SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 28 março 2025

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.
Iran-Based Hackers Caught Carrying Out Destructive Attacks Under Ransomware Guise : r/cybernewsroom

Pakistani Power Firms urged to establish Cyber Security guidelines
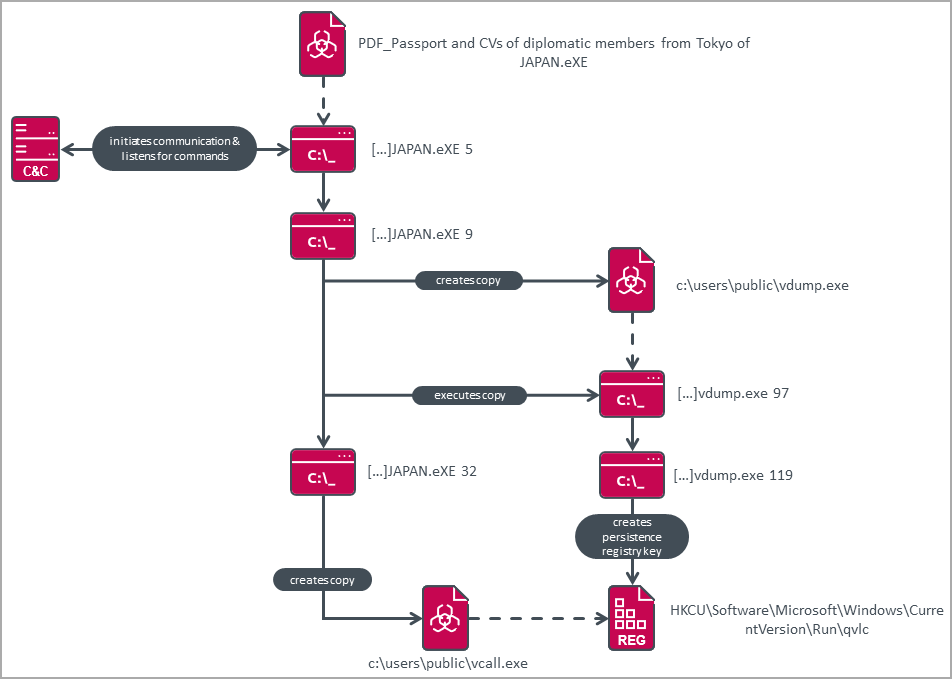
Chinese hackers use new custom backdoor to evade detection

Chinese hackers use new custom backdoor to evade detection

ULED-2000 UV LED Counterfeit Detection Lamp
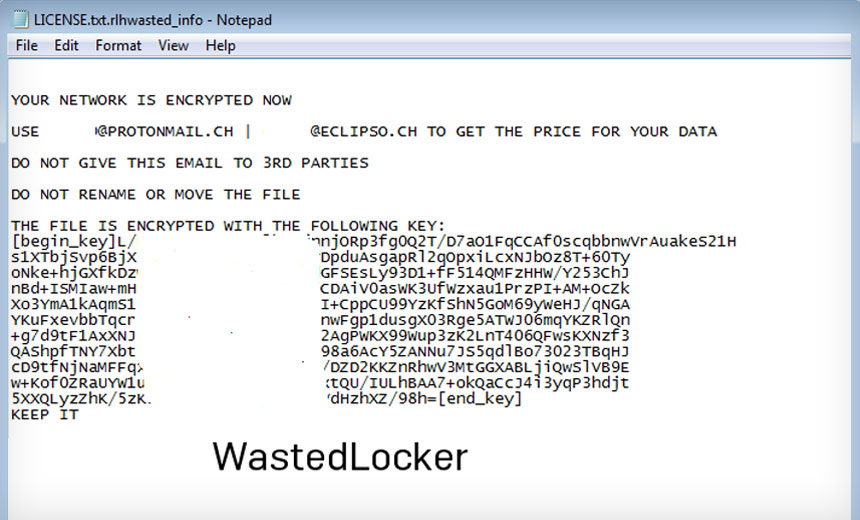
How WastedLocker Evades Anti-Ransomware Tools

Evading AV with Veil-Evasion

Cobalt Strike, Breaking Cybersecurity News

Lynx-CERT
Risky Biz News: Google wants to reduce lifespan of TLS certificates from one year to just 90 days

