Suspicious User Controls
Por um escritor misterioso
Last updated 03 abril 2025

Hunting for Suspicious DNS Requests with Short Domain Extensions
Content control – Access to users correspondence add-on, Communications - Marketplace — PG Dating Pro
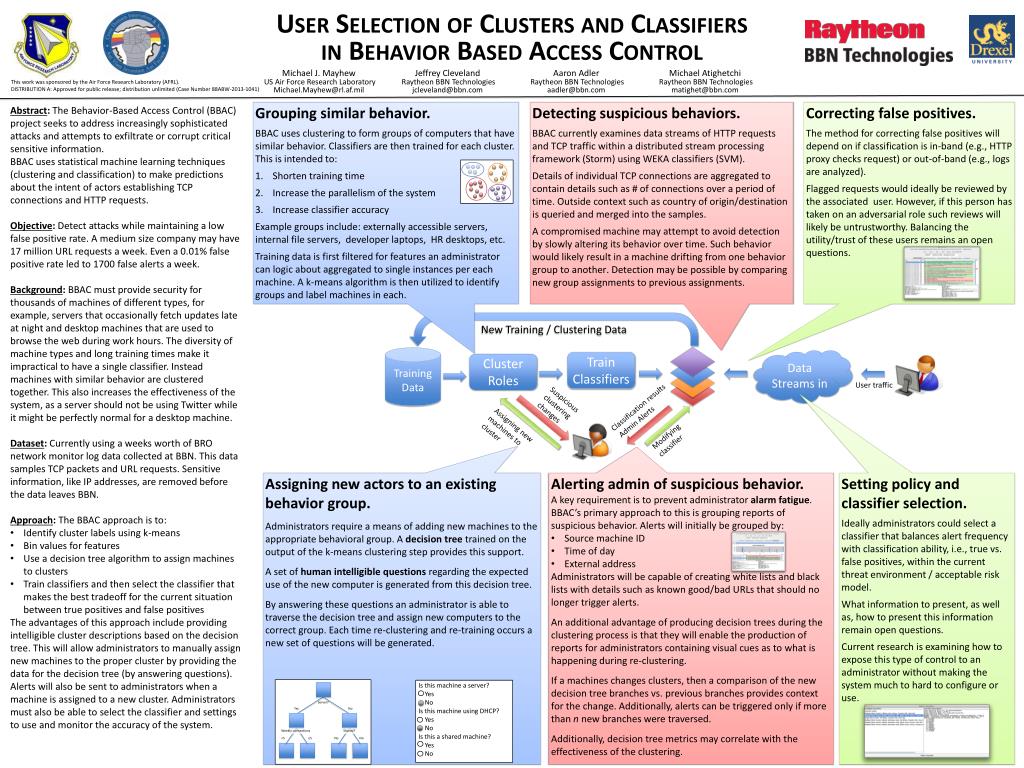
PPT - Detecting suspicious behaviors. PowerPoint Presentation, free download - ID:3093979

Insider Threat Detection Recommendations
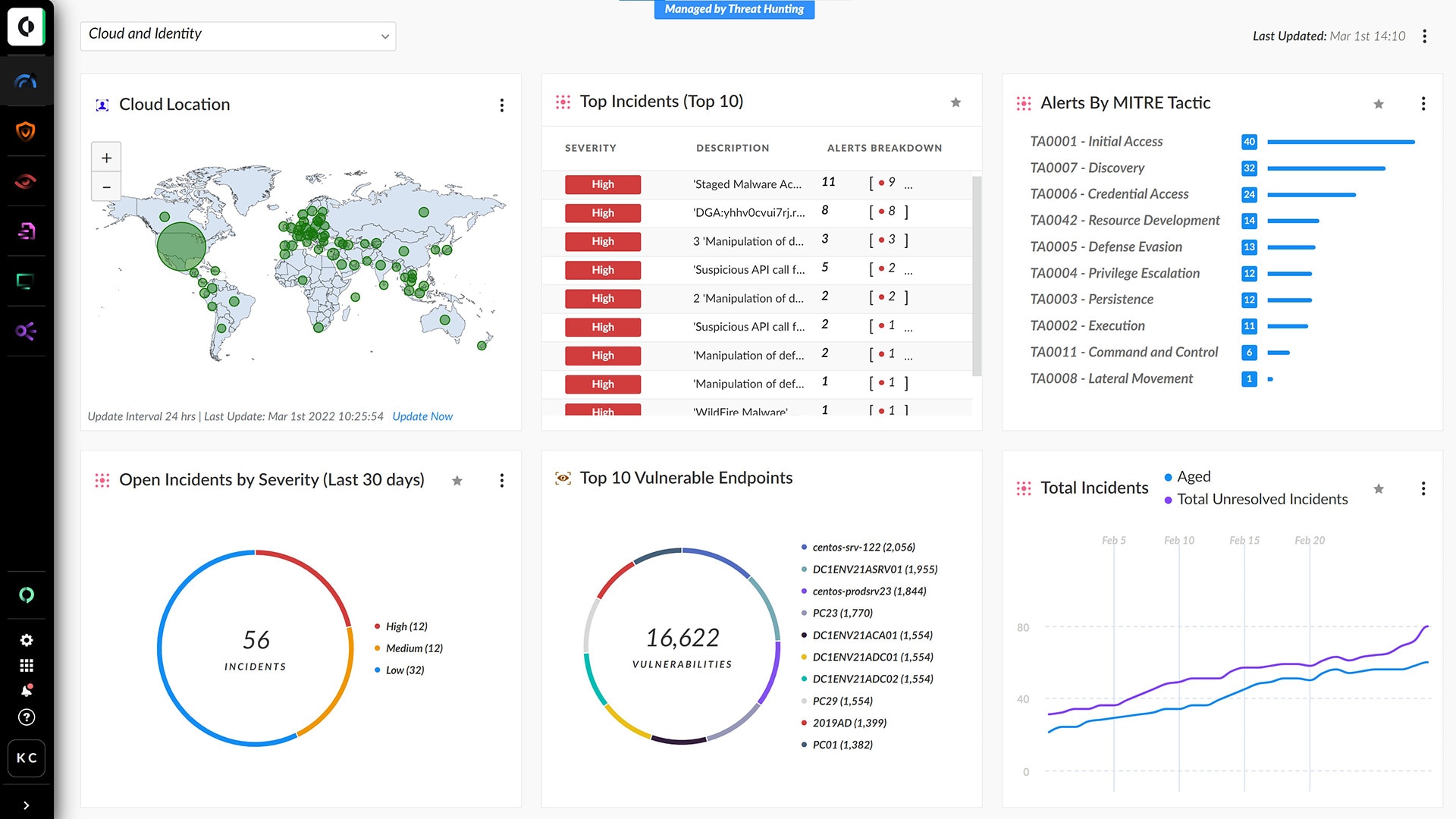
Cortex XDR- Extended Detection and Response - Palo Alto Networks
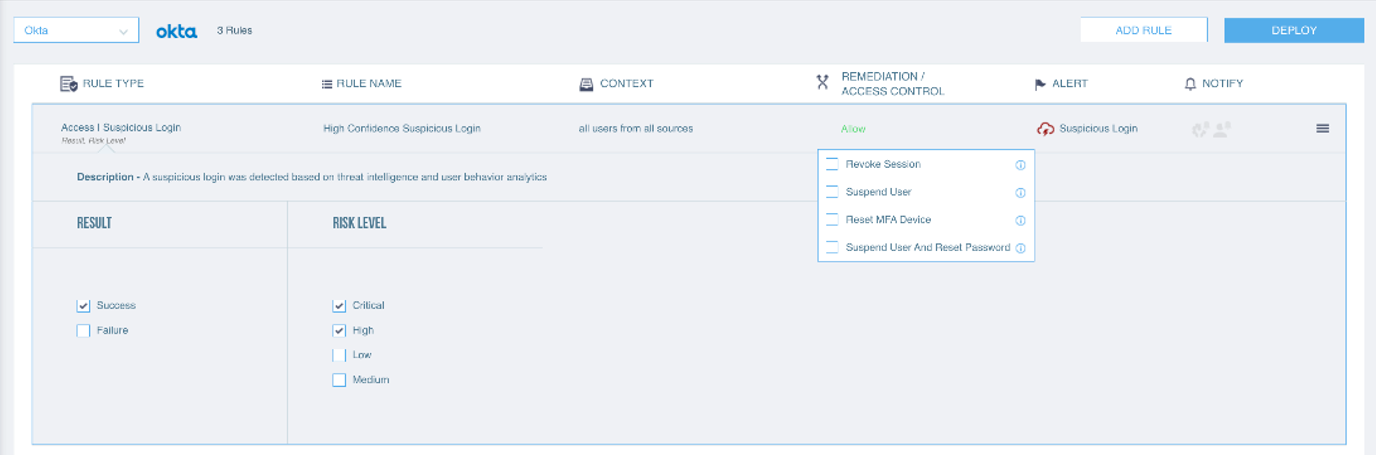
Suspicious Login Detection with your Cloud Identity Provider Through Proofpoint CASB

Zero trust element #4: Assess risk (adaptive control)

Recent Admin Enhancements in Microsoft Teams June 2023

GSPBC-1044: Lateral Movement - Taint Shared Content - GuardSight, Cybersecurity as a Service

