SQL injection and XSS: what white hat hackers know about trusting
Por um escritor misterioso
Last updated 03 abril 2025

Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where shipping new apps seems more like a race for reputation than a well-considered process, one of the most important questions often falls to the bottom of the “Urgent” column: how will our product be
Why are there suddenly so many hackers lately? - Quora
5 Phases of ETHICAL HACKING

PDF) A Survey on Web Application Vulnerabilities (SQLIA, XSS) Exploitation and Security Engine for SQL Injection
5 Phases of ETHICAL HACKING

WhiteHat Dynamic Application Security Testing (DAST)

SQL injection and XSS: what white hat hackers know about trusting user input

Hackers: The third pillar of security

PDF) Testing and Comparing Web Vulnerability Scanning Tools for SQL Injection and XSS Attacks

Exploring Prompt Injection Attacks, NCC Group Research Blog
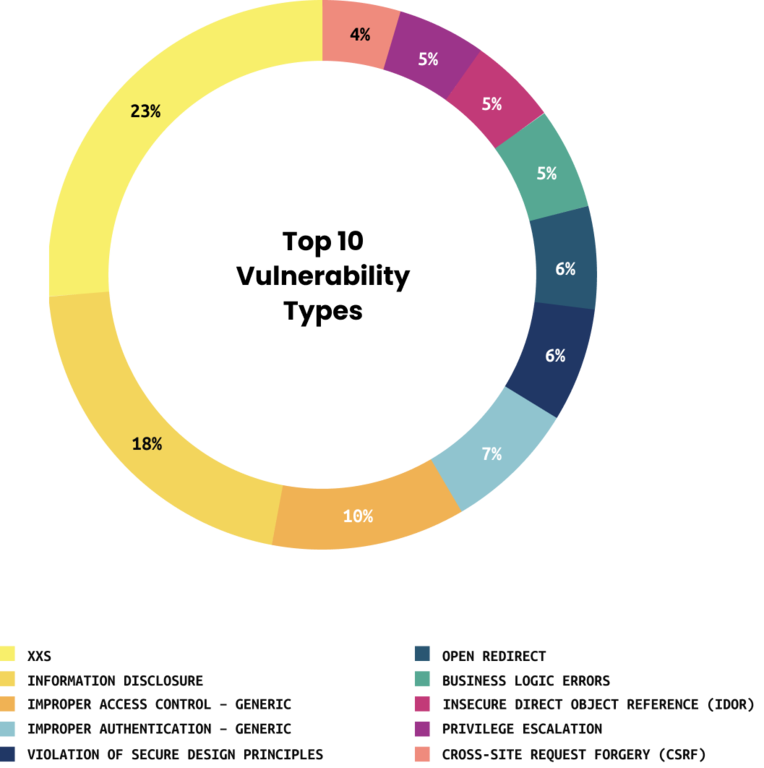
Top Ten Vulnerabilities
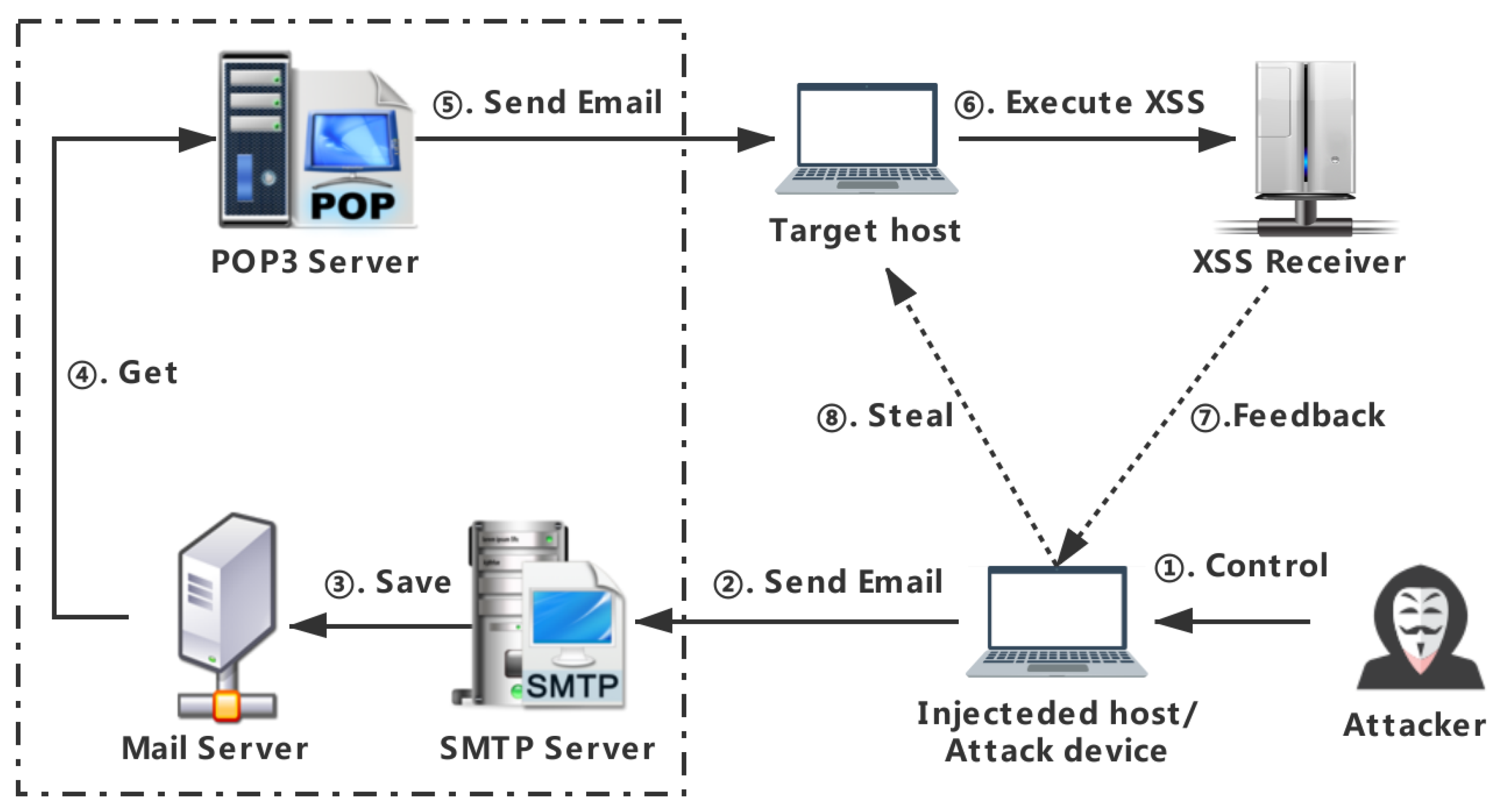
Applied Sciences, Free Full-Text

