Cryptojacking: Understanding and defending against cloud compute
Por um escritor misterioso
Last updated 28 março 2025

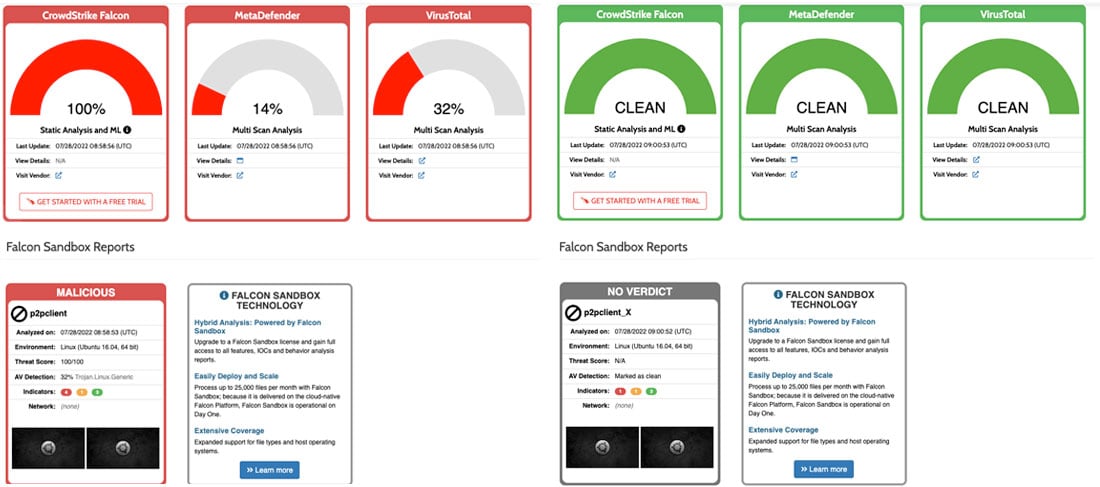
Threat Alert: Cloud Network Bandwidth Now Stolen through Cryptojacking
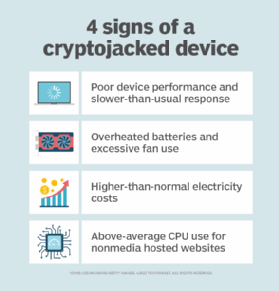
What is Cryptojacking? Detection and Preventions Techniques
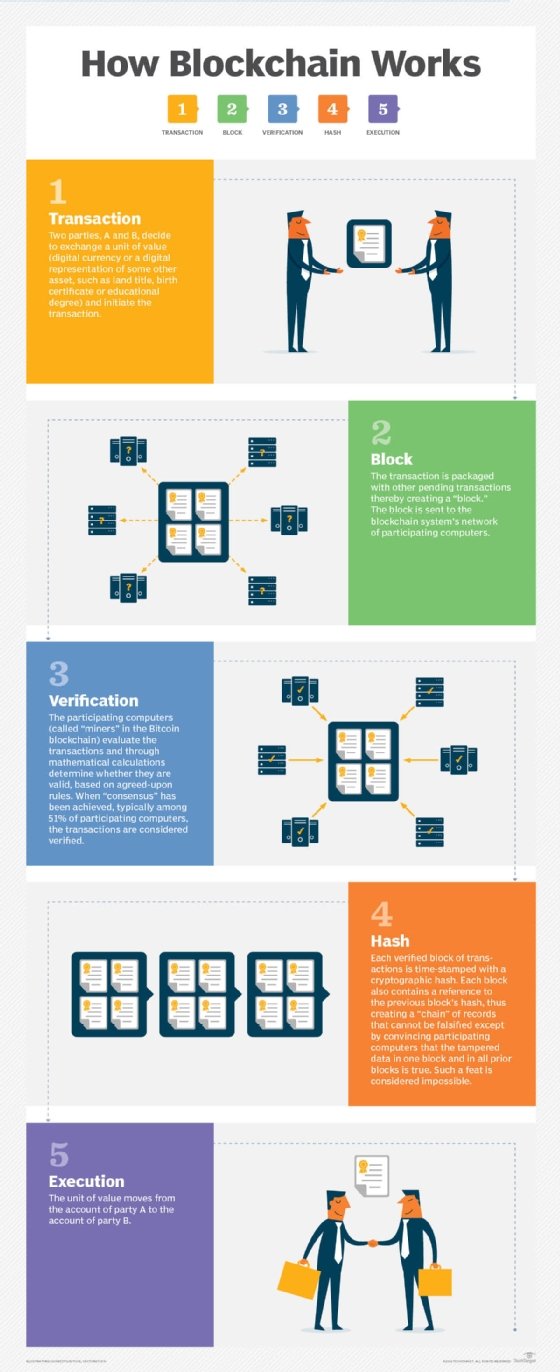
What is Cryptojacking? Detection and Preventions Techniques
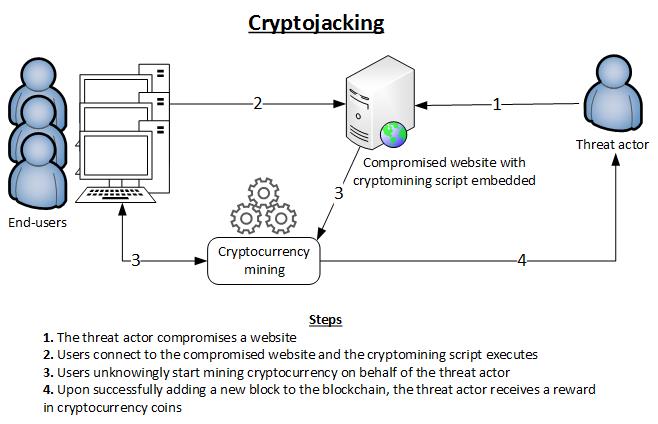
Cryptojacking: What is it And What You Need to Know in 2023

