Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 01 abril 2025

Ransomware: How it Works & How to Remove It
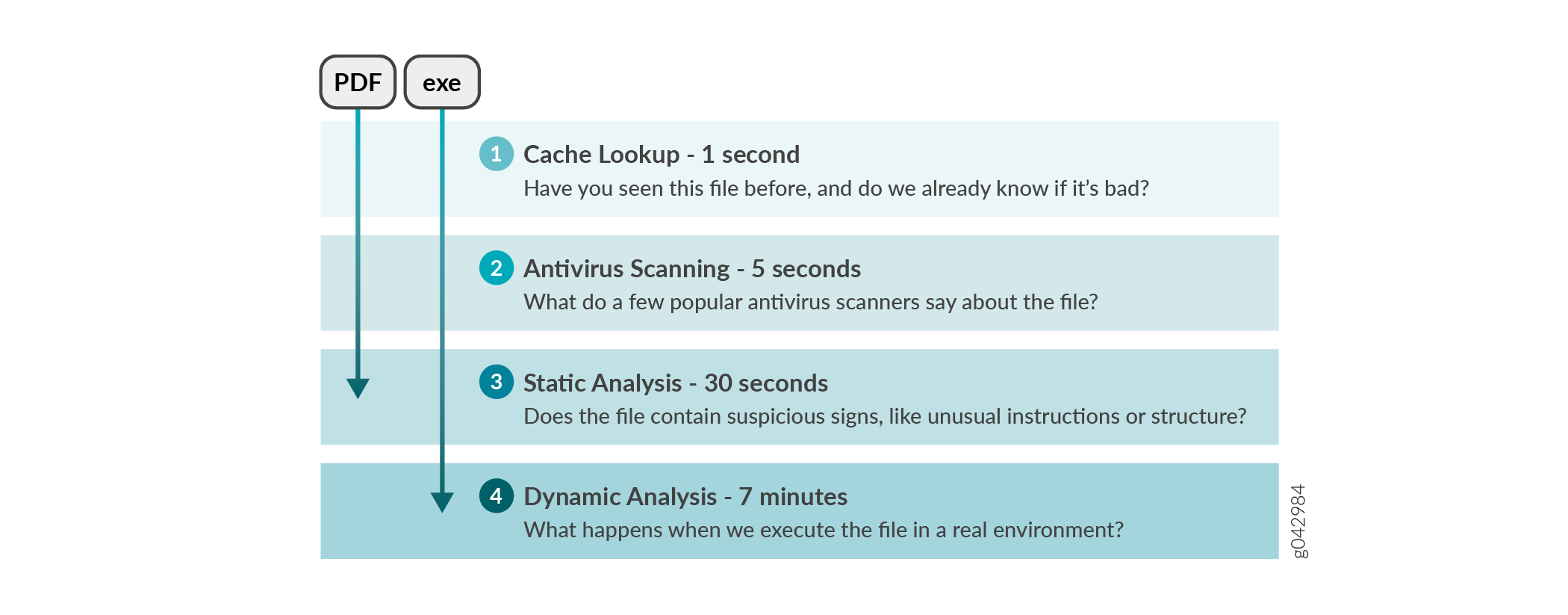
How is Malware Analyzed and Detected?, ATP Cloud

What Is Malware Analysis? Definition, Types, Stages, and Best

1. General Flow of Signature-Based Malware Detection and Analysis

Dismantling ZLoader: How malicious ads led to disabled security
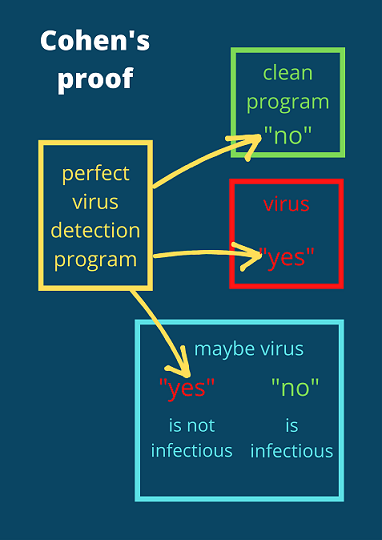
The real reason why malware detection is hard
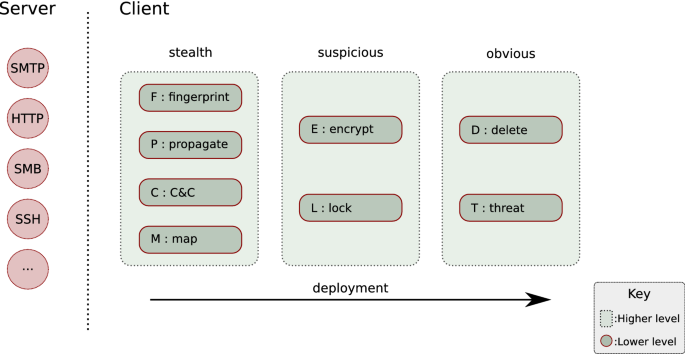
Ransomware deployment methods and analysis: views from a
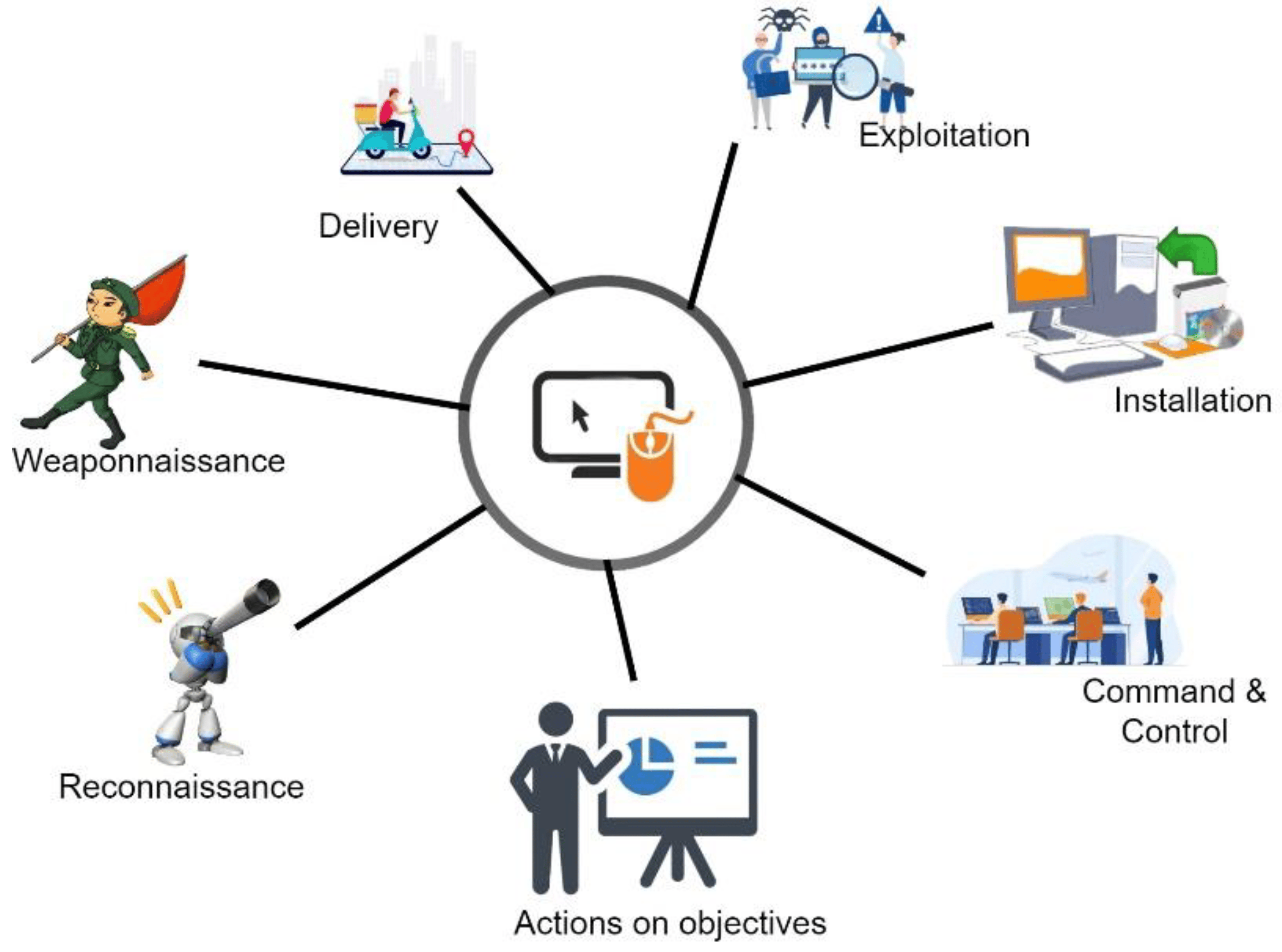
Symmetry, Free Full-Text

Top 10 Malware Analysis Platforms & Tools

Dynamic Malware Analysis in the Modern Era—A State of the Art Survey
