Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Last updated 04 abril 2025
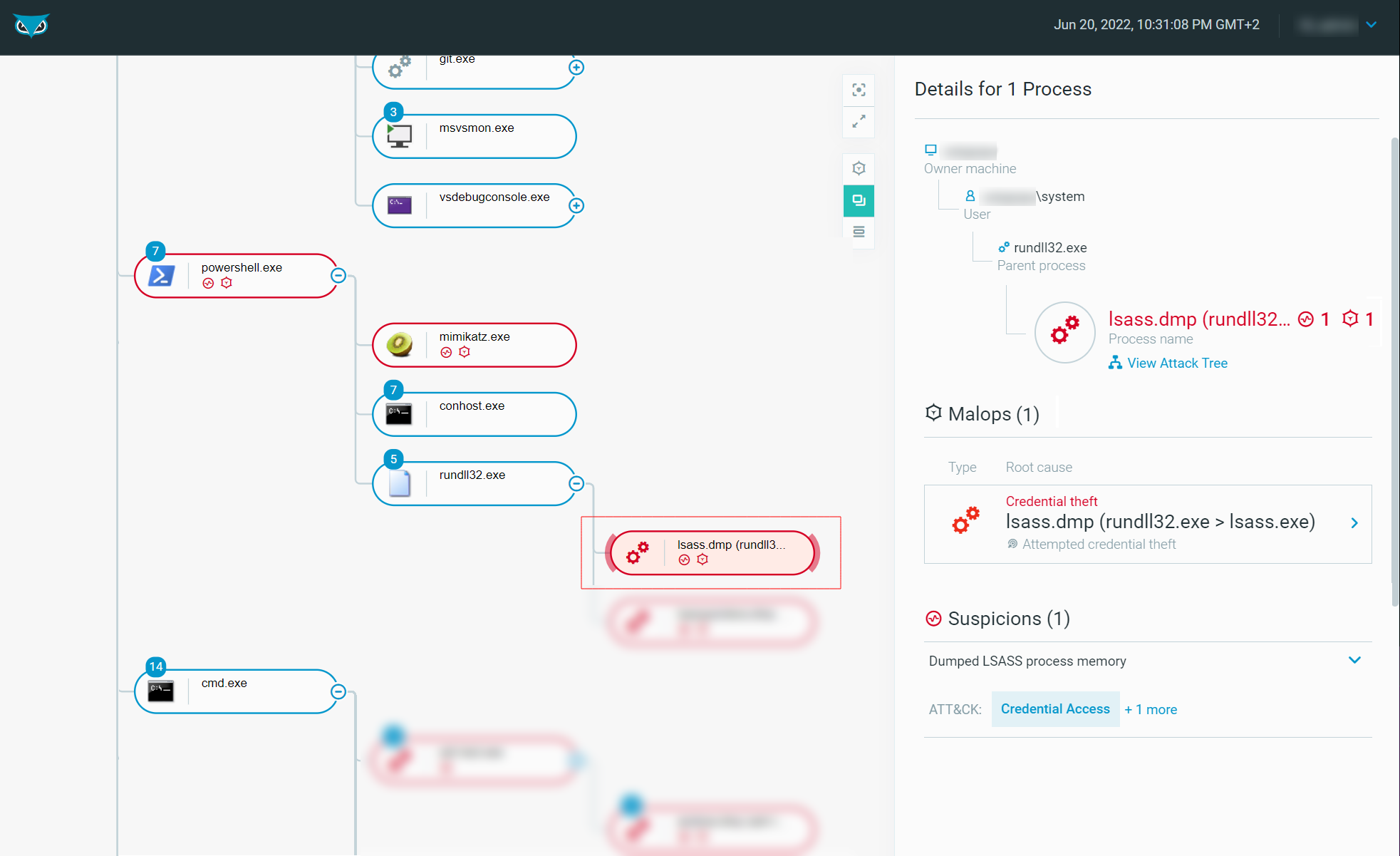
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail
Rundll32: The Infamous Proxy for Executing Malicious Code

