Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 28 março 2025
Collecting debug logs - Portable Security 3.0
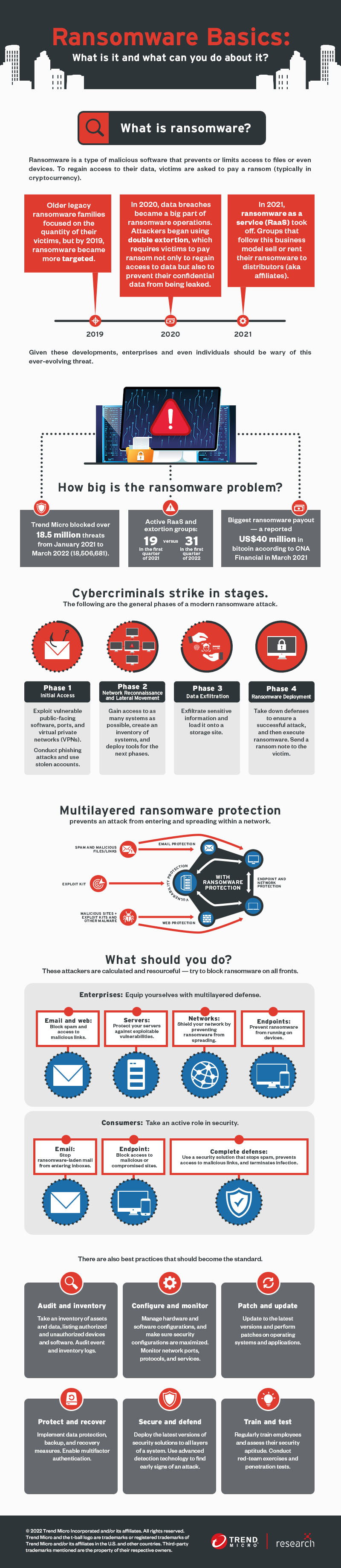
Ransomware - Definition
Trend Micro Update Toolset - Endpoint Application Control 2.0
Empty list for endpoint and domain nodes after agent deployment - OfficeScan
Ransomware - Definition
How to adjust Trend Micro scan settings on Windows

Climate change - Wikipedia

What is EAP-TLS?

Wi-Fi Spoofing: A Major Threat to Network Security - Cloud RADIUS

Top 10 Data Loss Prevention Software
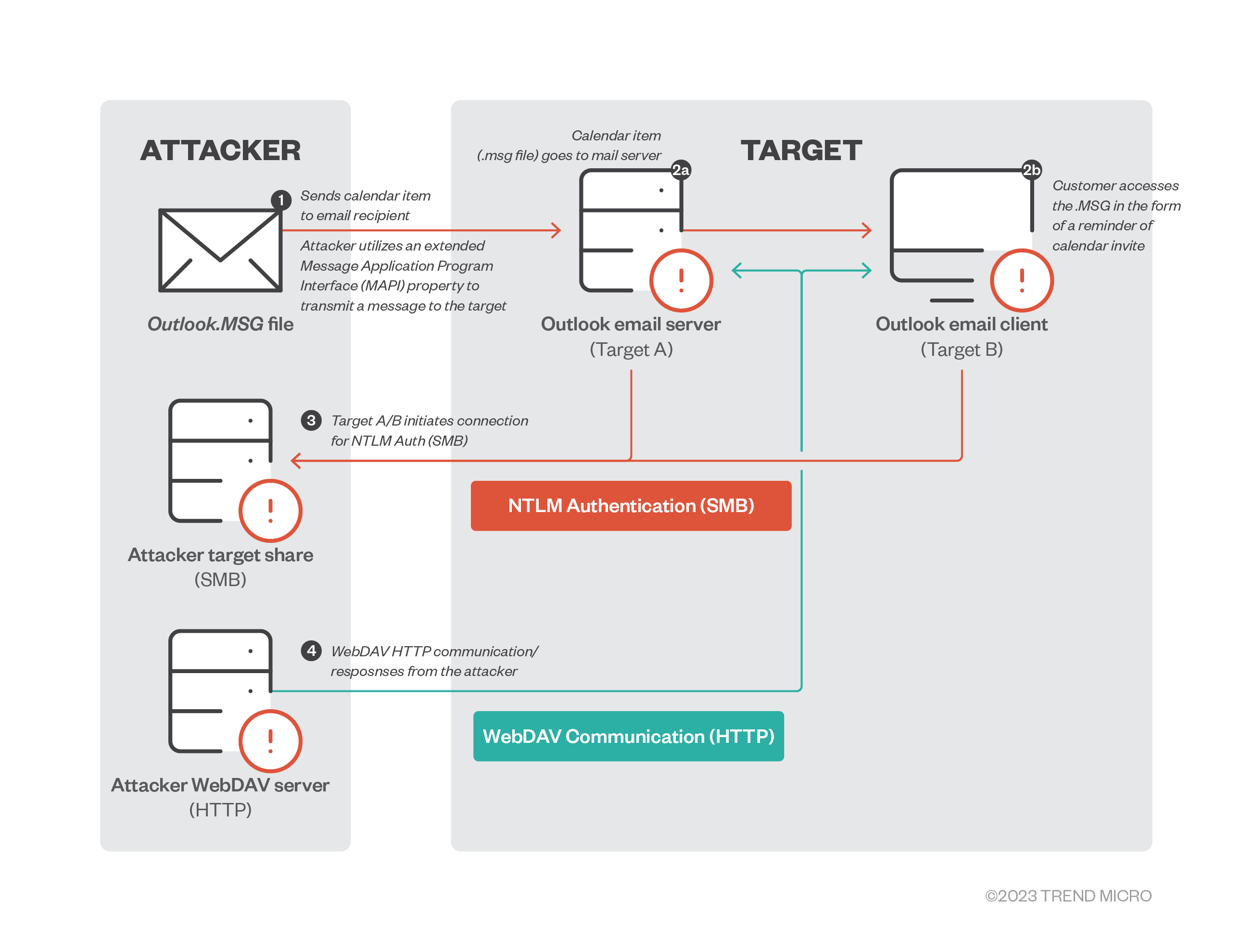
Patch CVE-2023-23397 Immediately: What You Need To Know and Do

Duo Administration - Policy & Control
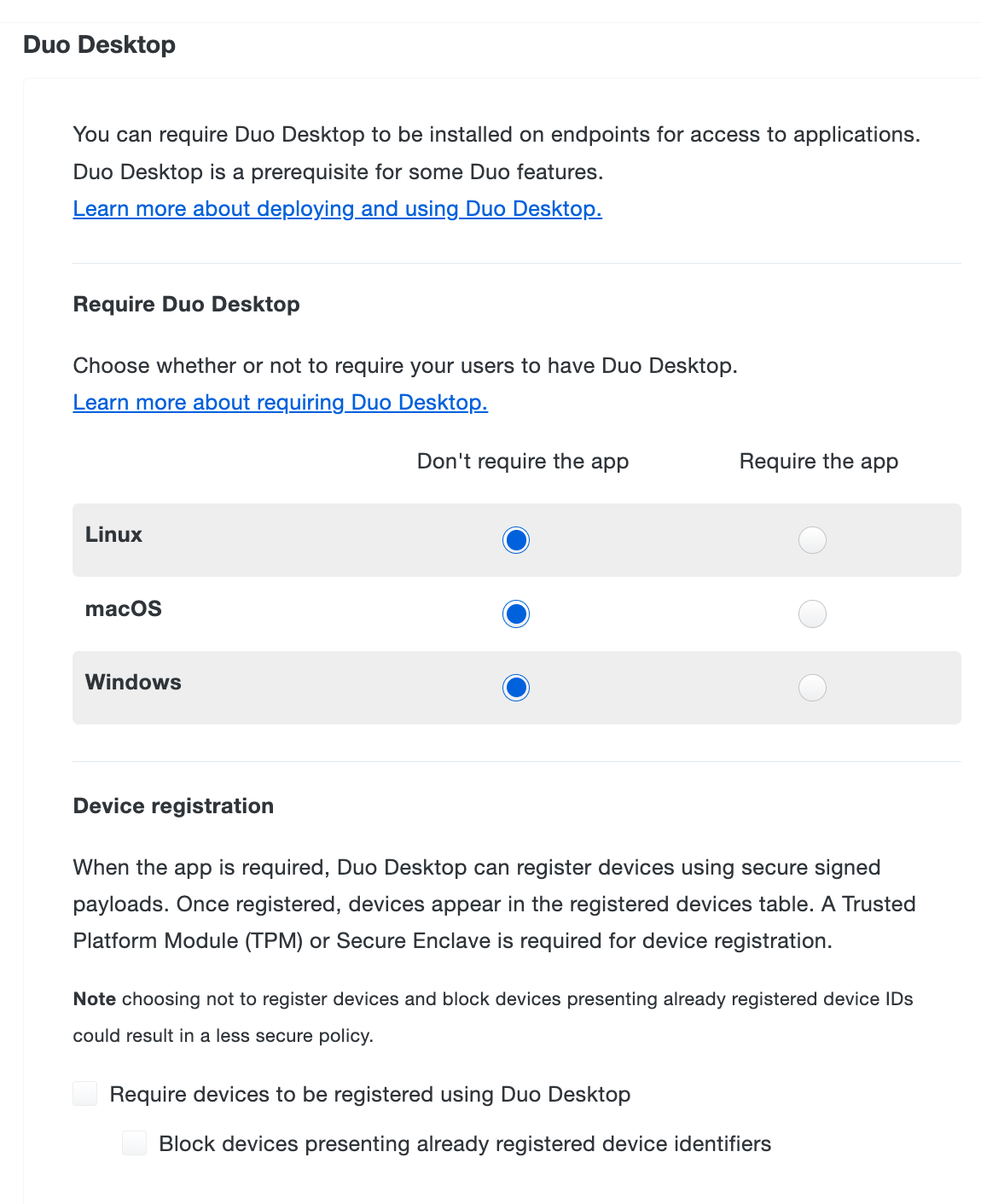
Duo Administration - Policy & Control
Recomendado para você
-
How to Log Into Facebook on Your Computer or Mobile Devices28 março 2025
-