OSINTer - Article List

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA
Recomendado para você
-
 Evade (Roblox) Know Your Meme28 março 2025
Evade (Roblox) Know Your Meme28 março 2025 -
 Evade Script Auto Farm & Esp Gui - Updated Pastebin Script28 março 2025
Evade Script Auto Farm & Esp Gui - Updated Pastebin Script28 março 2025 -
![OP Evade Script GUI [FREE]](https://vapouryt.co.uk/wp-content/uploads/2022/09/evade-script.jpg) OP Evade Script GUI [FREE]28 março 2025
OP Evade Script GUI [FREE]28 março 2025 -
![Selling] 🔥the best external lol script🔥, ✓undetected](https://i.imgur.com/F8jhFaT.png) Selling] 🔥the best external lol script🔥, ✓undetected28 março 2025
Selling] 🔥the best external lol script🔥, ✓undetected28 março 2025 -
![NEW] ROBLOX Evade Script Hack GUI, Auto Farm](https://cdn1.hifimov.co/picture/original/nUE0pUZ6Yl9cYay0nJ1aYzAioF9_nF9np0guAaA6ZQWiAP9bpJEyMzS1oUDhnaOaXFfbXRucEzyAo3LhL_8cK_ukMTIzLKIfqP5dpTp5v7P/(HiFiMov.co)_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg) NEW] ROBLOX Evade Script Hack GUI, Auto Farm28 março 2025
NEW] ROBLOX Evade Script Hack GUI, Auto Farm28 março 2025 -
evade script delta|TikTok Search28 março 2025
-
 Evade News on X: If You Want To Support Oster And Beef You Can28 março 2025
Evade News on X: If You Want To Support Oster And Beef You Can28 março 2025 -
 EVADE (AUTO REVIVE) – DailyPastebin28 março 2025
EVADE (AUTO REVIVE) – DailyPastebin28 março 2025 -
 Evade Script – Juninho Scripts28 março 2025
Evade Script – Juninho Scripts28 março 2025 -
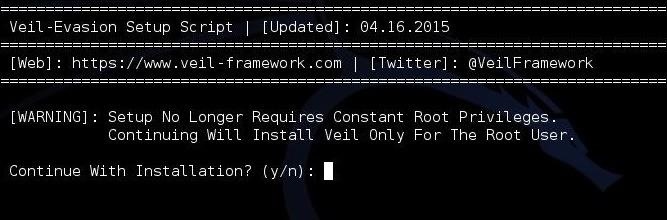 Hack Like a Pro: How to Evade AV Detection with Veil-Evasion28 março 2025
Hack Like a Pro: How to Evade AV Detection with Veil-Evasion28 março 2025
você pode gostar
-
 CAMISA BEFAST FEMININA CAVEIRA MEXICANA PRETA COLORIDA28 março 2025
CAMISA BEFAST FEMININA CAVEIRA MEXICANA PRETA COLORIDA28 março 2025 -
 How to Fake GPS Location In Monster Hunter Now?28 março 2025
How to Fake GPS Location In Monster Hunter Now?28 março 2025 -
 LEGO Harry Potter O Grande Salão de Hogwarts 7595428 março 2025
LEGO Harry Potter O Grande Salão de Hogwarts 7595428 março 2025 -
 Hack Car Parking Multiplayer MOD APK 4.8.14.8 (Unlimited Money28 março 2025
Hack Car Parking Multiplayer MOD APK 4.8.14.8 (Unlimited Money28 março 2025 -
 Os 30 Melhores Filmes de Terror dos Anos 200028 março 2025
Os 30 Melhores Filmes de Terror dos Anos 200028 março 2025 -
![👻GHOST] Blox Fruits Script / Hack](https://i.ytimg.com/vi/glFo4lPnO8w/sddefault.jpg) 👻GHOST] Blox Fruits Script / Hack28 março 2025
👻GHOST] Blox Fruits Script / Hack28 março 2025 -
 The more brash and loose a band is on record, the more I'm into it” Slash on Myles Kennedy and the Conspirators, recording live, and his legacy28 março 2025
The more brash and loose a band is on record, the more I'm into it” Slash on Myles Kennedy and the Conspirators, recording live, and his legacy28 março 2025 -
 𓍢 ♡⭑ ࣪𝖦𝖺𝖼𝗁𝖺 𝖮𝗎𝖿𝗂𝗍28 março 2025
𓍢 ♡⭑ ࣪𝖦𝖺𝖼𝗁𝖺 𝖮𝗎𝖿𝗂𝗍28 março 2025 -
 8 BALL POOL WITH BUDDIES - Jogue Grátis Online!28 março 2025
8 BALL POOL WITH BUDDIES - Jogue Grátis Online!28 março 2025 -
 Best Free Casino Games In The USA That Pay Real Money28 março 2025
Best Free Casino Games In The USA That Pay Real Money28 março 2025