A Survey on the Evolution of Fileless Attacks and Detection Techniques - ScienceDirect
Rundll32: The Infamous Proxy for Executing Malicious Code

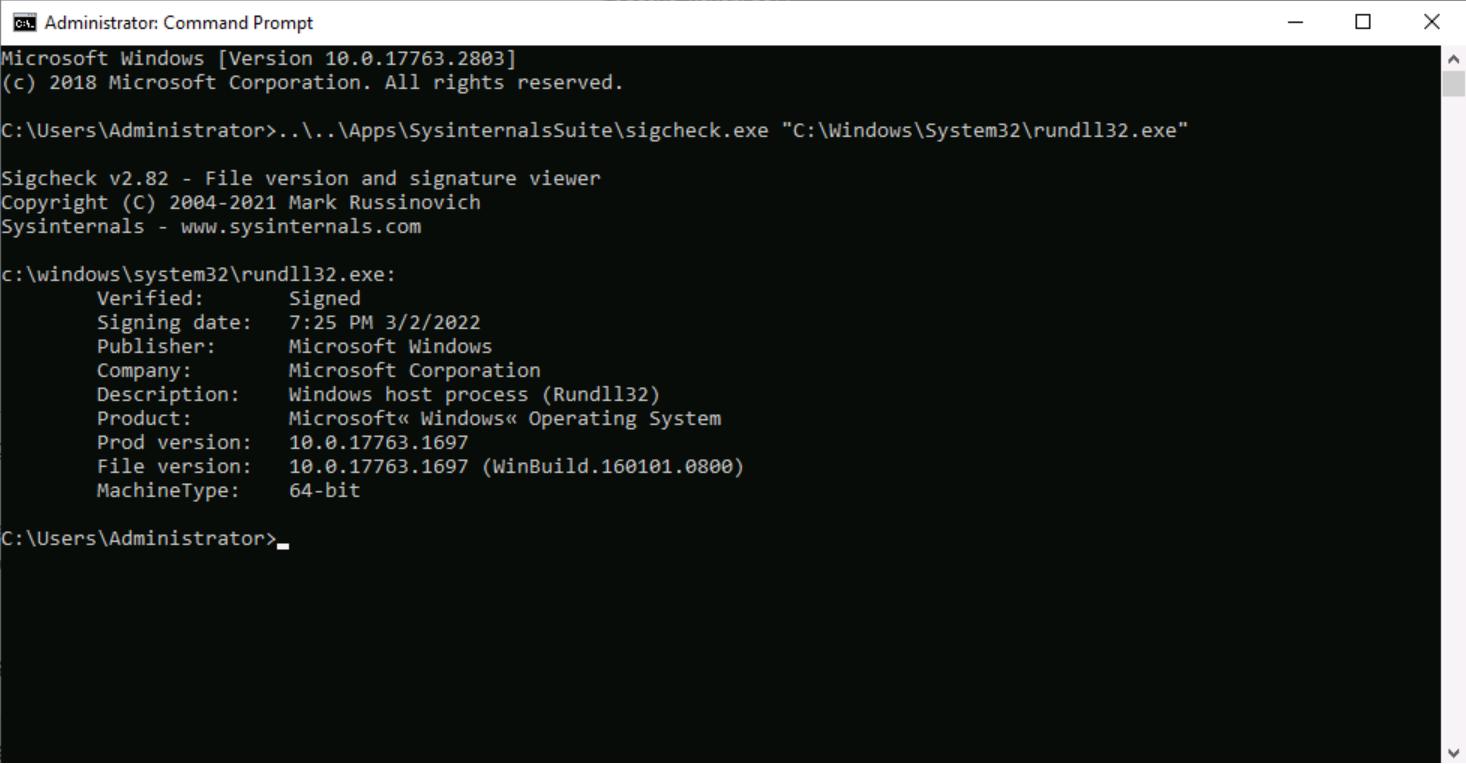
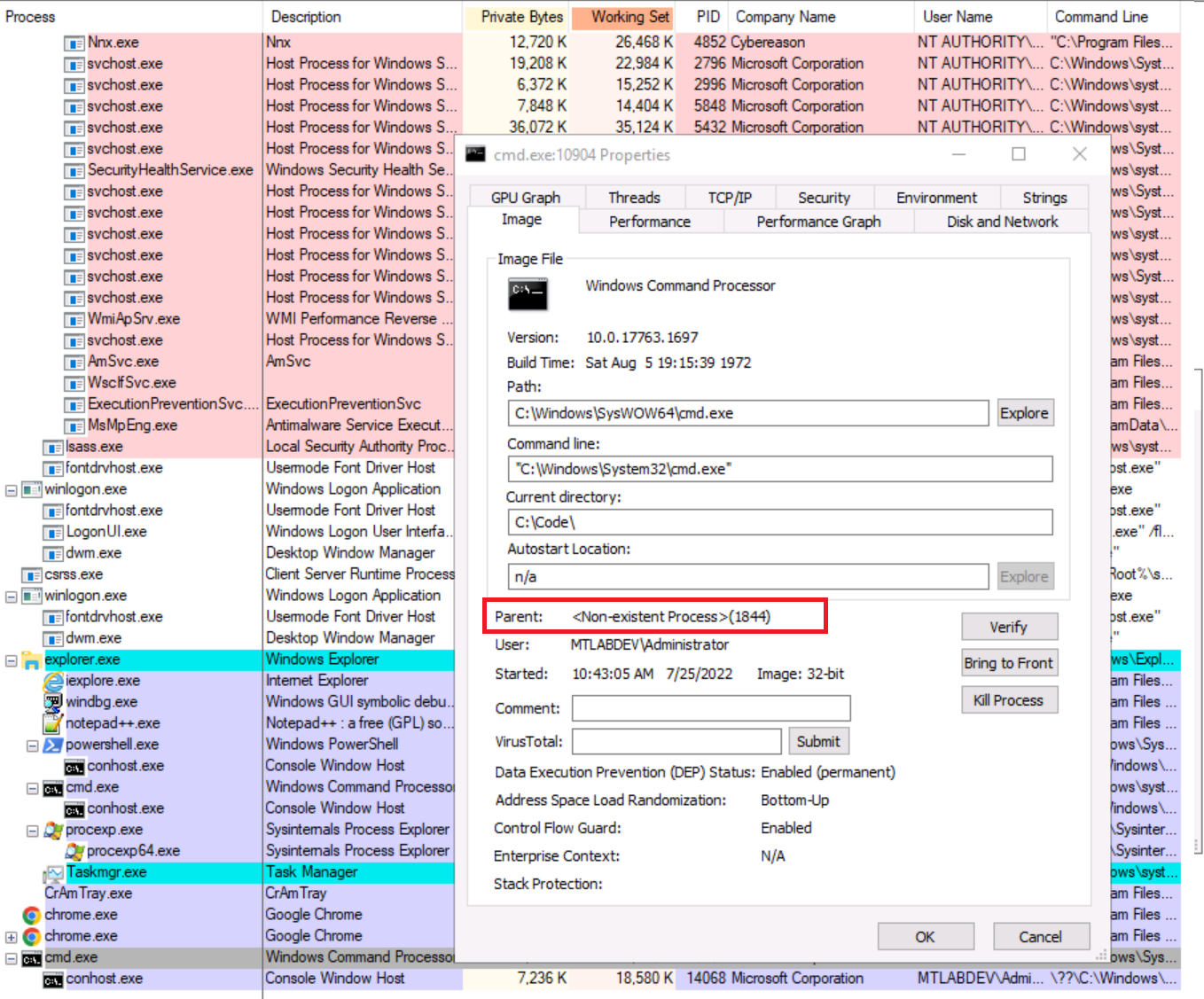
The second program that was found is rundll32exe which is a Microsoft signed