xss, Breaking Cybersecurity News

Black Hat USA 2017

Bug Bytes #10 - Command Injection, Sublert by @yassineaboukir & Bypassing XSS Detection - Intigriti

National Day of Ethical Hacking Special: How to Become an Ethical Hacker?
Recomendado para você
-
 How to craft an XSS payload to create an admin user in Wordpress03 abril 2025
How to craft an XSS payload to create an admin user in Wordpress03 abril 2025 -
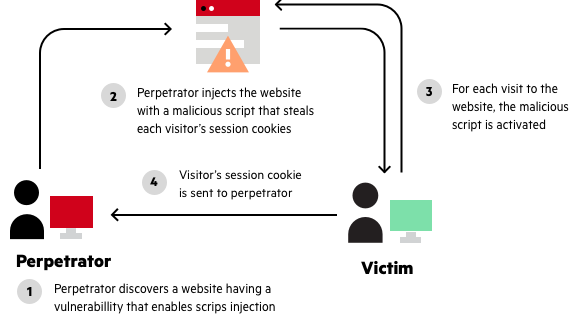 Reflected XSS, How to Prevent a Non-Persistent Attack03 abril 2025
Reflected XSS, How to Prevent a Non-Persistent Attack03 abril 2025 -
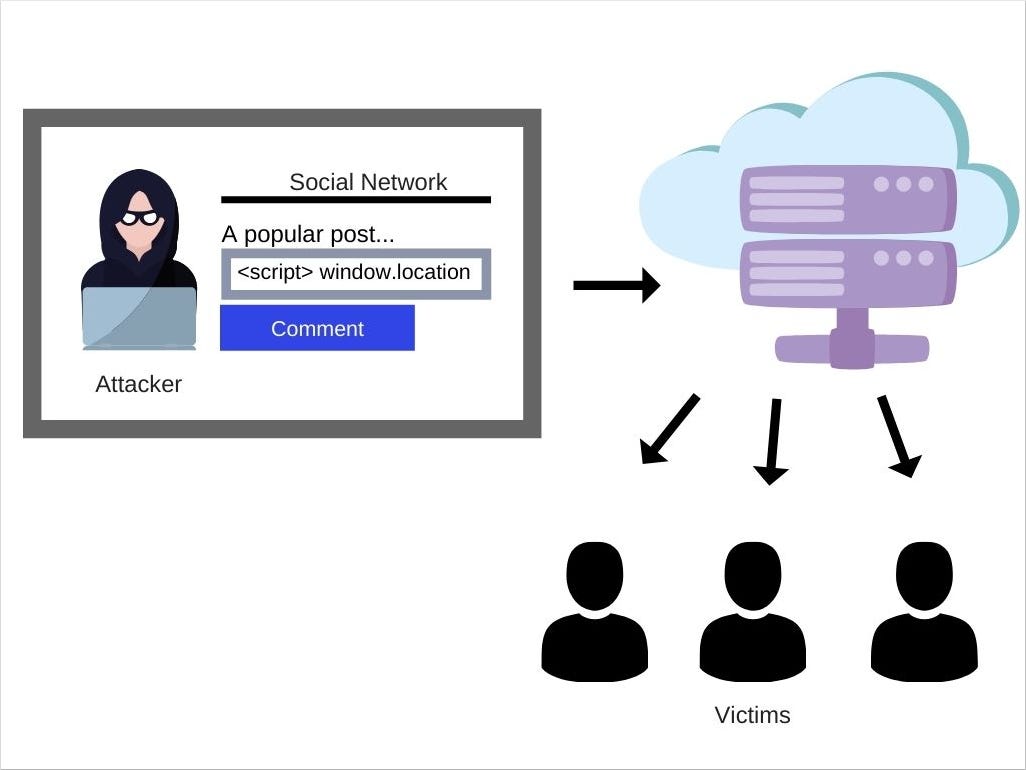 How JavaScript works: 5 types of XSS attacks + tips on preventing03 abril 2025
How JavaScript works: 5 types of XSS attacks + tips on preventing03 abril 2025 -
5: Cross-site scripting (XSS) attack (Source Coursera) [8003 abril 2025
-
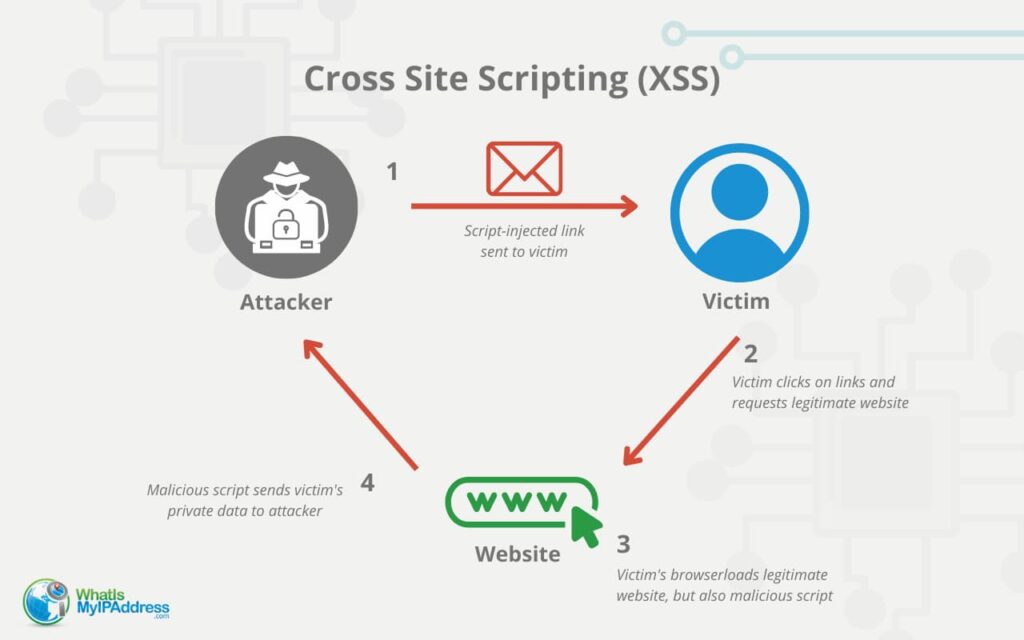 Cross-Site Scripting (XSS) Attacks Explained03 abril 2025
Cross-Site Scripting (XSS) Attacks Explained03 abril 2025 -
Cross Site Scripting Attack - What Is It, How It Works, How to Prevent03 abril 2025
-
