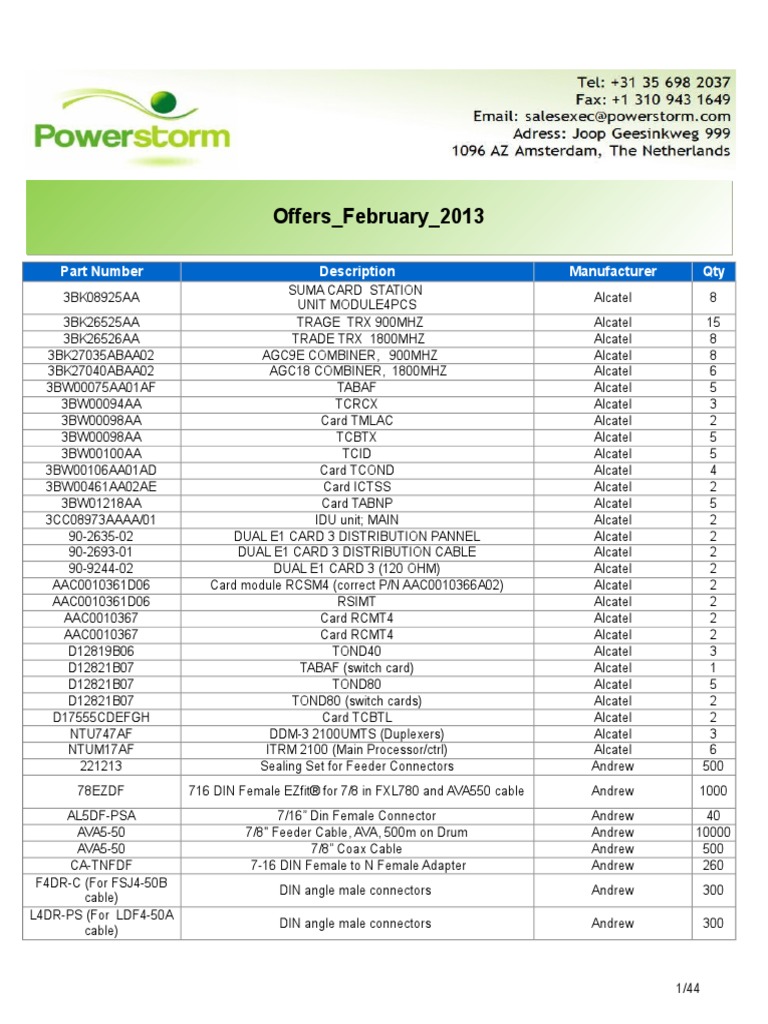
UA Part 6: Mappings - 6 Message SecurityProtocols
Por um escritor misterioso
Last updated 02 abril 2025

Criminal Justice Information Services (CJIS) Security Policy - FBI

Sequence diagram of the Co-Location Detection Phase of PPCA, assuming

Blockchain-based key management system in Named Data Networking: A survey - ScienceDirect
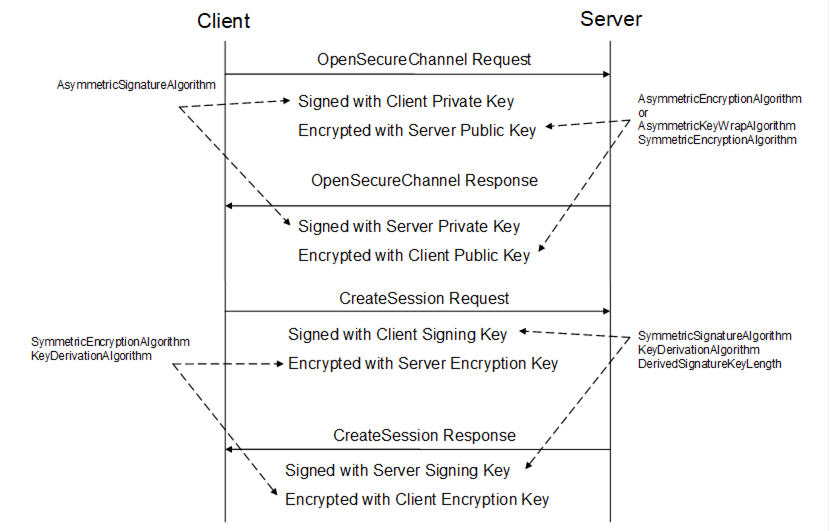
UA Part 6: Mappings - 4 Overview
Sensors, Free Full-Text

West Central Alabama ACTION: Advanced Connected Transportation Infrastructure & Operations Network - Introduction - FHWA Office of Operations

UA Part 6: Mappings - 6 Message SecurityProtocols
