Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 31 março 2025
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Explained: The Tinyman Hack (January 2022)

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy

Certified Information Security And Ethical Hacker

Russian APT hacked Iranian APT's infrastructure back in 2017

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Tips for Investigating Cybercrime Infrastructure

Malicious Life Podcast: Wild West Hackin' Fest

Should you use Let's Encrypt for internal hostnames? – Terence Eden's Blog

Tips for Investigating Cybercrime Infrastructure
Recomendado para você
-
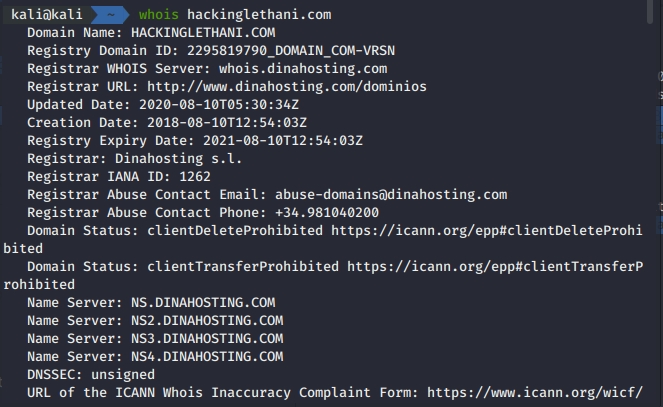
 Whois - N0C KB31 março 2025
Whois - N0C KB31 março 2025 -
 The WHOIS Database31 março 2025
The WHOIS Database31 março 2025 -
 ARIN's Whois: What Data is Public Information and How Can it be31 março 2025
ARIN's Whois: What Data is Public Information and How Can it be31 março 2025 -
WHOIS/Domain Expiry Check Basics – Uptime.com31 março 2025
-
 Whois Lookup - Domain Research and Availablity Tool31 março 2025
Whois Lookup - Domain Research and Availablity Tool31 março 2025 -
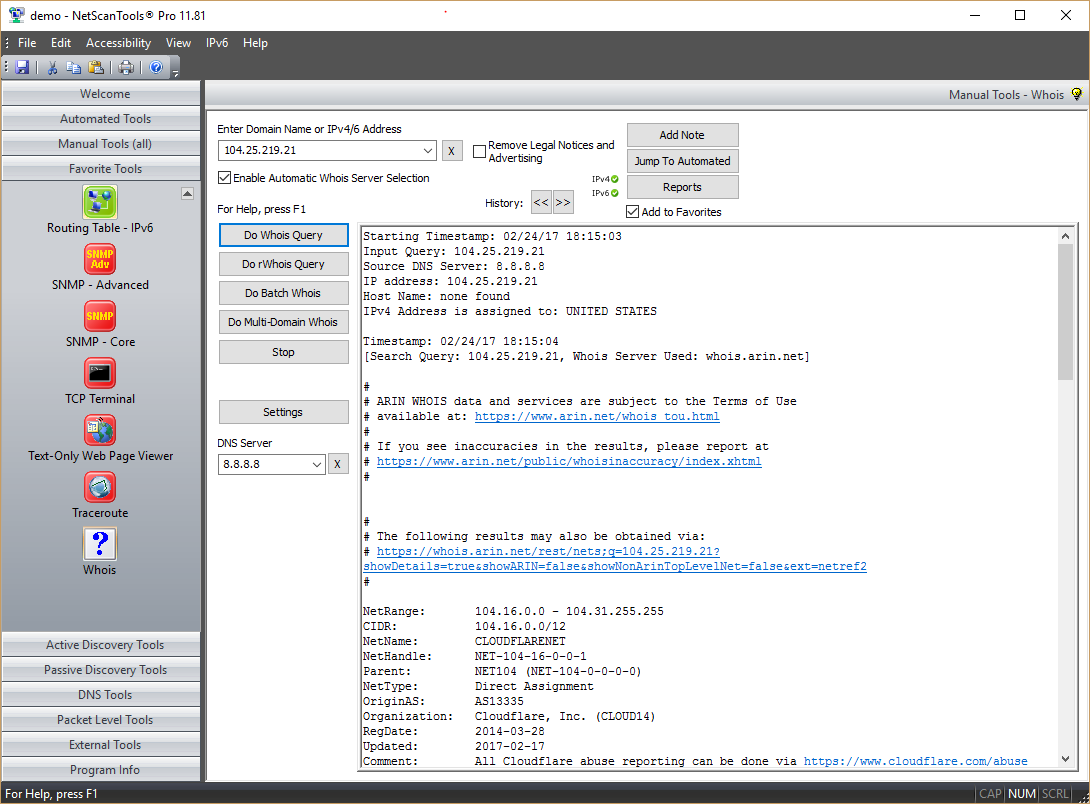 Whois Tool in NetScanTools Pro31 março 2025
Whois Tool in NetScanTools Pro31 março 2025 -
 File:Whois Mushoku Tensei screenshot.png - Wikipedia31 março 2025
File:Whois Mushoku Tensei screenshot.png - Wikipedia31 março 2025 -
 State/province and country/region in WHOIS - Registrar - Cloudflare Community31 março 2025
State/province and country/region in WHOIS - Registrar - Cloudflare Community31 março 2025 -
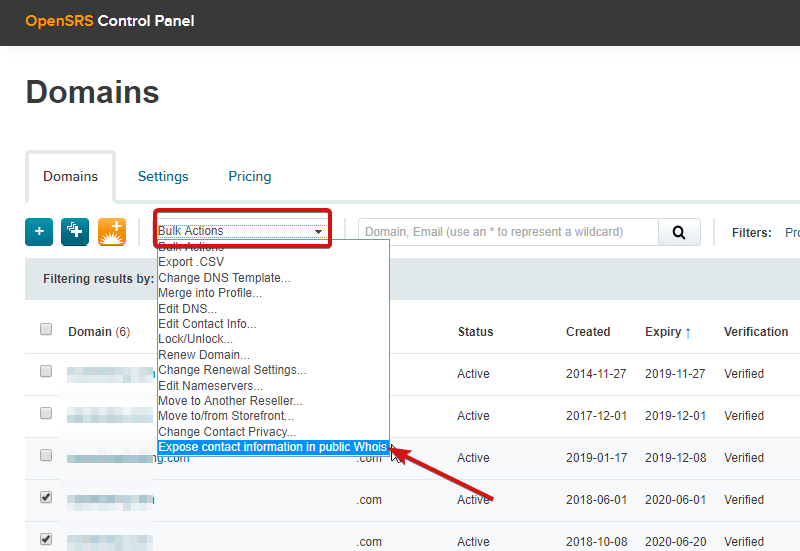 Public Whois - Exposing contact information – OpenSRS Help & Support31 março 2025
Public Whois - Exposing contact information – OpenSRS Help & Support31 março 2025 -
 Prefix WhoIs - Wikipedia31 março 2025
Prefix WhoIs - Wikipedia31 março 2025
