Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 02 abril 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
FireEye Portfolio

It is Time to Take Action - How to Defend Against FireEye's Red

BOLO - Be On The Lookout: FireEye Red Team Tools Stolen in Nation
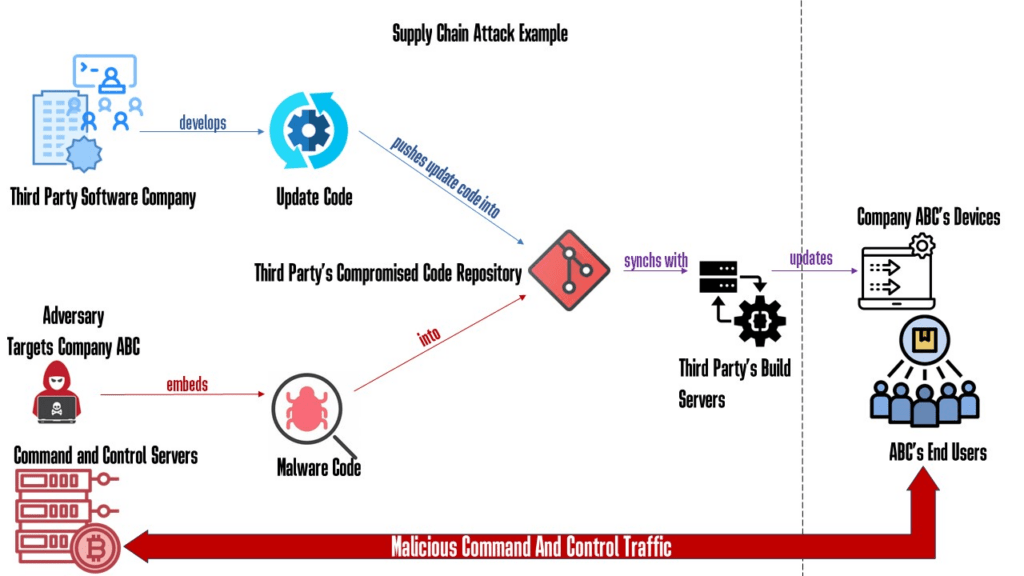
Why Red Teaming Should Be In A Supply Chain Defense Strategy
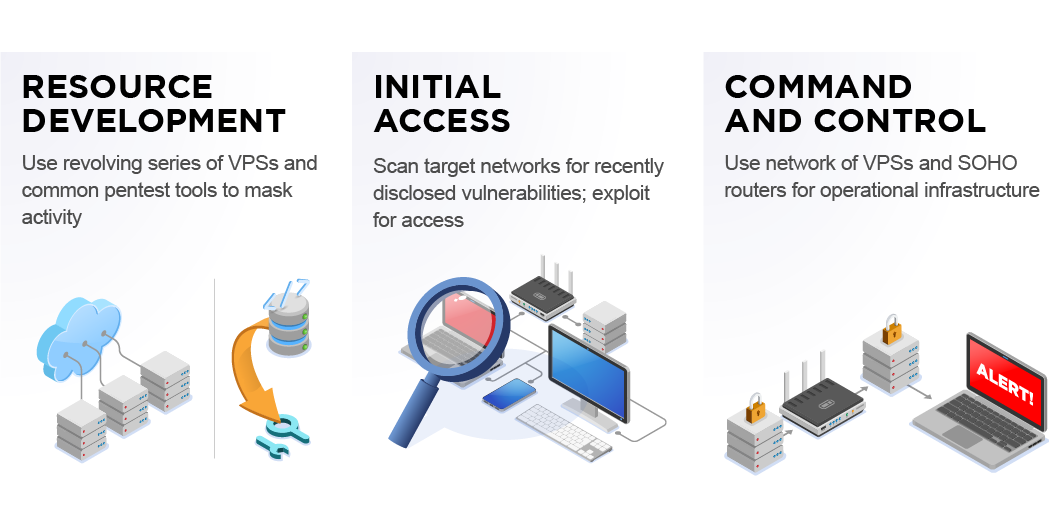
Chinese State-Sponsored Cyber Operations: Observed TTPs