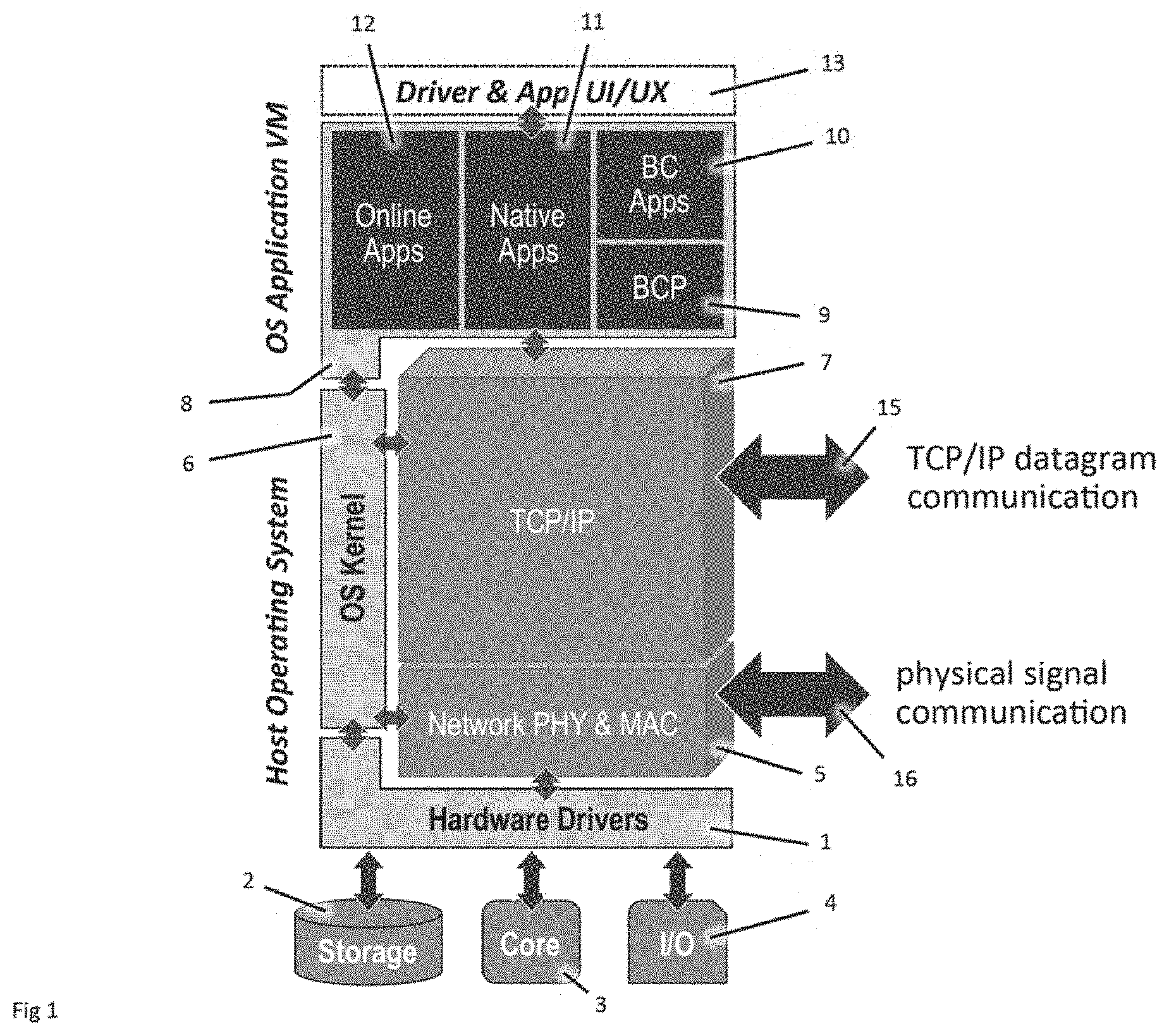
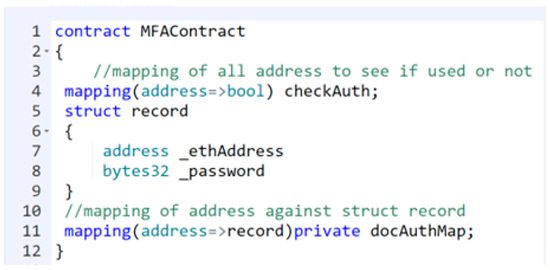
Decentralized Cybersecure Privacy Network For Cloud Communication, Computing And Global e-Commerce Verzun; Ievgen ; et al. [Listat Ltd.]
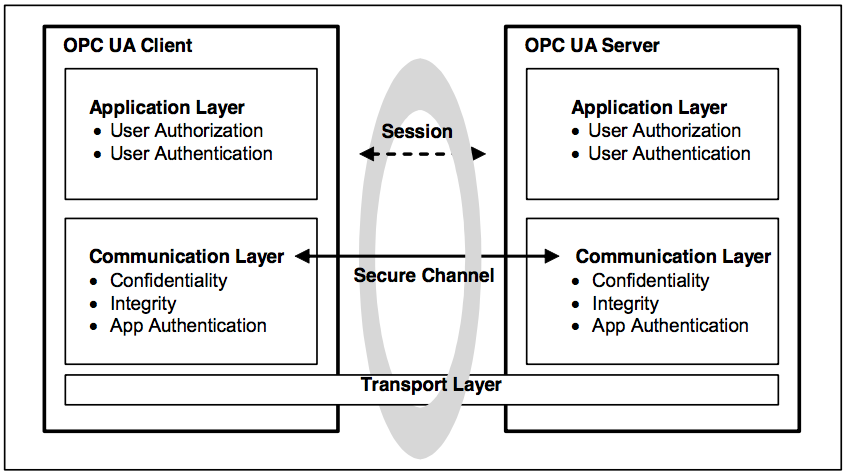
4 OPC Security architecture · OPC UA
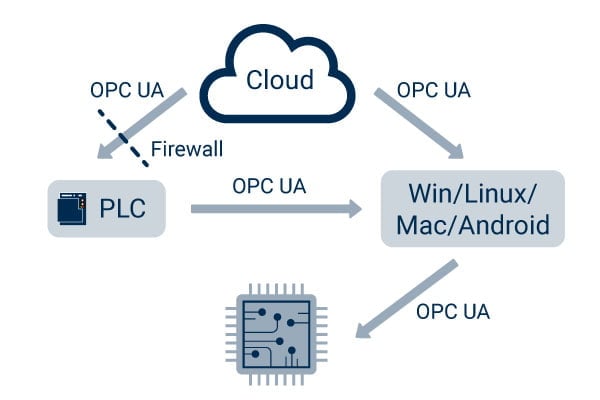
world Interfaces play a crucial role in today's networked
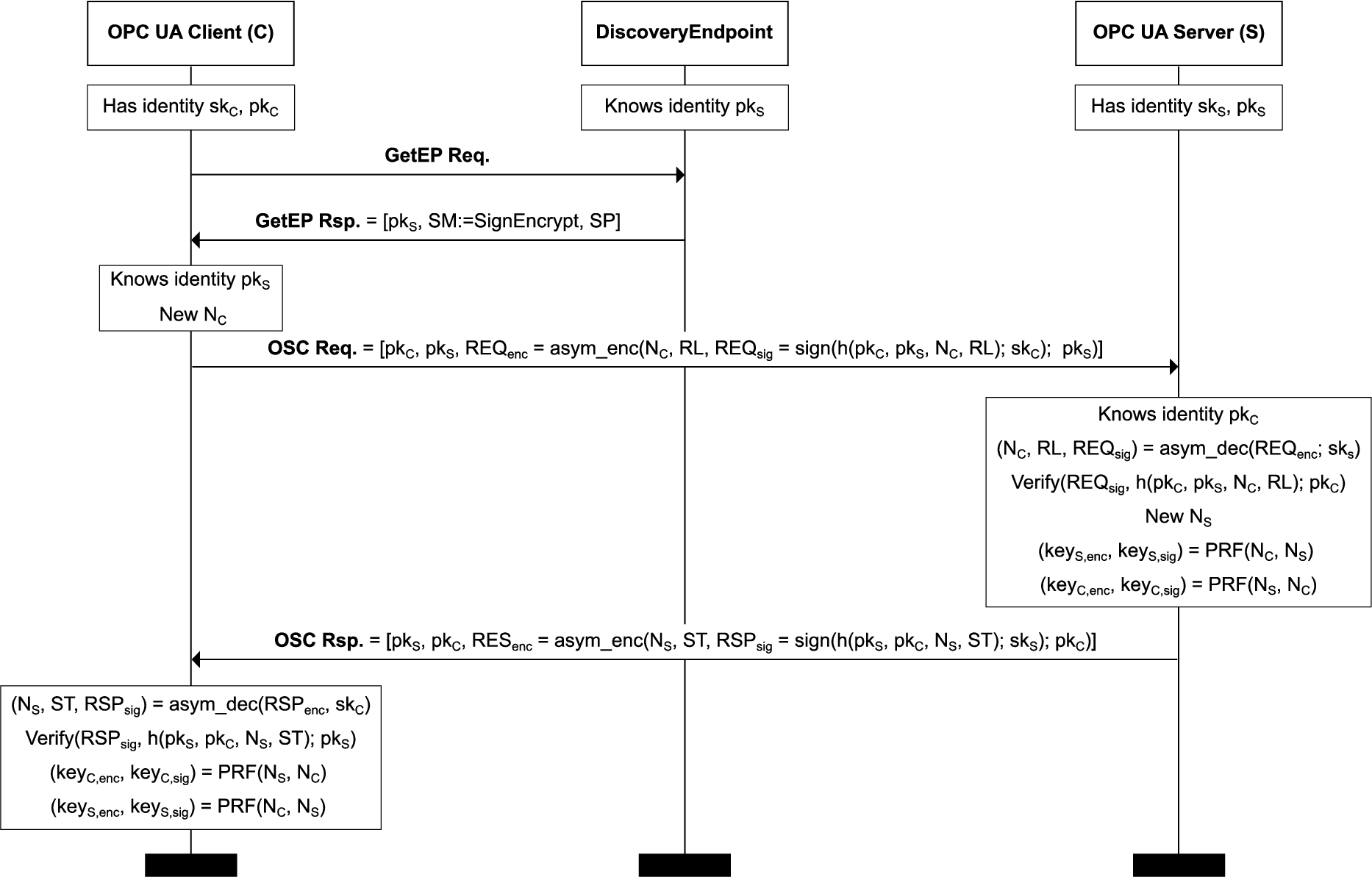
Towards post-quantum security for cyber-physical systems: Integrating PQC into industrial M2M communication 1 - IOS Press

What is driving the adoption of Chinese surveillance technology in Africa? - DFRLab
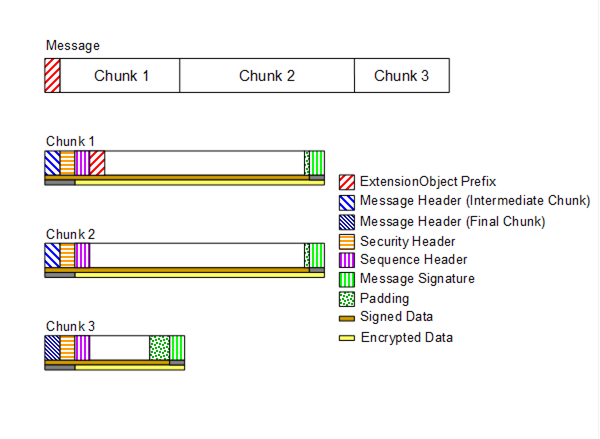