Cloudlock K-12 Statement of Value

mongodb - Suspicious app name in Windows 10 permission prompt - Information Security Stack Exchange
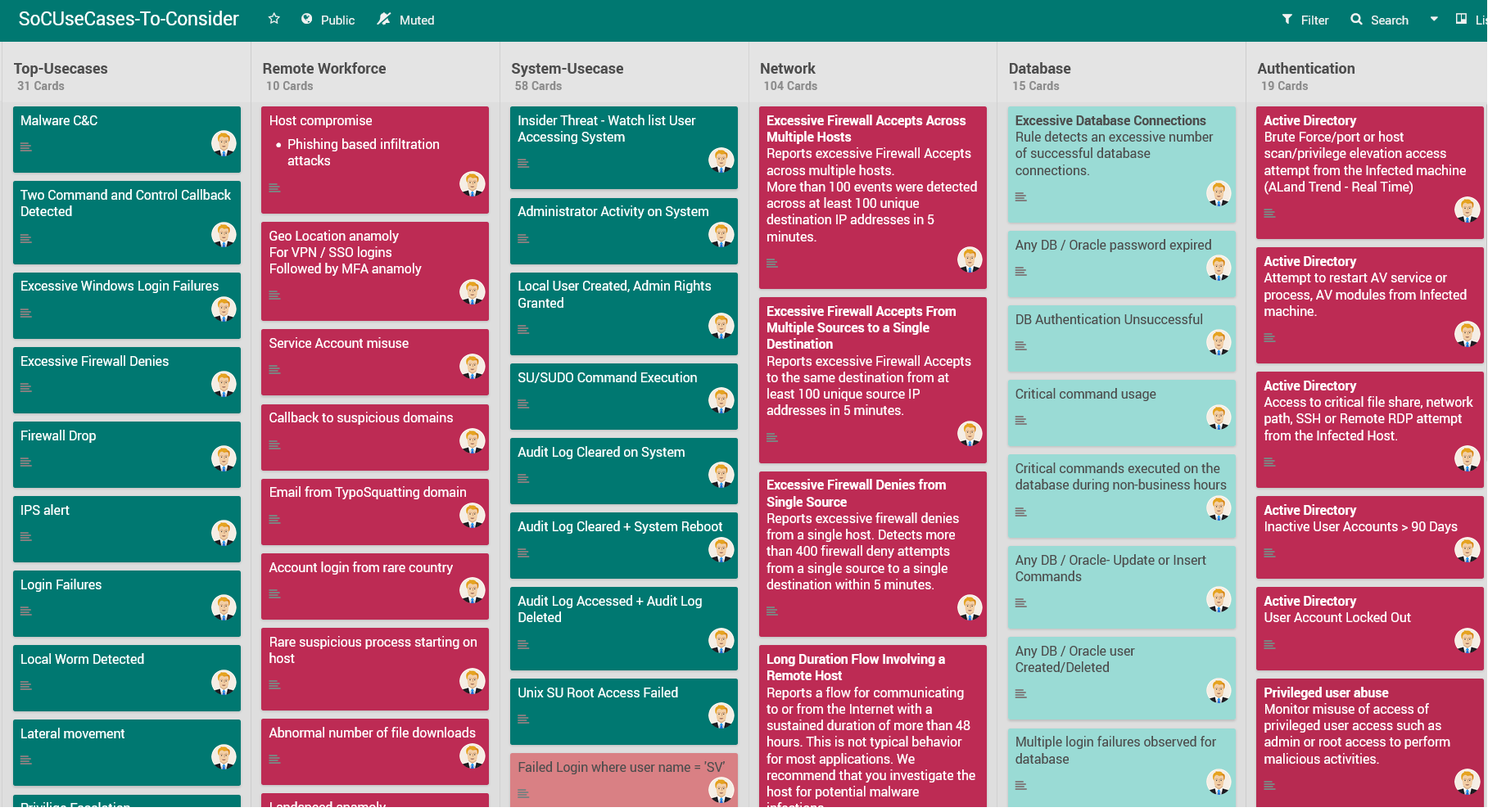
SoC SIEM Use Cases

Enhanced Data Security and Protections for SAP Cloud Services
Understanding HP Wolf Identity/Credential Protection
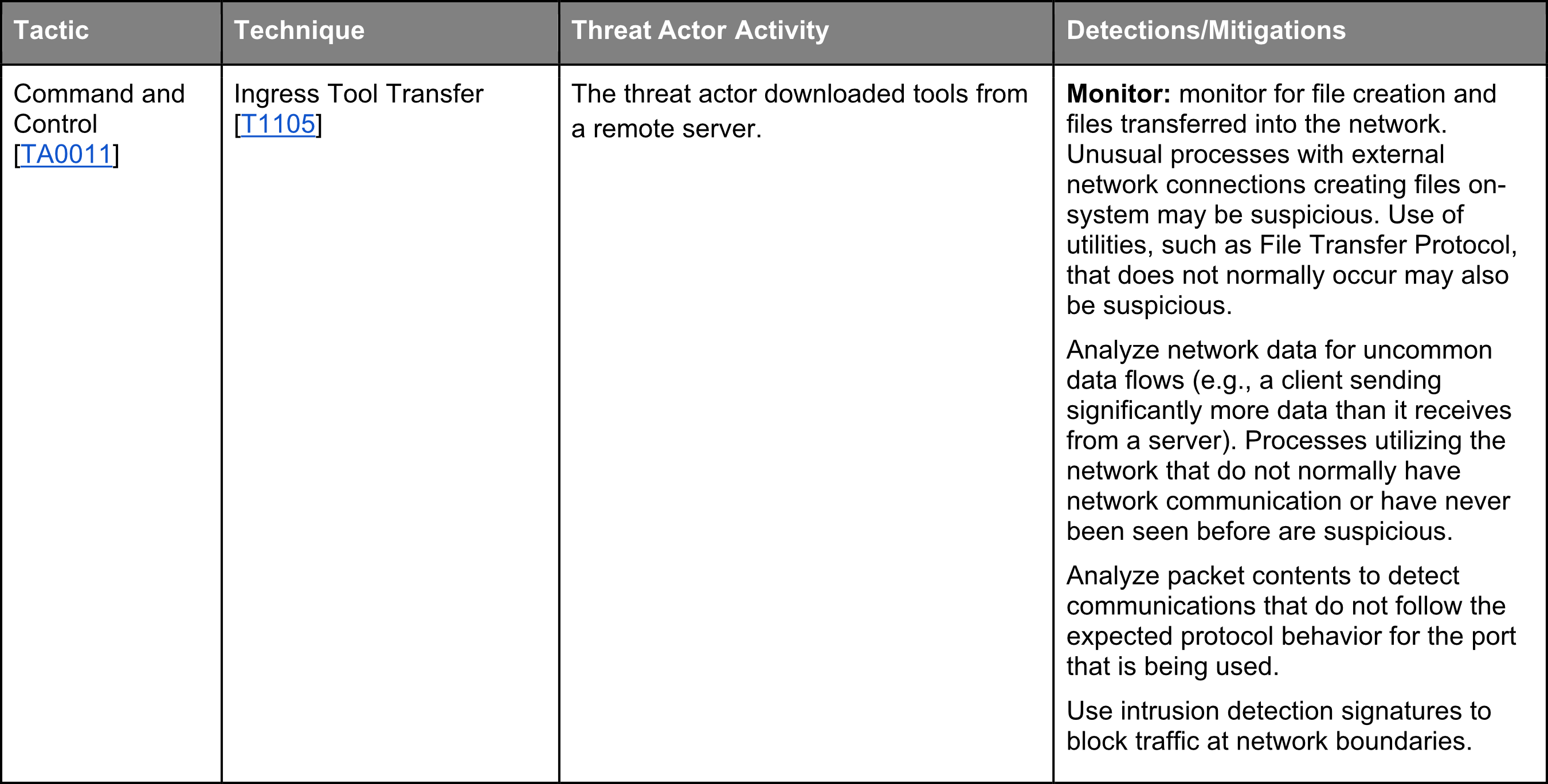
TRITON's Tactics and Techniques in the Enterprise domain + mitigations - Part 8 - SEQRED
Recomendado para você
-
 Evade - Xbox Controller Experience03 abril 2025
Evade - Xbox Controller Experience03 abril 2025 -
 Evade, Control Wiki03 abril 2025
Evade, Control Wiki03 abril 2025 -
 Translational Control of Immune Evasion in Cancer: Trends in Cancer03 abril 2025
Translational Control of Immune Evasion in Cancer: Trends in Cancer03 abril 2025 -