Cryptojacking: Understanding and defending against cloud compute

How crypto miners hijack AWS accounts (Cryptojacking GUI-Vil Case

Digital Piracy: Understanding the Threat of Cryptojacking
How to Monitor for Cryptomining in the Cloud

Delay-CJ: A novel cryptojacking covert attack method based on

The SecureMac Guide to Understanding Cryptocurrency and Cryptojacking

What is Cryptojacking? Definition, Detection, Prevention
Recomendado para você
-
 Sudden Attack 2 Game Review28 março 2025
Sudden Attack 2 Game Review28 março 2025 -
 Cardiac Arrest vs Heart Attack Infographic American Heart Association CPR & First Aid28 março 2025
Cardiac Arrest vs Heart Attack Infographic American Heart Association CPR & First Aid28 março 2025 -
 Oil Prices Surge Amidst Hamas Attack: Global Energy Alert28 março 2025
Oil Prices Surge Amidst Hamas Attack: Global Energy Alert28 março 2025 -
 Kwon Eunbi & Kang Hyewon for Sudden Attack 202328 março 2025
Kwon Eunbi & Kang Hyewon for Sudden Attack 202328 março 2025 -
Malmstrom reigns with fifth back-to-back win in 2023 Global Strike28 março 2025
-
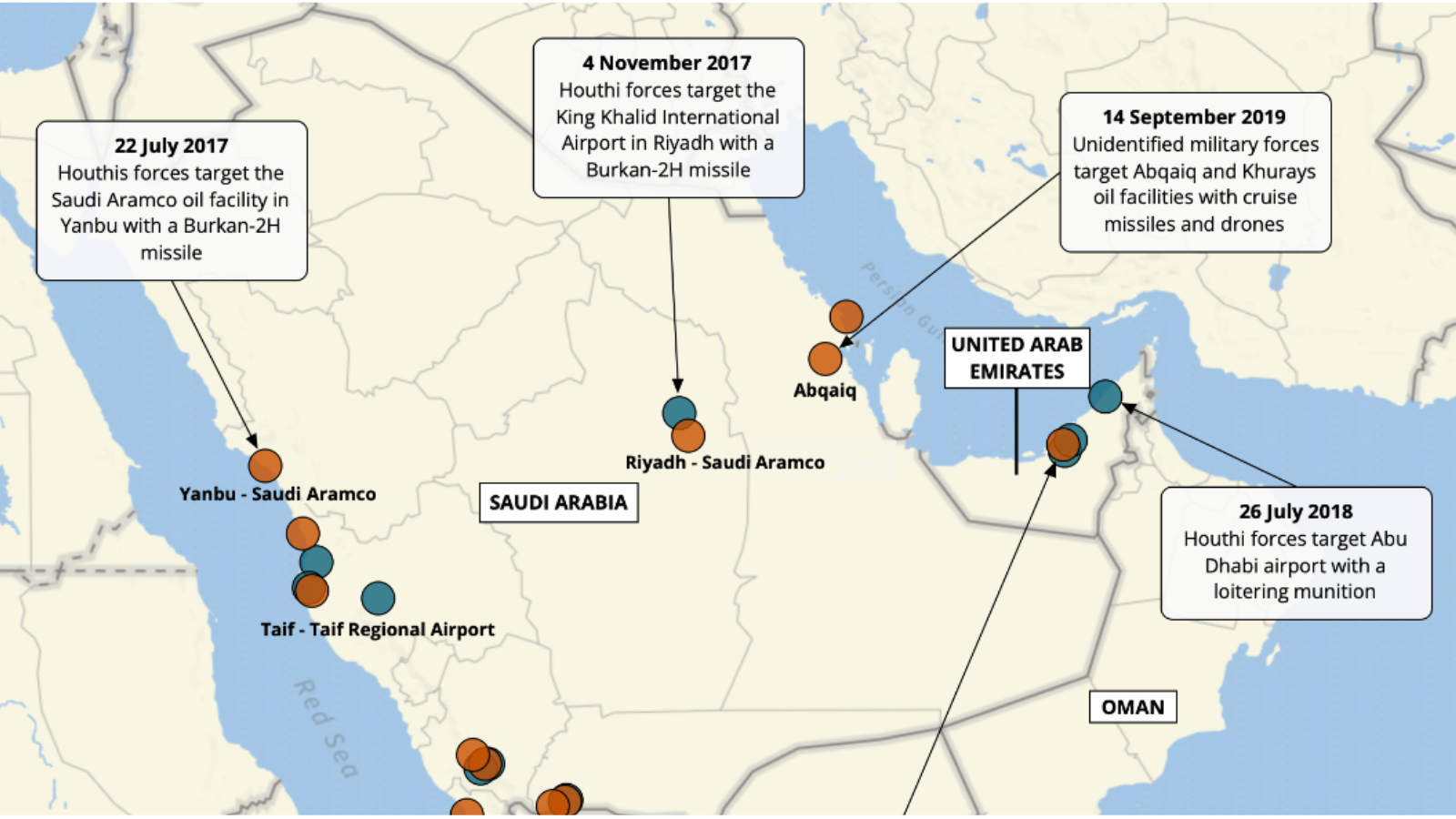 Beyond Riyadh: Houthi Cross-Border Aerial Warfare (2015-2022)28 março 2025
Beyond Riyadh: Houthi Cross-Border Aerial Warfare (2015-2022)28 março 2025 -
 لعبه سدن اتاك تعود من جديد تحميل اللعبه 202328 março 2025
لعبه سدن اتاك تعود من جديد تحميل اللعبه 202328 março 2025 -
 SUDDEN ATTACK 2023 - 4FUN NA MADRUGA!!!28 março 2025
SUDDEN ATTACK 2023 - 4FUN NA MADRUGA!!!28 março 2025 -