Microsoft experts linked Raspberry Robin malware to Evil Corp
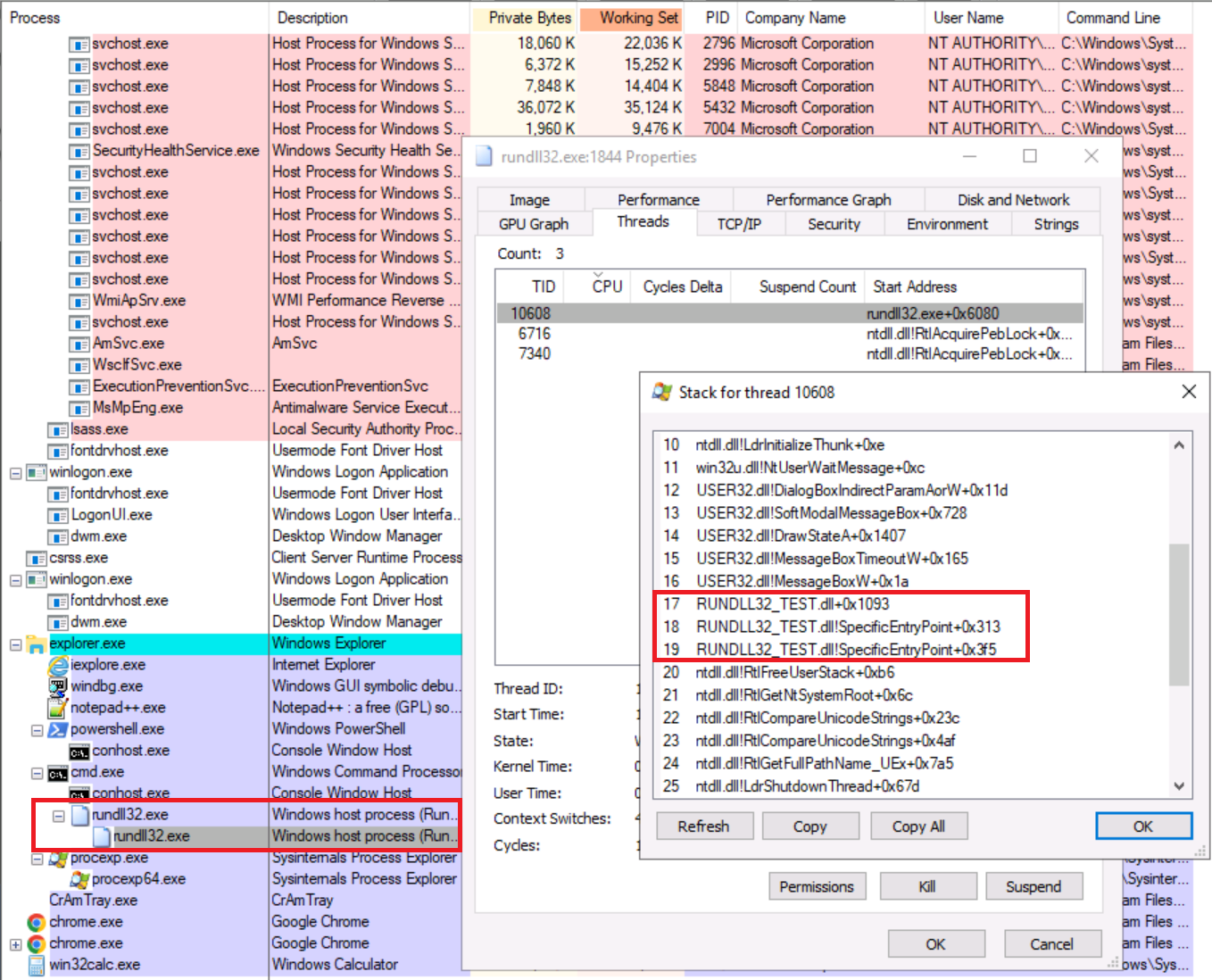
Rundll32: The Infamous Proxy for Executing Malicious Code
APT Profile: Sandworm - SOCRadar® Cyber Intelligence Inc.