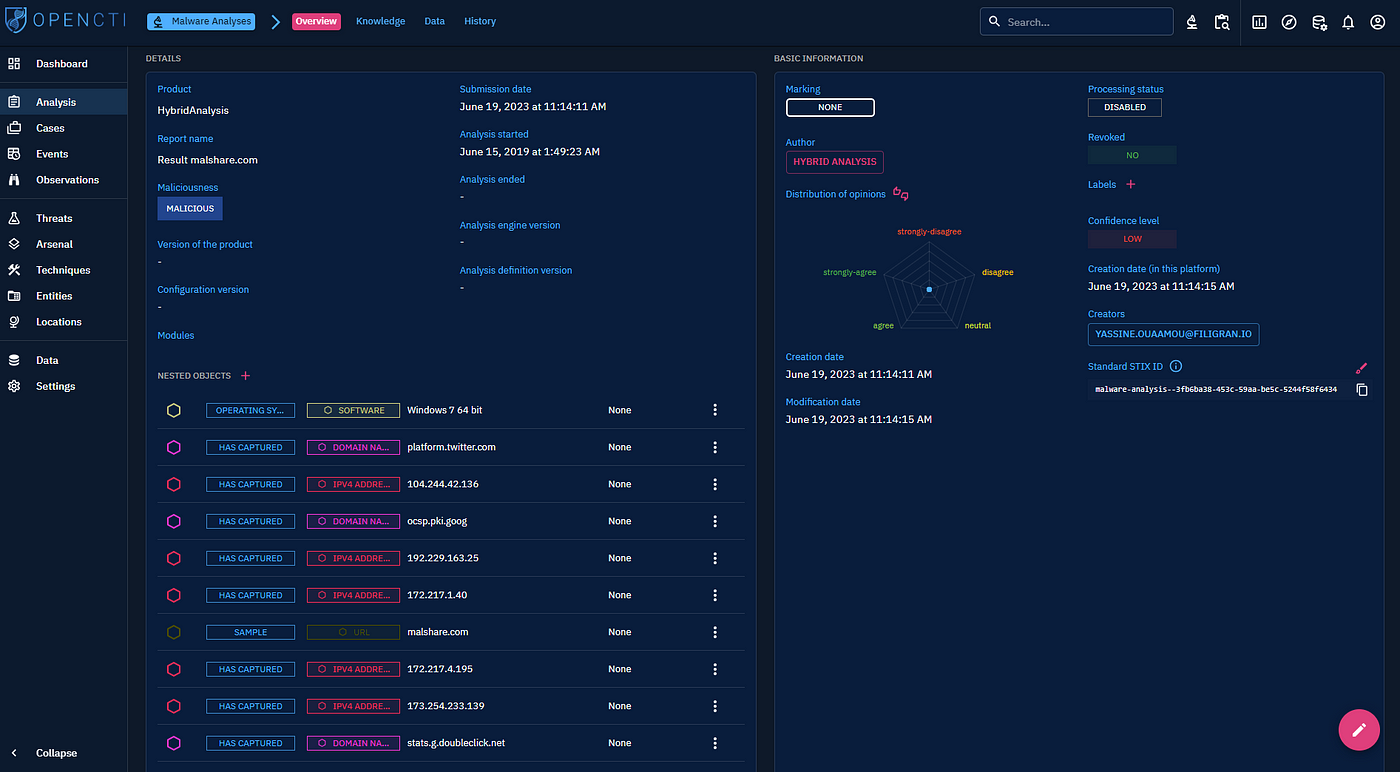
Introducing malware analysis: enhance your cybersecurity triage

Using Python for Malware Analysis — A Beginners Guide
Recomendado para você
-
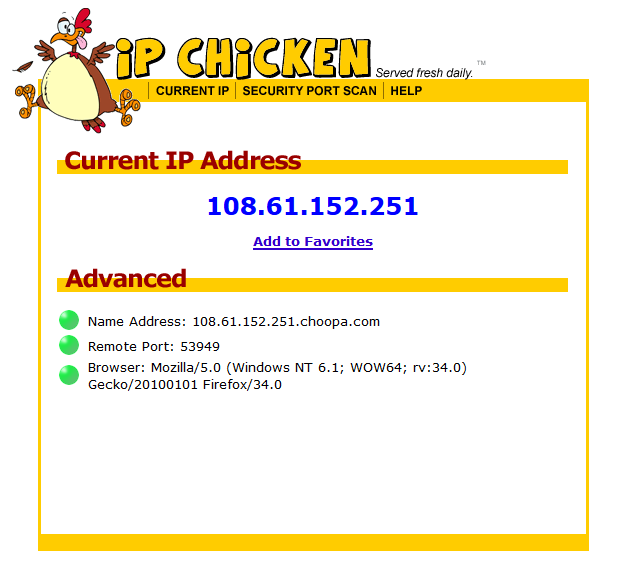
 IPchicken at the terminal01 abril 2025
IPchicken at the terminal01 abril 2025 -
 Private Internet Access via L2TP IPSEC Cisco IOS Client01 abril 2025
Private Internet Access via L2TP IPSEC Cisco IOS Client01 abril 2025 -
 Is Ipchicken.com Legit or a Scam? Info, Reviews and Complaints01 abril 2025
Is Ipchicken.com Legit or a Scam? Info, Reviews and Complaints01 abril 2025 -
 Test It!, Onion Pi01 abril 2025
Test It!, Onion Pi01 abril 2025 -
 IP Chicken - Adventures of a Nurse01 abril 2025
IP Chicken - Adventures of a Nurse01 abril 2025 -