UA Part 6: Mappings - 7.1.2 Message structure
Recomendado para você
-
 SCP-10000 World of Anthros, Wiki02 abril 2025
SCP-10000 World of Anthros, Wiki02 abril 2025 -
 Program Book - Gershwin & Bernstein by Chicago Symphony02 abril 2025
Program Book - Gershwin & Bernstein by Chicago Symphony02 abril 2025 -
demo/docs/03_sparkLoad2StarRocks.md at master · StarRocks/demo02 abril 2025
-
 PDF02 abril 2025
PDF02 abril 2025 -
 Gigabyte UD1000GM PG5 & UD750GM 80+ Gold Power Supply Impressions02 abril 2025
Gigabyte UD1000GM PG5 & UD750GM 80+ Gold Power Supply Impressions02 abril 2025 -
 8 Advanced parallelization - Deep Learning with JAX02 abril 2025
8 Advanced parallelization - Deep Learning with JAX02 abril 2025 -
Offers February 2013 Powerstorm02 abril 2025
-
 How to Defeat 10,000 SCP-096 CLONES! (MULTIPLAYER)02 abril 2025
How to Defeat 10,000 SCP-096 CLONES! (MULTIPLAYER)02 abril 2025 -
TreasureBox.ke Outer Ring Road02 abril 2025
-
 RI360P2-QR14-LIU5X2 by TURCK - Buy or Repair at Radwell02 abril 2025
RI360P2-QR14-LIU5X2 by TURCK - Buy or Repair at Radwell02 abril 2025
você pode gostar
-
 robux gratis 12302 abril 2025
robux gratis 12302 abril 2025 -
 Hikaru Nakamura on X: Apparently this is a match twitch wanted to02 abril 2025
Hikaru Nakamura on X: Apparently this is a match twitch wanted to02 abril 2025 -
 QTCinderella Updates (@QTC_Updates) / X02 abril 2025
QTCinderella Updates (@QTC_Updates) / X02 abril 2025 -
 Pac-Chicken, Crossy Road Wiki02 abril 2025
Pac-Chicken, Crossy Road Wiki02 abril 2025 -
 Temple Run 202 abril 2025
Temple Run 202 abril 2025 -
 Jogos da Barbie no Jogalo02 abril 2025
Jogos da Barbie no Jogalo02 abril 2025 -
 Custom Wedding Anniversary Pikachu Pokemon Card02 abril 2025
Custom Wedding Anniversary Pikachu Pokemon Card02 abril 2025 -
 Record of Grancrest War (TV Series 2018– ) - IMDb02 abril 2025
Record of Grancrest War (TV Series 2018– ) - IMDb02 abril 2025 -
Skateboard Party 3 Pro – Apps no Google Play02 abril 2025
-
twicebrasil #twice02 abril 2025