Using an Incident-Focused Model for Information Security Programs
Por um escritor misterioso
Last updated 28 março 2025

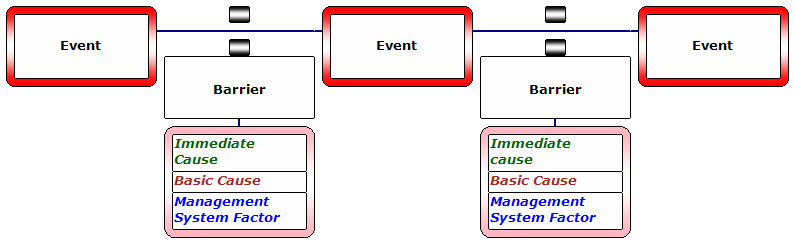
[nodOrganizations attempt to prevent information security incidents by embedding tools in policies and practices across business functions. Because it is not possible to completely prevent security events, organizations must also include proven response practices as part of their security program. e:summary]
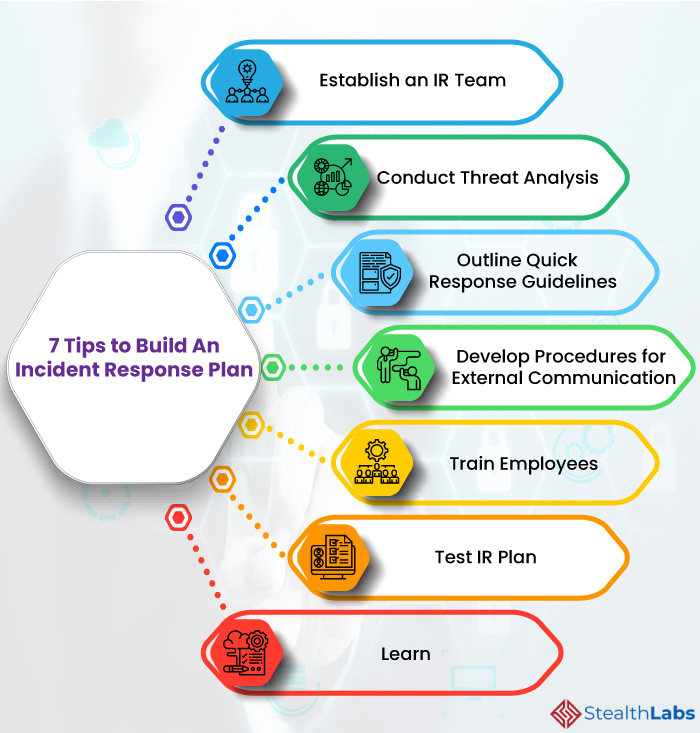
6 Steps to an Effective Cyber Incident Response Plan (+ Tips)
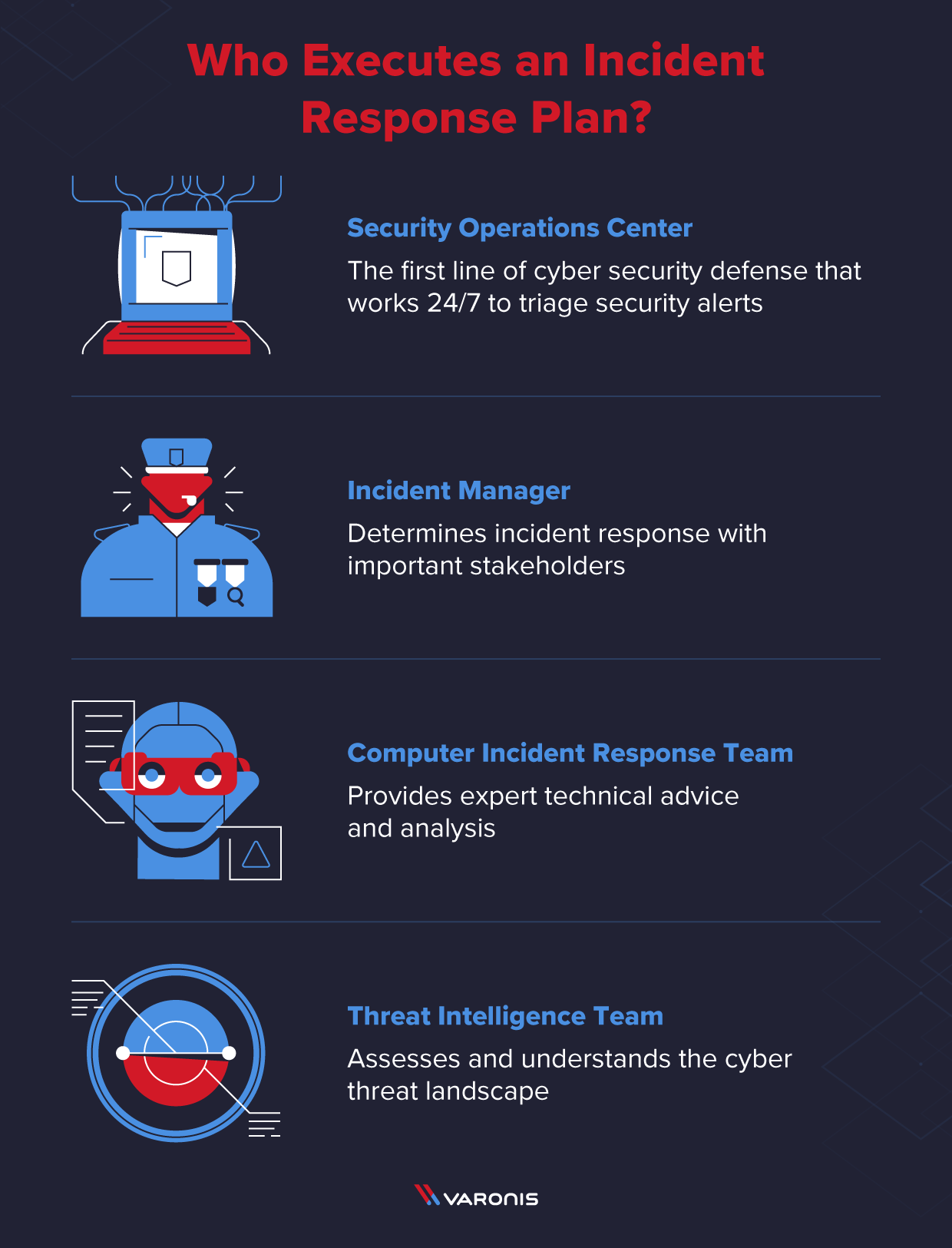
What is an Incident Response Plan and How to Create One