 How to Use Facebook Login on Your Website : Social Media Examiner28 março 2025
How to Use Facebook Login on Your Website : Social Media Examiner28 março 2025 -
 How to add Facebook App Login to Your WordPress Website - UsersWP28 março 2025
How to add Facebook App Login to Your WordPress Website - UsersWP28 março 2025 -
 Facebook Login UI Clone28 março 2025
Facebook Login UI Clone28 março 2025 -
 OAuth: How Does 'Login With Facebook/Google' Work? » Science ABC28 março 2025
OAuth: How Does 'Login With Facebook/Google' Work? » Science ABC28 março 2025 -
 Inspiration Login and Signup by Facebook - UI Garage28 março 2025
Inspiration Login and Signup by Facebook - UI Garage28 março 2025 -
 Day 2 - Exploring Forms in React with a Facebook login clone - DEV Community28 março 2025
Day 2 - Exploring Forms in React with a Facebook login clone - DEV Community28 março 2025 -
 Facebook Login Screen by Dennis Bondarenko on Dribbble28 março 2025
Facebook Login Screen by Dennis Bondarenko on Dribbble28 março 2025 -
 ios - How to Display the Facebook login page when button is28 março 2025
ios - How to Display the Facebook login page when button is28 março 2025 -
 How to Create the Facebook Login Page with HTML CSS28 março 2025
How to Create the Facebook Login Page with HTML CSS28 março 2025
você pode gostar
-
 Ja-Ru Play Money - Coins and Bills (Pack of 4)28 março 2025
Ja-Ru Play Money - Coins and Bills (Pack of 4)28 março 2025 -
 Withered freddy with bonnie's withering (with face) : r28 março 2025
Withered freddy with bonnie's withering (with face) : r28 março 2025 -
 CACHORROS e GATOS engraçados brincando com OBJETOS ANIMADOS28 março 2025
CACHORROS e GATOS engraçados brincando com OBJETOS ANIMADOS28 março 2025 -
 Kamigami no Asobi InFinite, Kamigami no Asobi Wiki28 março 2025
Kamigami no Asobi InFinite, Kamigami no Asobi Wiki28 março 2025 -