Detecting IcedID: The Latest Campaign Against Ukrainian Government Bodies - SOC Prime

Virus Bulletin on X: The Cybereason Blue Team describe how Microsoft's rundll32.exe tool, which allows code to be loaded and executed, is often used by adversaries during their offensive operations. /
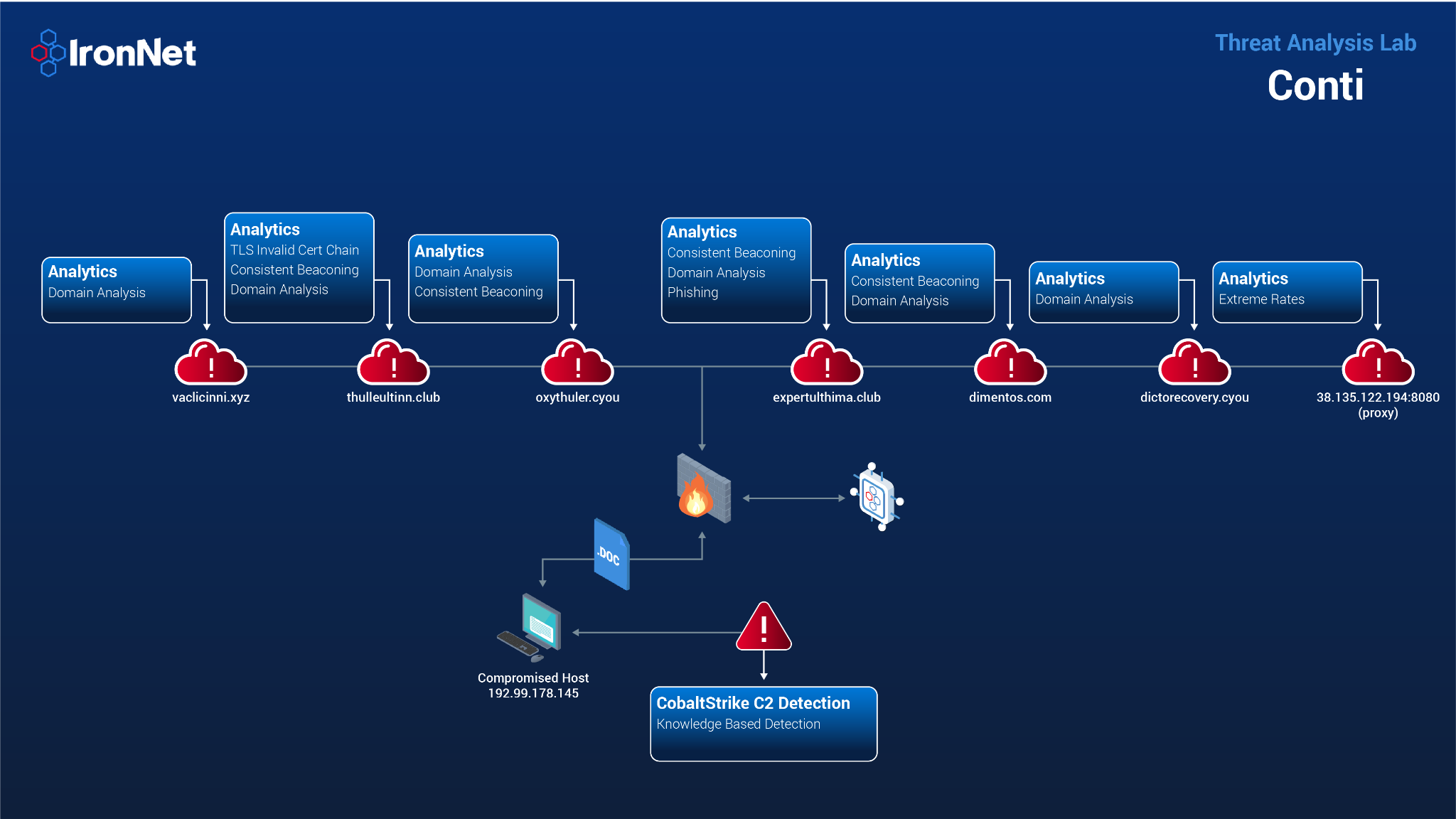
How IronNet's Behavioral Analytics Detect REvil and Conti Ransomware

Microsoft experts linked Raspberry Robin malware to Evil Corp
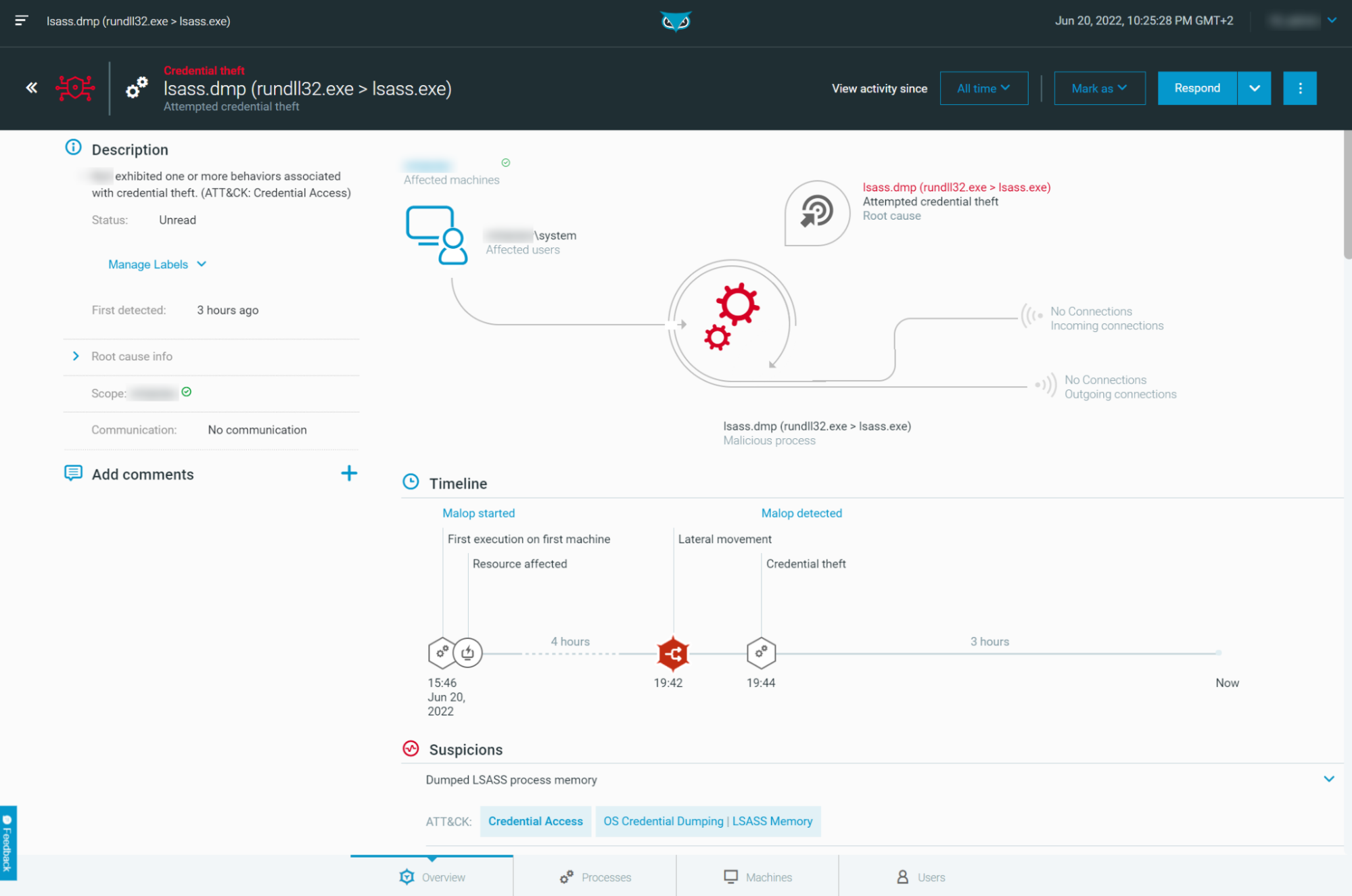
Rundll32: The Infamous Proxy for Executing Malicious Code
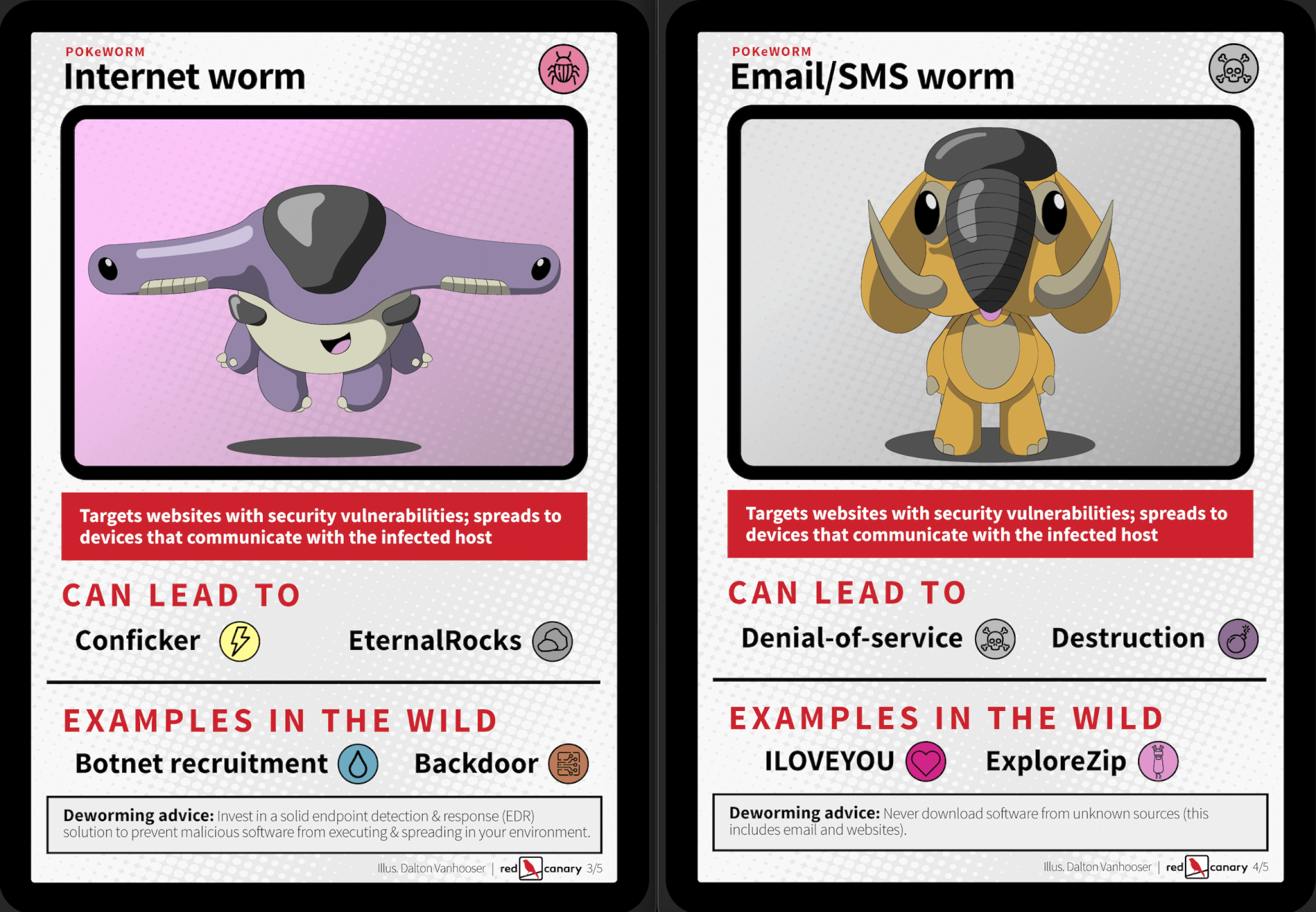
Persistent pests: A taxonomy of computer worms - Red Canary
Recomendado para você
-
