How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 03 abril 2025
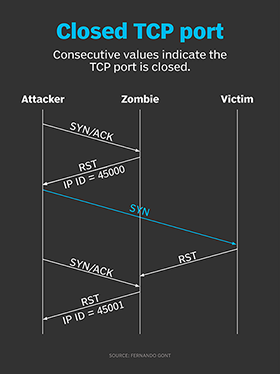
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

Scanning Techniques (EC-Council) EC-Council. Certified Ethical Hacker (CEH) Version 10 eBook w/ iLabs (Volumes 1 through 4). EC-Council Academia, 08/2018. VitalBook file. Flashcards
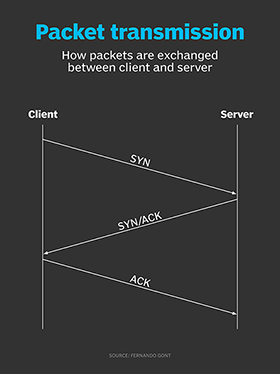
How hackers use idle scans in port scan attacks
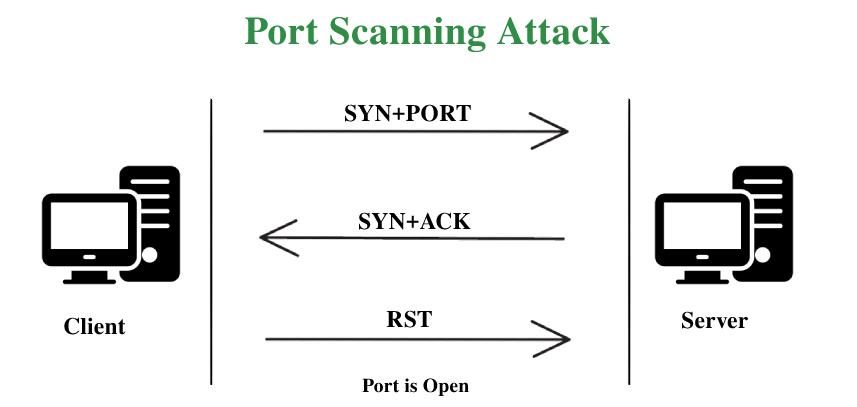
Port Scanning Attack - GeeksforGeeks

A Complete Guide to Nmap, Nmap Tutorial

Hacking techniques

What is a Port Scanner and How Does it Work?
What is a Cyber Attack? Definition and Related FAQs
What Is Nmap? A Comprehensive Tutorial For Network Mapping
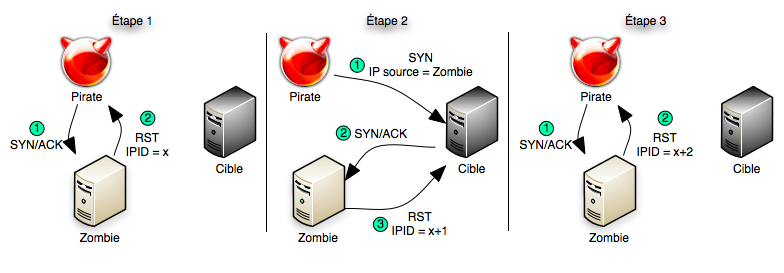
Idle scan - Wikipedia
Recomendado para você
-
 Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders03 abril 2025
Setup OrthoInTouch with topsOrtho - OrthoInTouch - Appointment Reminders03 abril 2025 -
After exchanging my SWITCH to a ROUTER, I… - Apple Community03 abril 2025
-
 IP Chicken - Served Fresh Daily03 abril 2025
IP Chicken - Served Fresh Daily03 abril 2025 -
 CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center03 abril 2025
CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center03 abril 2025 -
 How to Find Your Phone's IP Address on Android or iPhone03 abril 2025
How to Find Your Phone's IP Address on Android or iPhone03 abril 2025 -
 Block ads on all your devices using pfSense, Squid & SquidGuard03 abril 2025
Block ads on all your devices using pfSense, Squid & SquidGuard03 abril 2025 -
 Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K03 abril 2025
Proxying Burp Traffic through VPS using SOCKS Proxy, by Nishith K03 abril 2025 -
 Malware analysis Malicious activity03 abril 2025
Malware analysis Malicious activity03 abril 2025 -
Ethical Hacking With Net03 abril 2025
-
Help Center03 abril 2025
você pode gostar
-
Box de Livros Diários do Vampiro - O Retorno (Lacrado)03 abril 2025
-
![Roblox Action Collection - Tower Defense Simulator: Last Stand Playset [Includes Exclusive Virtual Item] : Toys & Games](https://m.media-amazon.com/images/W/MEDIAX_792452-T2/images/I/71UkD2ZhQHL.jpg) Roblox Action Collection - Tower Defense Simulator: Last Stand Playset [Includes Exclusive Virtual Item] : Toys & Games03 abril 2025
Roblox Action Collection - Tower Defense Simulator: Last Stand Playset [Includes Exclusive Virtual Item] : Toys & Games03 abril 2025 -
 Kono Light Novel Sugoi 2020 – Os melhores personagens de Light03 abril 2025
Kono Light Novel Sugoi 2020 – Os melhores personagens de Light03 abril 2025 -
 BLEACH DUB EPISODE 141 - BiliBili03 abril 2025
BLEACH DUB EPISODE 141 - BiliBili03 abril 2025 -
 O que aconteceu com a Gameloft? - Mobile Gamer03 abril 2025
O que aconteceu com a Gameloft? - Mobile Gamer03 abril 2025 -
 Rogue Company Elite, the mobile version, is coming soon - Jaxon03 abril 2025
Rogue Company Elite, the mobile version, is coming soon - Jaxon03 abril 2025 -
Best Game of Thrones Memes03 abril 2025
-
 Claim your FREE Redeem Code (Pack Code) for Bleach Mobile 3D –03 abril 2025
Claim your FREE Redeem Code (Pack Code) for Bleach Mobile 3D –03 abril 2025 -
 Web Sudoku - Billions of Free Sudoku Puzzles to Play Online03 abril 2025
Web Sudoku - Billions of Free Sudoku Puzzles to Play Online03 abril 2025 -
 Horizon Forbidden West', 'Stray', 'Elden Ring' & More – Vote for Your Favorite Video Games Now! - Bell of Lost Souls03 abril 2025
Horizon Forbidden West', 'Stray', 'Elden Ring' & More – Vote for Your Favorite Video Games Now! - Bell of Lost Souls03 abril 2025


