo à floresta: guia de plantas da Mata Atlântica no Vale13 abril 2025 -
 Demon Slayer: Kimetsu no Yaiba Promotion Reel13 abril 2025
Demon Slayer: Kimetsu no Yaiba Promotion Reel13 abril 2025 -
 Let's Play Pokémon Infinite Fusion Part 1: Setting Out in a World of Abominations – Curated Critiques13 abril 2025
Let's Play Pokémon Infinite Fusion Part 1: Setting Out in a World of Abominations – Curated Critiques13 abril 2025 -
 Smash Bros Ultimate: 10 Characters Who Could Be The Final DLC13 abril 2025
Smash Bros Ultimate: 10 Characters Who Could Be The Final DLC13 abril 2025