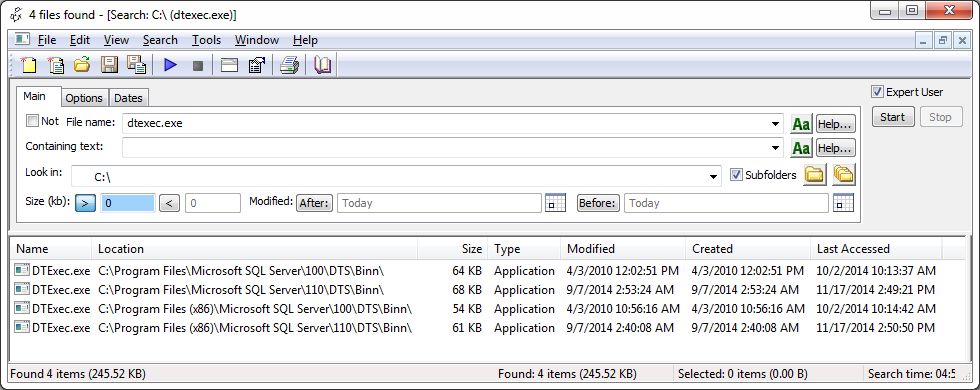 How to execute an SSIS package from the command line or a batch file – SQLServerCentral04 abril 2025
How to execute an SSIS package from the command line or a batch file – SQLServerCentral04 abril 2025 -
 User Guide for Command Line Arguments in Windows – Computer Chum04 abril 2025
User Guide for Command Line Arguments in Windows – Computer Chum04 abril 2025 -
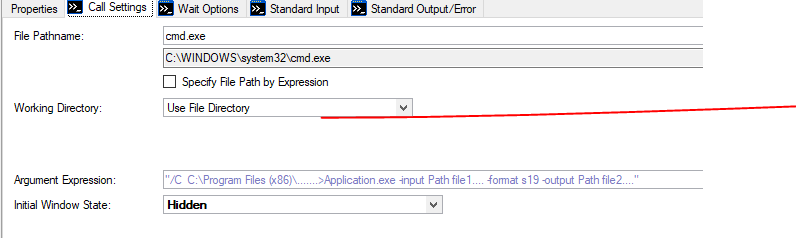
Passing arguments to exe using the Argument Expression - NI Community04 abril 2025
-
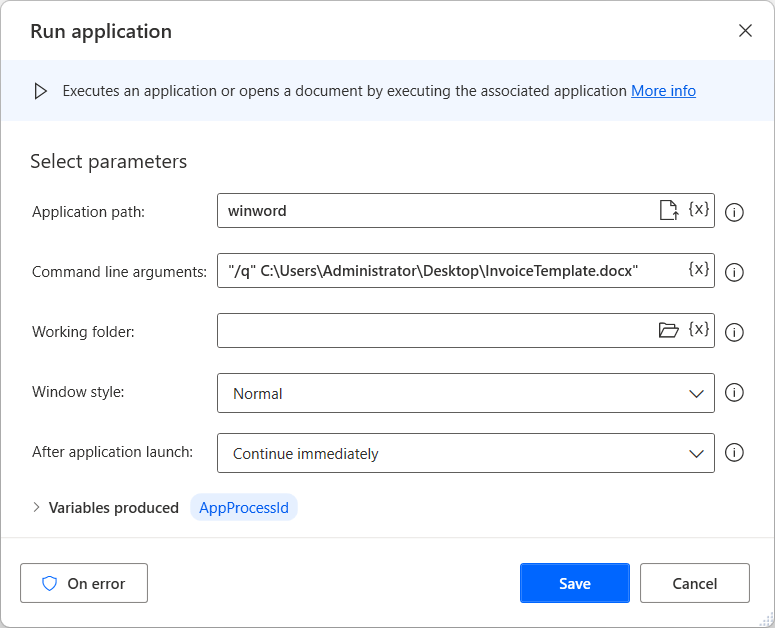 System actions reference - Power Automate04 abril 2025
System actions reference - Power Automate04 abril 2025 -
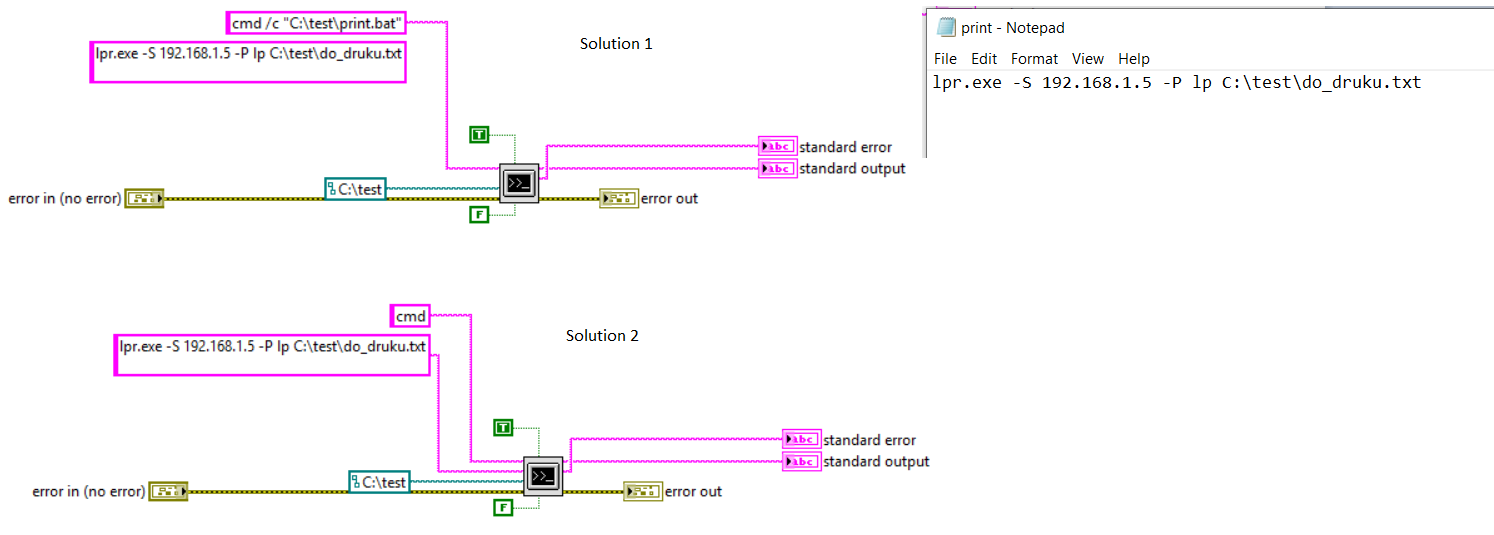 System Exec - not possible to recognize program or batch file04 abril 2025