você pode gostar
-
 Wednesday Addams Inspired Halloween Costume Ideas31 março 2025
Wednesday Addams Inspired Halloween Costume Ideas31 março 2025 -
 Classic Sport 2-in-1 Billiard Rack 8/9-Ball, Triangle/Diamond31 março 2025
Classic Sport 2-in-1 Billiard Rack 8/9-Ball, Triangle/Diamond31 março 2025 -
/cdn.vox-cdn.com/uploads/chorus_image/image/72051009/1438843136.0.jpg) Scream 6 Rotten Tomatoes score: Rating, reviews for latest Scream movie - DraftKings Network31 março 2025
Scream 6 Rotten Tomatoes score: Rating, reviews for latest Scream movie - DraftKings Network31 março 2025 -
 Playstation 3 Ps3 Super Slim + 45 Jogos + Fifa 19 + Gta531 março 2025
Playstation 3 Ps3 Super Slim + 45 Jogos + Fifa 19 + Gta531 março 2025 -
.jpg) RIKARDO.MUSIC - BLOG DE EURODANCE : A GRAVADORA PARADOXX MUSIC E O31 março 2025
RIKARDO.MUSIC - BLOG DE EURODANCE : A GRAVADORA PARADOXX MUSIC E O31 março 2025 -
 Skip and Loafer Chapter 55 Release Date, Spoilers & Where To Read? - Sportslumo31 março 2025
Skip and Loafer Chapter 55 Release Date, Spoilers & Where To Read? - Sportslumo31 março 2025 -
 Framery O The original soundproof office phone booth31 março 2025
Framery O The original soundproof office phone booth31 março 2025 -
 React jujutsu kaisen temporada 2 ep 2 (dublado)31 março 2025
React jujutsu kaisen temporada 2 ep 2 (dublado)31 março 2025 -
![Episode 11 - Mashle: Magic and Muscles [2023-06-24] - Anime News Network](https://cdn.animenewsnetwork.com/thumbnails/max300x600/cms/episode-review.4/199574/mashle111.jpg) Episode 11 - Mashle: Magic and Muscles [2023-06-24] - Anime News Network31 março 2025
Episode 11 - Mashle: Magic and Muscles [2023-06-24] - Anime News Network31 março 2025 -
 Thisisgame Thailand :: เปิดโผคะแนนรีวิว Sonic Frontiers จาก Metacritic31 março 2025
Thisisgame Thailand :: เปิดโผคะแนนรีวิว Sonic Frontiers จาก Metacritic31 março 2025