Tactics, Techniques and Procedures of FireEye Red Team Tools

Try Hack Me Red Team Threat Intel

FireEye Reveals How SolarWinds Hackers Bypassed the Defenses
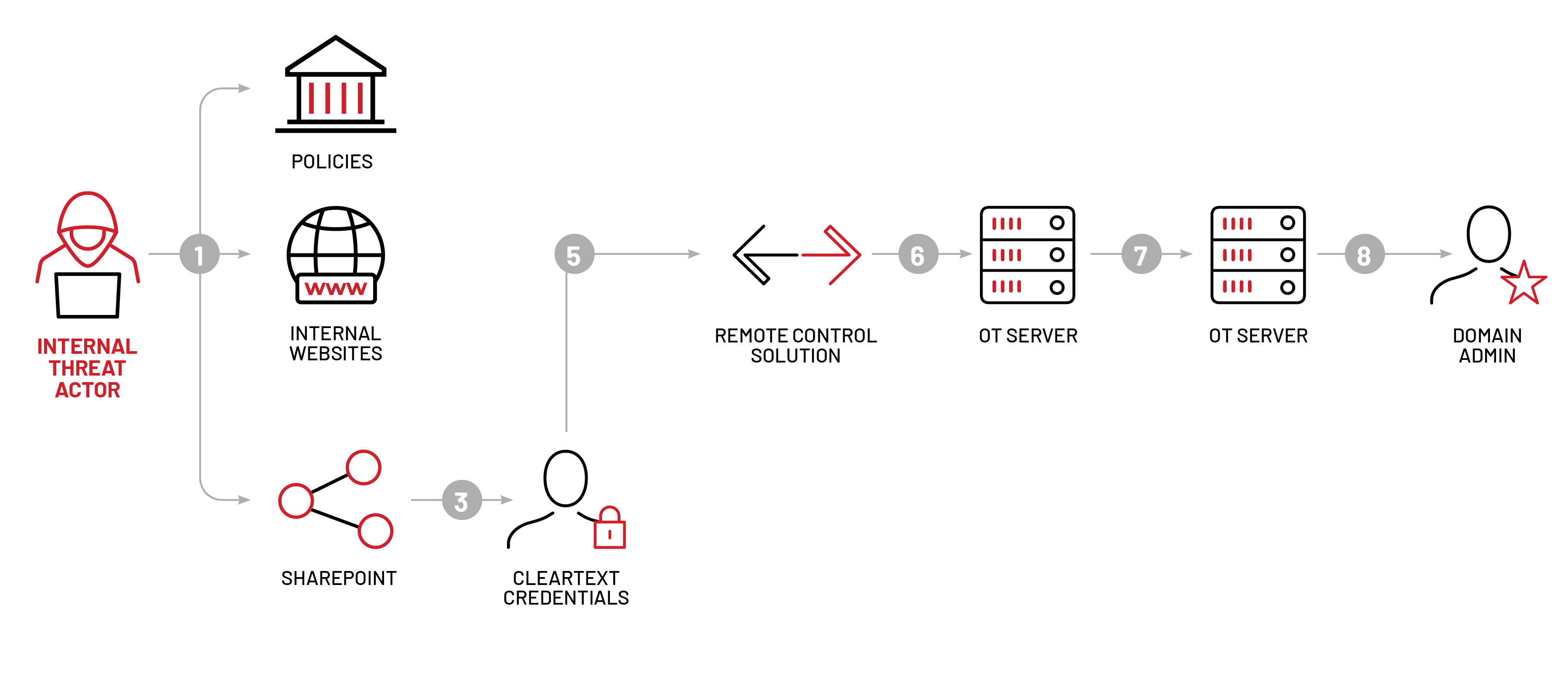
Mandiant Red Team Emulates FIN11 Tactics To Control Operational