System Exec - not possible to recognize program or batch file04 abril 2025 -
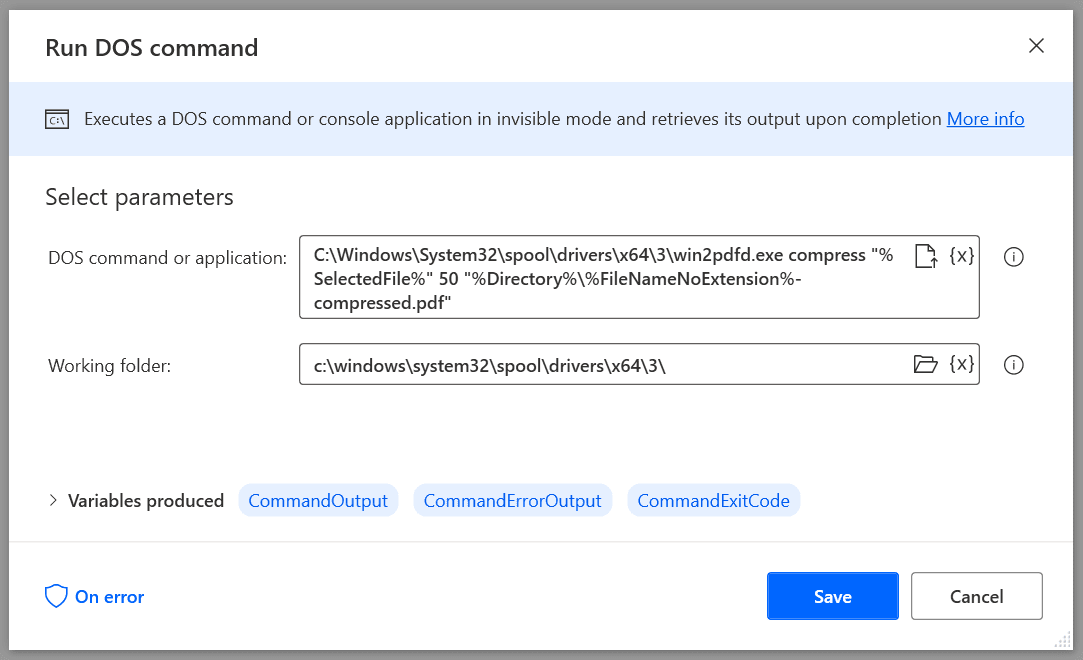 How To Use The Win2PDF Command Line With Power Automate Desktop04 abril 2025
How To Use The Win2PDF Command Line With Power Automate Desktop04 abril 2025 -
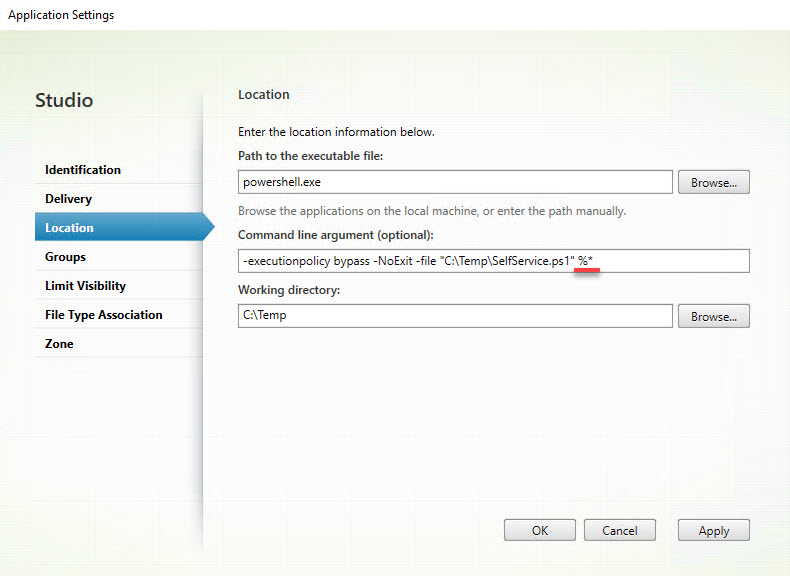 Parsing multiple parameters using the Citrix SelfService.exe04 abril 2025
Parsing multiple parameters using the Citrix SelfService.exe04 abril 2025 -
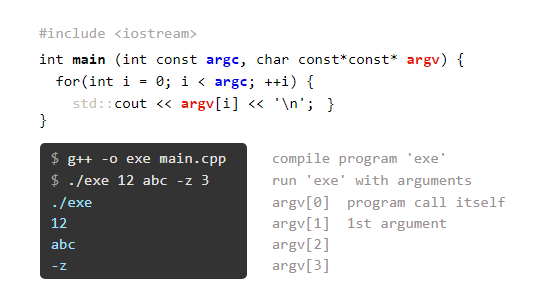 C++ Command Line Argument Processing04 abril 2025
C++ Command Line Argument Processing04 abril 2025 -
 Launching Deploy-Application via PSEXEC using ServiceUI with04 abril 2025
Launching Deploy-Application via PSEXEC using ServiceUI with04 abril 2025 -