Incident Response SANS: The 6 Steps in Depth

Types Of Security Controls Explained

What is SOAR (Security Orchestration, Automation, and Response
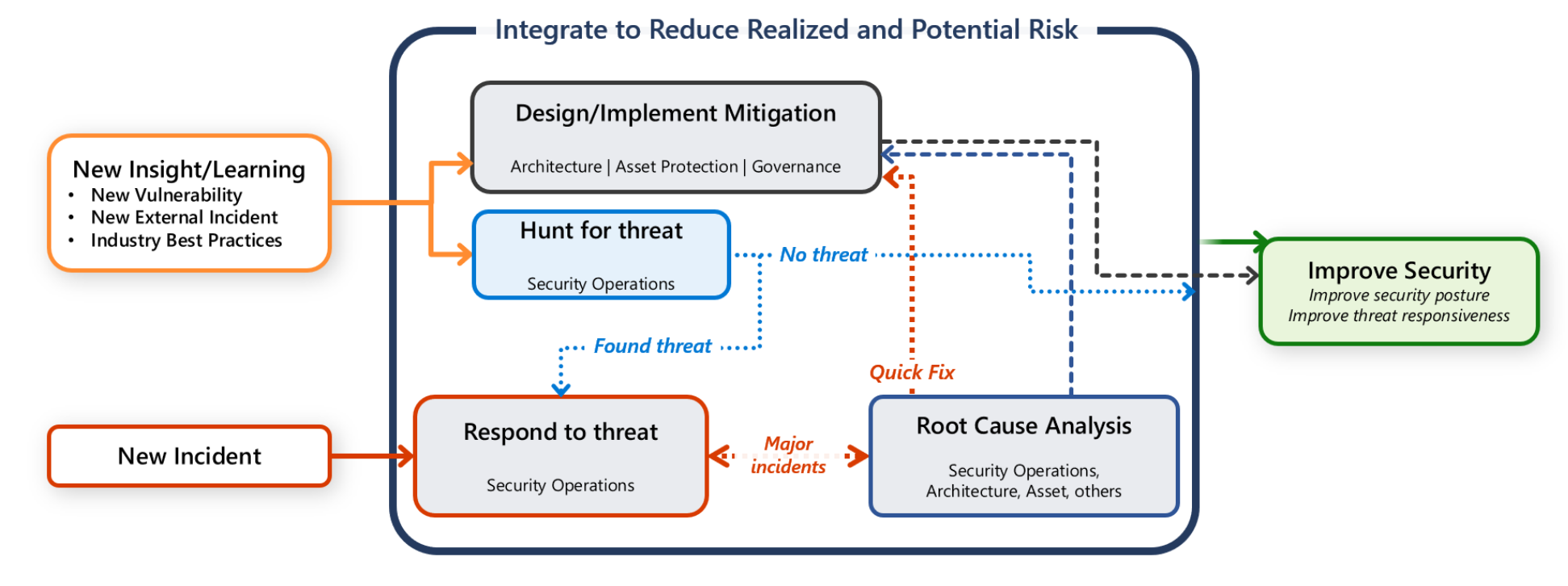
Recommendations for security incident response - Microsoft Azure