Long Term Analysis Illustrates How Risk Posed by a Vulnerability

Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Recomendado para você
-
 What is Spoofing? - FFCCU Blog02 abril 2025
What is Spoofing? - FFCCU Blog02 abril 2025 -
 How to hack a car — a quick crash-course02 abril 2025
How to hack a car — a quick crash-course02 abril 2025 -
 Beware of Spoof Websites - RCB Bank02 abril 2025
Beware of Spoof Websites - RCB Bank02 abril 2025 -
 elmoCut - Clean UI ARP spoofer for Windows : r/Python02 abril 2025
elmoCut - Clean UI ARP spoofer for Windows : r/Python02 abril 2025 -
 Device Fingerprinting - SEON Docs02 abril 2025
Device Fingerprinting - SEON Docs02 abril 2025 -
 1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for02 abril 2025
1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for02 abril 2025 -
 Telnet Networks - Managing Network Performance - Telnet Network02 abril 2025
Telnet Networks - Managing Network Performance - Telnet Network02 abril 2025 -
 Autonomous aerial robotics for package delivery: A technical02 abril 2025
Autonomous aerial robotics for package delivery: A technical02 abril 2025 -
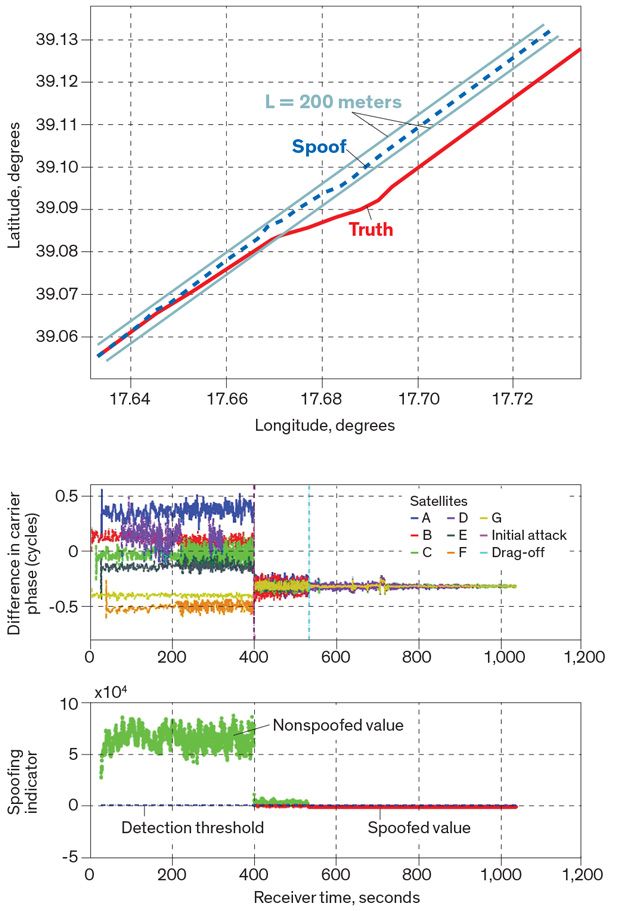 Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum02 abril 2025
Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum02 abril 2025 -
 1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for AntiMiner S7 S9 T9 T9 S9i Z9 MINI Z9 DR3 4Pins for Mining - AliExpress02 abril 2025
1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for AntiMiner S7 S9 T9 T9 S9i Z9 MINI Z9 DR3 4Pins for Mining - AliExpress02 abril 2025
você pode gostar
-
 Iruka Umino, Eroninja Wiki02 abril 2025
Iruka Umino, Eroninja Wiki02 abril 2025 -
 Pista skate dedo brinquedo extra extra extra extra02 abril 2025
Pista skate dedo brinquedo extra extra extra extra02 abril 2025 -
 My Talking Tom Friends Trucchi Illimitate Monete E Bus Gettoni Gratis by Claire Rosen - Issuu02 abril 2025
My Talking Tom Friends Trucchi Illimitate Monete E Bus Gettoni Gratis by Claire Rosen - Issuu02 abril 2025 -
 Meu desenho do motosserra homem, vejam o anime é sério! - iFunny Brazil02 abril 2025
Meu desenho do motosserra homem, vejam o anime é sério! - iFunny Brazil02 abril 2025 -
 49 ideias de T-shirt Roblox em 202302 abril 2025
49 ideias de T-shirt Roblox em 202302 abril 2025 -
 CapCut_id de roupa no brookhaven mandrake02 abril 2025
CapCut_id de roupa no brookhaven mandrake02 abril 2025 -
Tá né! #TheTown2023 #5k #csclips #fy #wave #waveigl #csgoclips #csgobr02 abril 2025
-
 Arquivo de ROBLOX - ELSAS ELECTRONICS02 abril 2025
Arquivo de ROBLOX - ELSAS ELECTRONICS02 abril 2025 -
 halloween - Royalty-Free GIFs - Animated Stickers - Cliply02 abril 2025
halloween - Royalty-Free GIFs - Animated Stickers - Cliply02 abril 2025 -
 Jojo bizarre Adventure thread02 abril 2025
Jojo bizarre Adventure thread02 abril 2025