 Portugal - Kawe & Ananda - Part. Especial Mikezin e Elana Dara28 março 2025
Portugal - Kawe & Ananda - Part. Especial Mikezin e Elana Dara28 março 2025 -
 Games that tolerate cheating gamble with their future28 março 2025
Games that tolerate cheating gamble with their future28 março 2025 -
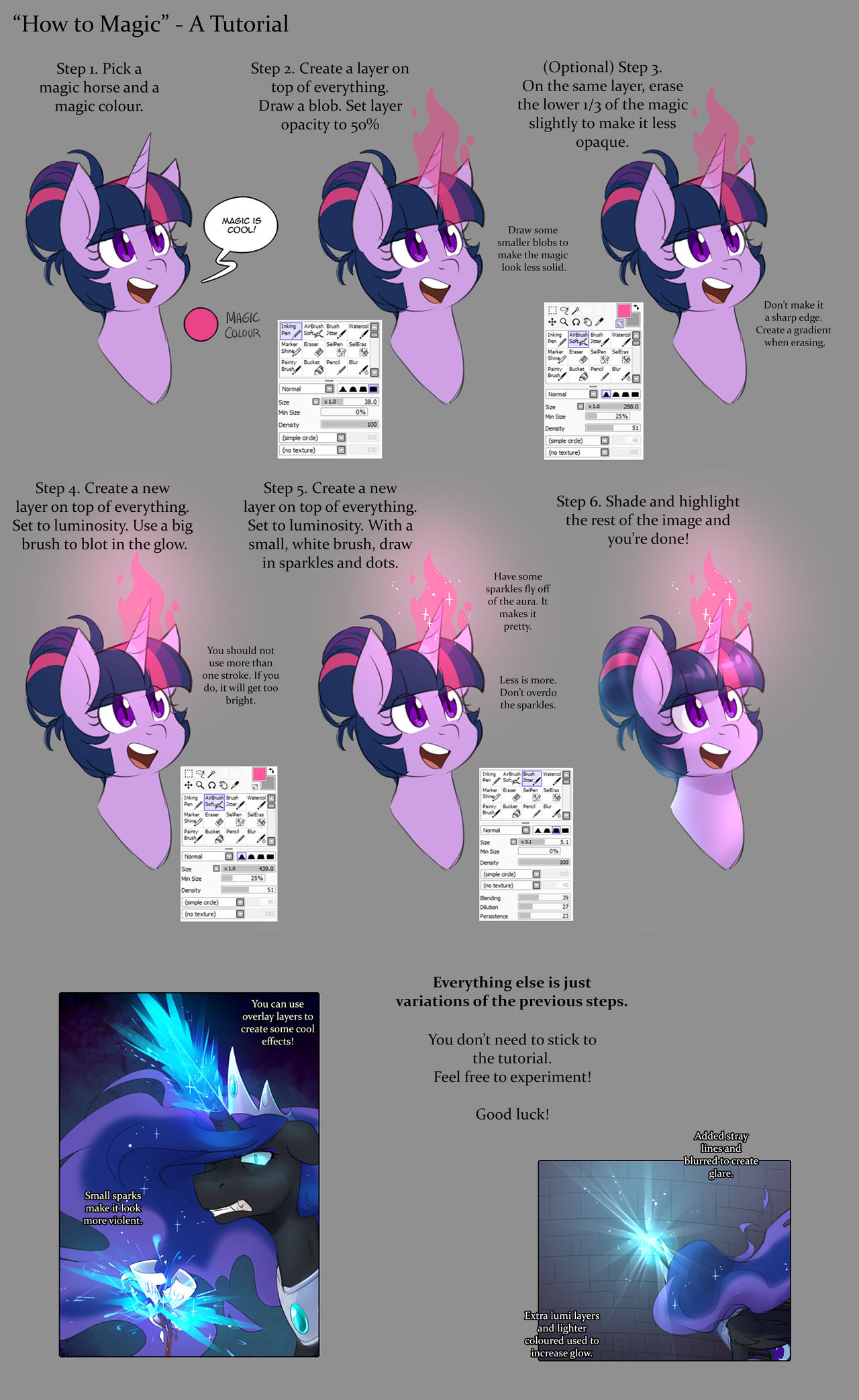 Magic Tutorial by Cosmalumi on DeviantArt28 março 2025
Magic Tutorial by Cosmalumi on DeviantArt28 março 2025 -
 Assistir Tengoku Daimakyou - Episódio - 3 animes online28 março 2025
Assistir Tengoku Daimakyou - Episódio - 3 animes online28 março 2025 -
 conjunto de bocas de desenho animado. boca aberta, língua28 março 2025
conjunto de bocas de desenho animado. boca aberta, língua28 março 2025 -
 Battlefield 4 y Titanfall gratis en Origin por tiempo limitado28 março 2025
Battlefield 4 y Titanfall gratis en Origin por tiempo limitado28 março 2025