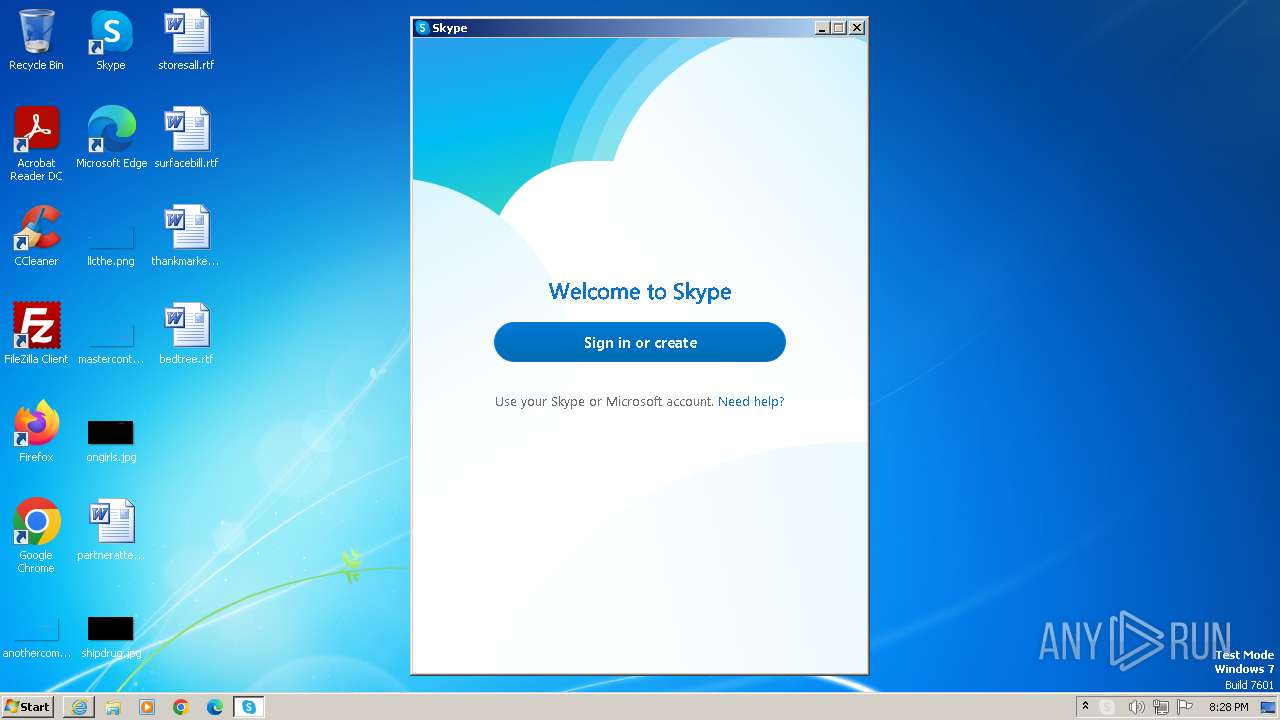 Malware analysis Malicious activity01 abril 2025
Malware analysis Malicious activity01 abril 2025 -
 shell - SSH socks proxy via jumphost - Stack Overflow01 abril 2025
shell - SSH socks proxy via jumphost - Stack Overflow01 abril 2025 -
 Instant Pot Chicken Salad with Strawberries, Feta, and Pecans - Pesto & Margaritas01 abril 2025
Instant Pot Chicken Salad with Strawberries, Feta, and Pecans - Pesto & Margaritas01 abril 2025 -
 Instant Pot Chicken Parmesan - Cooking With Karli01 abril 2025
Instant Pot Chicken Parmesan - Cooking With Karli01 abril 2025 -
 Instant Pot Chicken with Mushrooms, Leeks, and Artichokes - White Coat Pink Apron01 abril 2025
Instant Pot Chicken with Mushrooms, Leeks, and Artichokes - White Coat Pink Apron01 abril 2025