CIS Critical Security Control 17: Incident Response and Management
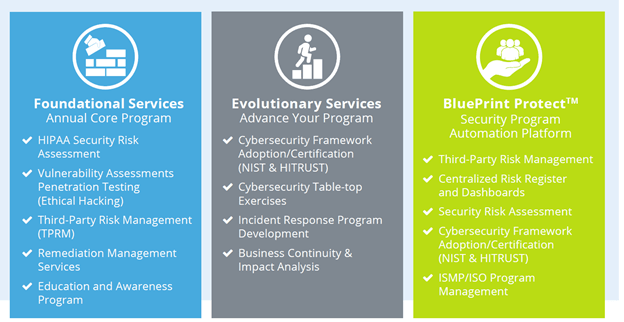
Healthcare Security Essentials Program for VC & PE Portfolio
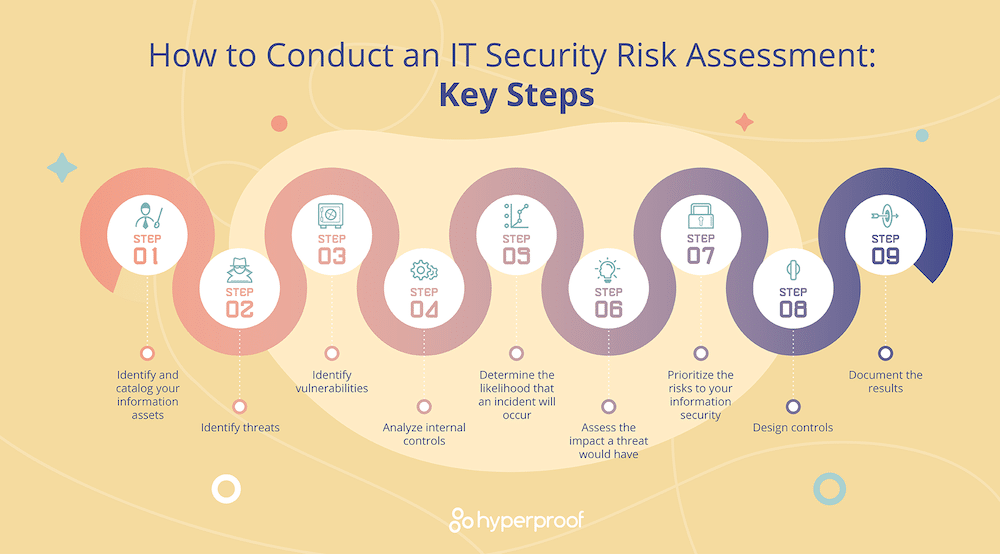
How to Perform a Successful IT Risk Assessment - Hyperproof