 Star Wars Jedi Survivor Controls Guide and Keybinds Recommendations03 abril 2025
Star Wars Jedi Survivor Controls Guide and Keybinds Recommendations03 abril 2025 -
Solved Which of the following is NOT an attempt to evade03 abril 2025
-
 TTA Insight: Move, Evade, Defend03 abril 2025
TTA Insight: Move, Evade, Defend03 abril 2025 -
 More than 10,000 air passengers evade UK border control following misdirection, The Independent03 abril 2025
More than 10,000 air passengers evade UK border control following misdirection, The Independent03 abril 2025 -
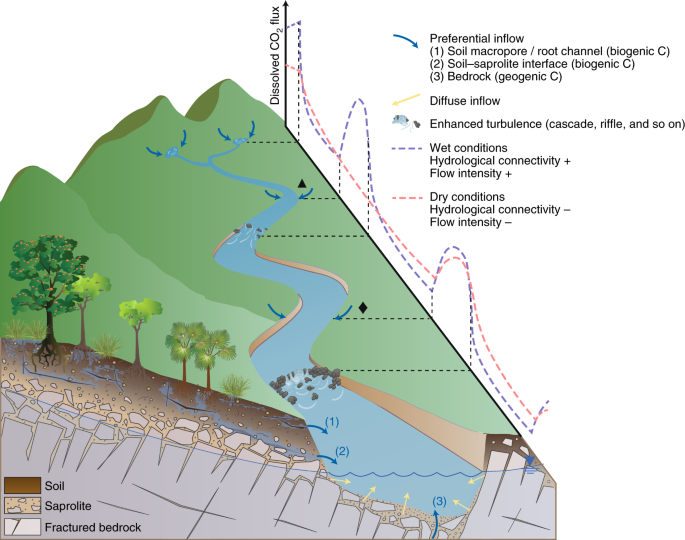 CO2 evasion along streams driven by groundwater inputs and geomorphic controls03 abril 2025
CO2 evasion along streams driven by groundwater inputs and geomorphic controls03 abril 2025 -
 Milton Friedman quote: By encouraging men to spy and report on one another03 abril 2025