 7 Reasons Global Attacks Will Rise Significantly in 202328 março 2025
7 Reasons Global Attacks Will Rise Significantly in 202328 março 2025 -
 Surge of Middle East Attacks Left 21 Troops Injured, Most with28 março 2025
Surge of Middle East Attacks Left 21 Troops Injured, Most with28 março 2025
você pode gostar
-
 Over Rev! - Wikipedia28 março 2025
Over Rev! - Wikipedia28 março 2025 -
motivacional #reflexão #ansiedade #ansiedadetemcura28 março 2025
-
Jogo Rally Champions PS2 ( Corrida ) Play 228 março 2025
-
 Vintage Diable Au Corps Perfume by Donatella Pecci Blunt 1.7 - Israel28 março 2025
Vintage Diable Au Corps Perfume by Donatella Pecci Blunt 1.7 - Israel28 março 2025 -
 PinPics Free Disney Pin Trading Database28 março 2025
PinPics Free Disney Pin Trading Database28 março 2025 -
 Eevee Gets Another Evolution For Pokemon X and Pokemon Y - Cheat Code Central28 março 2025
Eevee Gets Another Evolution For Pokemon X and Pokemon Y - Cheat Code Central28 março 2025 -
IMDb - Big Evil Dead fan? Comment below with your best Ash one-liner for a chance to win tickets to the Ash vs Evil Dead premiere! #AshBash UPDATE: Congratulations to our28 março 2025
-
omega flowey APK (Android Game) - Free Download28 março 2025
-
 Elizabeth 1 (Bioshock Infinite) by KanzassArt on Newgrounds28 março 2025
Elizabeth 1 (Bioshock Infinite) by KanzassArt on Newgrounds28 março 2025 -
 Chaturanga Pose Tutorial - Power Yoga - Power Yoga Online28 março 2025
Chaturanga Pose Tutorial - Power Yoga - Power Yoga Online28 março 2025