você pode gostar
-
![Updated] Chaos Clickers Codes : January 2023 » Gaming Guide](https://i0.wp.com/theposterstyle.com/wp-content/uploads/2022/08/ezgif.com-gif-maker-74.webp) Updated] Chaos Clickers Codes : January 2023 » Gaming Guide01 abril 2025
Updated] Chaos Clickers Codes : January 2023 » Gaming Guide01 abril 2025 -
 Jack Smith adds war crimes prosecutor — his deputy from the Hague01 abril 2025
Jack Smith adds war crimes prosecutor — his deputy from the Hague01 abril 2025 -
 Entrei com R$ 600, e hoje, só em um jogo, tenho R$ 42 mil01 abril 2025
Entrei com R$ 600, e hoje, só em um jogo, tenho R$ 42 mil01 abril 2025 -
1 Pç Brinquedos Pokemon Pokeball Pop-Up Elf Pokébola De Brinquedo01 abril 2025
-
 What in the Middle-Earth are reviewers saying about The Lord of the Rings: Gollum? - Xfire01 abril 2025
What in the Middle-Earth are reviewers saying about The Lord of the Rings: Gollum? - Xfire01 abril 2025 -
Sidney Leather Creeper Platform Shoes in Black01 abril 2025
-
 BORDERLANDS 2: GOLDEN CHEST - LEVEL 50 (4 Keys)01 abril 2025
BORDERLANDS 2: GOLDEN CHEST - LEVEL 50 (4 Keys)01 abril 2025 -
 sono bisque doll fim da 1 temporada01 abril 2025
sono bisque doll fim da 1 temporada01 abril 2025 -
 Wallpaper Saint Seiya Soul of Gold Nº 201 abril 2025
Wallpaper Saint Seiya Soul of Gold Nº 201 abril 2025 -
 Black Friday Deals Nintendo Switch 2023: Discount, Where To Buy and Wh – EasySMX01 abril 2025
Black Friday Deals Nintendo Switch 2023: Discount, Where To Buy and Wh – EasySMX01 abril 2025