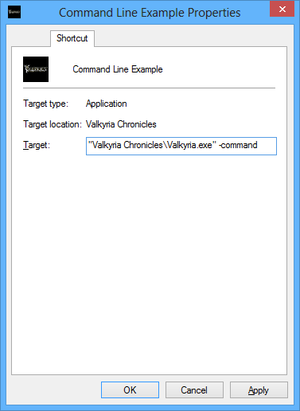 Glossary:Command line arguments - PCGamingWiki PCGW - bugs, fixes04 abril 2025
Glossary:Command line arguments - PCGamingWiki PCGW - bugs, fixes04 abril 2025
você pode gostar
-
 SCP-055 Interpretations. : r/SCP04 abril 2025
SCP-055 Interpretations. : r/SCP04 abril 2025 -
 What Does The Image Of A Plane With Red Dots On It Mean? The04 abril 2025
What Does The Image Of A Plane With Red Dots On It Mean? The04 abril 2025 -
 Shadowrun bundle lets you get started with the classic science04 abril 2025
Shadowrun bundle lets you get started with the classic science04 abril 2025 -
 Kalos, Where Dreams and Adventures Begin [FULL EPISODE04 abril 2025
Kalos, Where Dreams and Adventures Begin [FULL EPISODE04 abril 2025 -
 Characters appearing in Call of the Night Anime04 abril 2025
Characters appearing in Call of the Night Anime04 abril 2025 -
 Roblox Series 2 Boost Vector: Buster Deluxe Mystery Pack04 abril 2025
Roblox Series 2 Boost Vector: Buster Deluxe Mystery Pack04 abril 2025 -
 Friends kijken in Nederland en het buitenland04 abril 2025
Friends kijken in Nederland en het buitenland04 abril 2025 -
 Smart Islands: Boosting connectivity to unlock Pacific potential - ITU Hub04 abril 2025
Smart Islands: Boosting connectivity to unlock Pacific potential - ITU Hub04 abril 2025 -
 Active_Developer_Badge - Discord Emoji04 abril 2025
Active_Developer_Badge - Discord Emoji04 abril 2025 -
 El estado de BFV : r/BattlefieldV04 abril 2025
El estado de BFV : r/BattlefieldV04 abril 2025