Milton Friedman quote: By encouraging men to spy and report on one another03 abril 2025 -
 Sanctions and Export Controls, UK Regulatory Outlook November 2023 - Osborne Clarke03 abril 2025
Sanctions and Export Controls, UK Regulatory Outlook November 2023 - Osborne Clarke03 abril 2025
você pode gostar
-
 Call of Duty Mobile •LMG• (@LMGCODMobile) / X03 abril 2025
Call of Duty Mobile •LMG• (@LMGCODMobile) / X03 abril 2025 -
 Roblox - Códigos Mall Tycoon - Lojas e bancos gratuitos (novembro de 2023) - Listas Steam03 abril 2025
Roblox - Códigos Mall Tycoon - Lojas e bancos gratuitos (novembro de 2023) - Listas Steam03 abril 2025 -
 Boruto: Naruto the Movie (2015) - Cartazes — The Movie Database (TMDB)03 abril 2025
Boruto: Naruto the Movie (2015) - Cartazes — The Movie Database (TMDB)03 abril 2025 -
 como cuidar do piercing no umbigo styllo03 abril 2025
como cuidar do piercing no umbigo styllo03 abril 2025 -
 Pokemon 2083 Shiny Farfetchd Pokedex: Evolution, Moves, Location03 abril 2025
Pokemon 2083 Shiny Farfetchd Pokedex: Evolution, Moves, Location03 abril 2025 -
 Lyza (Made in Abyss) - Pictures03 abril 2025
Lyza (Made in Abyss) - Pictures03 abril 2025 -
 Turismo em Hoenn: Littleroot Town, Rota 101, Oldale Town, Rota 102 e Rota 10303 abril 2025
Turismo em Hoenn: Littleroot Town, Rota 101, Oldale Town, Rota 102 e Rota 10303 abril 2025 -
 St. Louis Dance Clubs: 10Best Nightlife Reviews03 abril 2025
St. Louis Dance Clubs: 10Best Nightlife Reviews03 abril 2025 -
 Godhuman + Dark Dagger Combo03 abril 2025
Godhuman + Dark Dagger Combo03 abril 2025 -
 Center Calçados Tênis Cavalera Break High - Center Calçados03 abril 2025
Center Calçados Tênis Cavalera Break High - Center Calçados03 abril 2025