 Cross-Site Scripting (XSS) Attack in Modern Frontend Web03 abril 2025
Cross-Site Scripting (XSS) Attack in Modern Frontend Web03 abril 2025 -
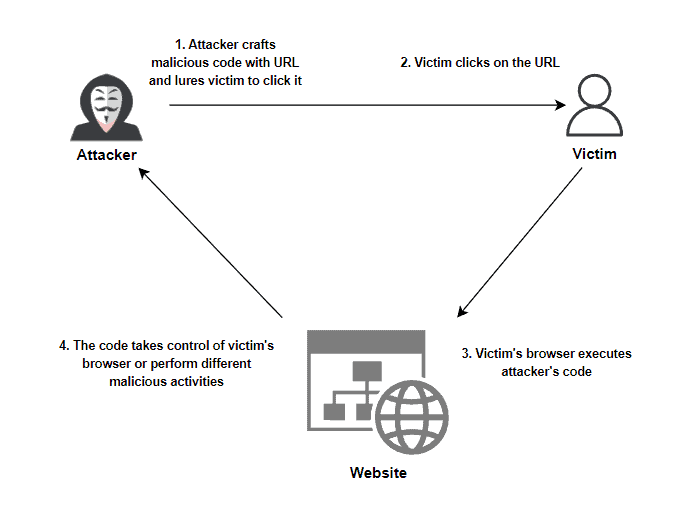 Cross-Site Scripting (XSS) Explained03 abril 2025
Cross-Site Scripting (XSS) Explained03 abril 2025 -
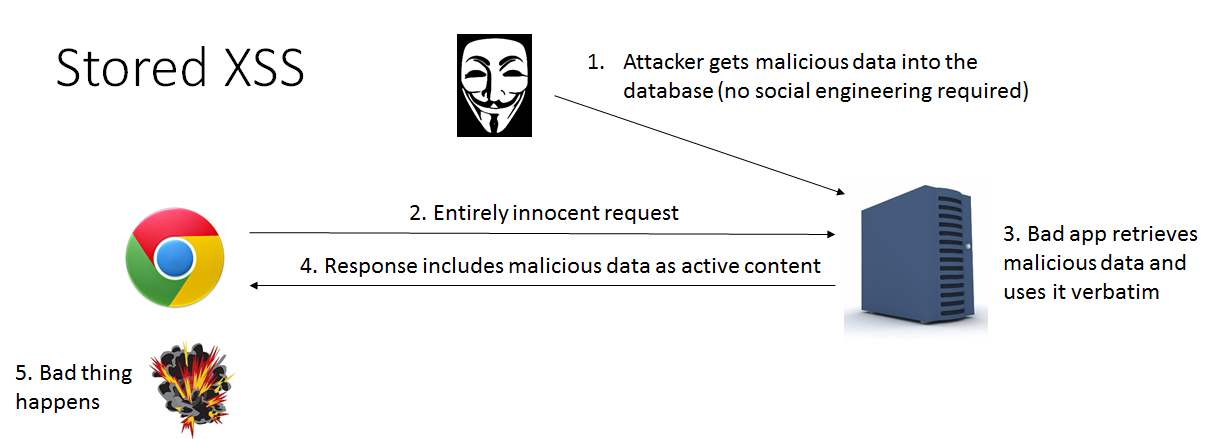 Differences of Stored XSS and Reflected XSS03 abril 2025
Differences of Stored XSS and Reflected XSS03 abril 2025 -
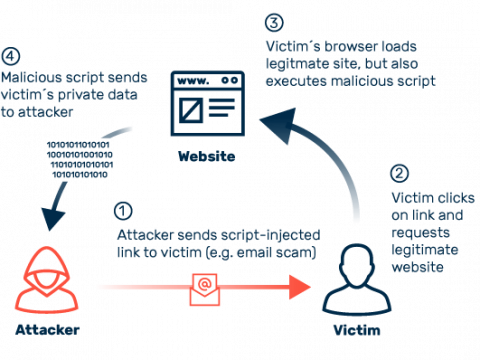 Cross-site scripting (XSS): definition and types03 abril 2025
Cross-site scripting (XSS): definition and types03 abril 2025
você pode gostar
-
 edp445 getting a cupcake (2021 colorized)03 abril 2025
edp445 getting a cupcake (2021 colorized)03 abril 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/h/u/XbP1BoRIOOmAMKTb5VQA/starship-troopers-terran-command-tropas-estelares-filme-1998.jpg) Tropas Estelares, filme clássico dos anos 90, ganhará novo jogo em 202003 abril 2025
Tropas Estelares, filme clássico dos anos 90, ganhará novo jogo em 202003 abril 2025 -
 Giaccio and his ice powers, Vento Aureo03 abril 2025