The Importance of Cyber Security Awareness in Education

What is Incident Management Policy? - Sprinto

What is a Cybersecurity Framework? — RiskOptics
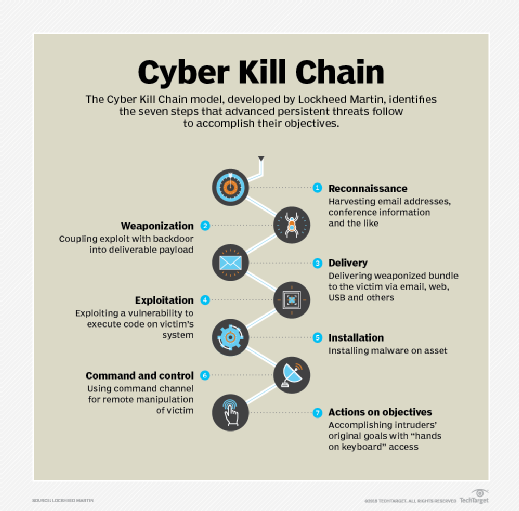
10 Types of Security Incidents and How to Handle Them

Information Security, Global

Product Security Secure Development
Recomendado para você
-
Learning from incidents28 março 2025
-
 The learning cycle for incidents.28 março 2025
The learning cycle for incidents.28 março 2025 -
 Safety Lessons Learned Template - Construction Documents And Templates28 março 2025
Safety Lessons Learned Template - Construction Documents And Templates28 março 2025 -
 Process Safety Incidents: Causes, Consequences, and Lessons Learned28 março 2025
Process Safety Incidents: Causes, Consequences, and Lessons Learned28 março 2025 -
Solved SCEN You have a dual role as an experienced and28 março 2025
-
 Embrace Mistakes to Build a Learning Culture28 março 2025
Embrace Mistakes to Build a Learning Culture28 março 2025 -
 collaboration28 março 2025
collaboration28 março 2025 -
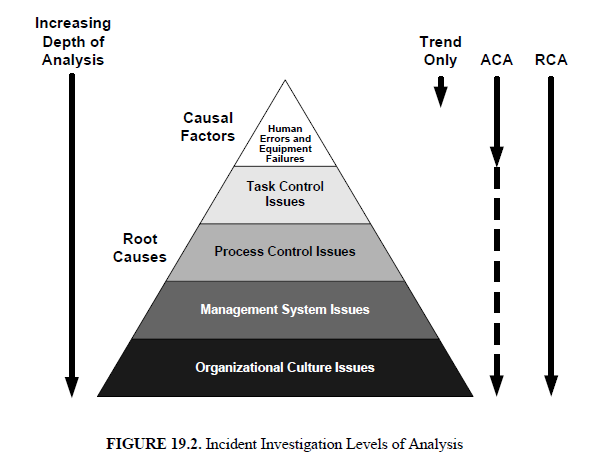 Introduction to Incident Investigation28 março 2025
Introduction to Incident Investigation28 março 2025 -
Wildland Fire Lessons Learned Center28 março 2025
-
 PPT - Responding to Safety & Environmental Incidents28 março 2025
PPT - Responding to Safety & Environmental Incidents28 março 2025
você pode gostar
-
About: Anime Couple Kissing Wallpaper (Google Play version)28 março 2025
-
Pedro Ribeiro: «No futebol tudo muda num lance»28 março 2025
-
 mairimashita iruma kun trio|TikTok Search28 março 2025
mairimashita iruma kun trio|TikTok Search28 março 2025 -
 Download Flame, Back, Fire. Royalty-Free Vector Graphic - Pixabay28 março 2025
Download Flame, Back, Fire. Royalty-Free Vector Graphic - Pixabay28 março 2025 -
 Anime One Piece Chaveiro Luffy Tony Sanji PVC chaveiro mochila28 março 2025
Anime One Piece Chaveiro Luffy Tony Sanji PVC chaveiro mochila28 março 2025 -
 Minecraft: Curse of Vanishing Explained28 março 2025
Minecraft: Curse of Vanishing Explained28 março 2025 -
Sinister shadows abound this Halloween season. Team GO Rocket28 março 2025
-
 How Old Is Chess Player, Andrea Botez In 2022? - Starsgab28 março 2025
How Old Is Chess Player, Andrea Botez In 2022? - Starsgab28 março 2025 -
 Jogos Sul-americanos de Praia Santa Marta - Dia 4 Beach Tennis semifinal e final28 março 2025
Jogos Sul-americanos de Praia Santa Marta - Dia 4 Beach Tennis semifinal e final28 março 2025 -
 Jogo de tabuleiro de xadrez28 março 2025
Jogo de tabuleiro de xadrez28 março 2025