Giaccio and his ice powers, Vento Aureo03 abril 2025 -
 World Rapid Chess Championship Day 3: Abdusattorov and Kosteniuk03 abril 2025
World Rapid Chess Championship Day 3: Abdusattorov and Kosteniuk03 abril 2025 -
 Street Fighter 6 Hypes up Imminent Release with Launch Trailer03 abril 2025
Street Fighter 6 Hypes up Imminent Release with Launch Trailer03 abril 2025 -
 Why Did the Chicken Cross the Road?03 abril 2025
Why Did the Chicken Cross the Road?03 abril 2025 -
 What Chat Commands can I Use in Game Chat? - Chess.com Member Support and FAQs03 abril 2025
What Chat Commands can I Use in Game Chat? - Chess.com Member Support and FAQs03 abril 2025 -
 Tata Estaniecki rebate crítica por não levar filha à viagem: 'Só a mulher recebe julgamento' - Famosos03 abril 2025
Tata Estaniecki rebate crítica por não levar filha à viagem: 'Só a mulher recebe julgamento' - Famosos03 abril 2025 -
 TEN CUIDADO CON ESTO! TODO SOBRE PLAYSTATION STARS03 abril 2025
TEN CUIDADO CON ESTO! TODO SOBRE PLAYSTATION STARS03 abril 2025 -
 Noa Lang Arsenal Leicester transfer battle03 abril 2025
Noa Lang Arsenal Leicester transfer battle03 abril 2025