Malware analysis Malicious activity
Por um escritor misterioso
Last updated 29 março 2025

How to Analyze Malware's Network Traffic in A Sandbox
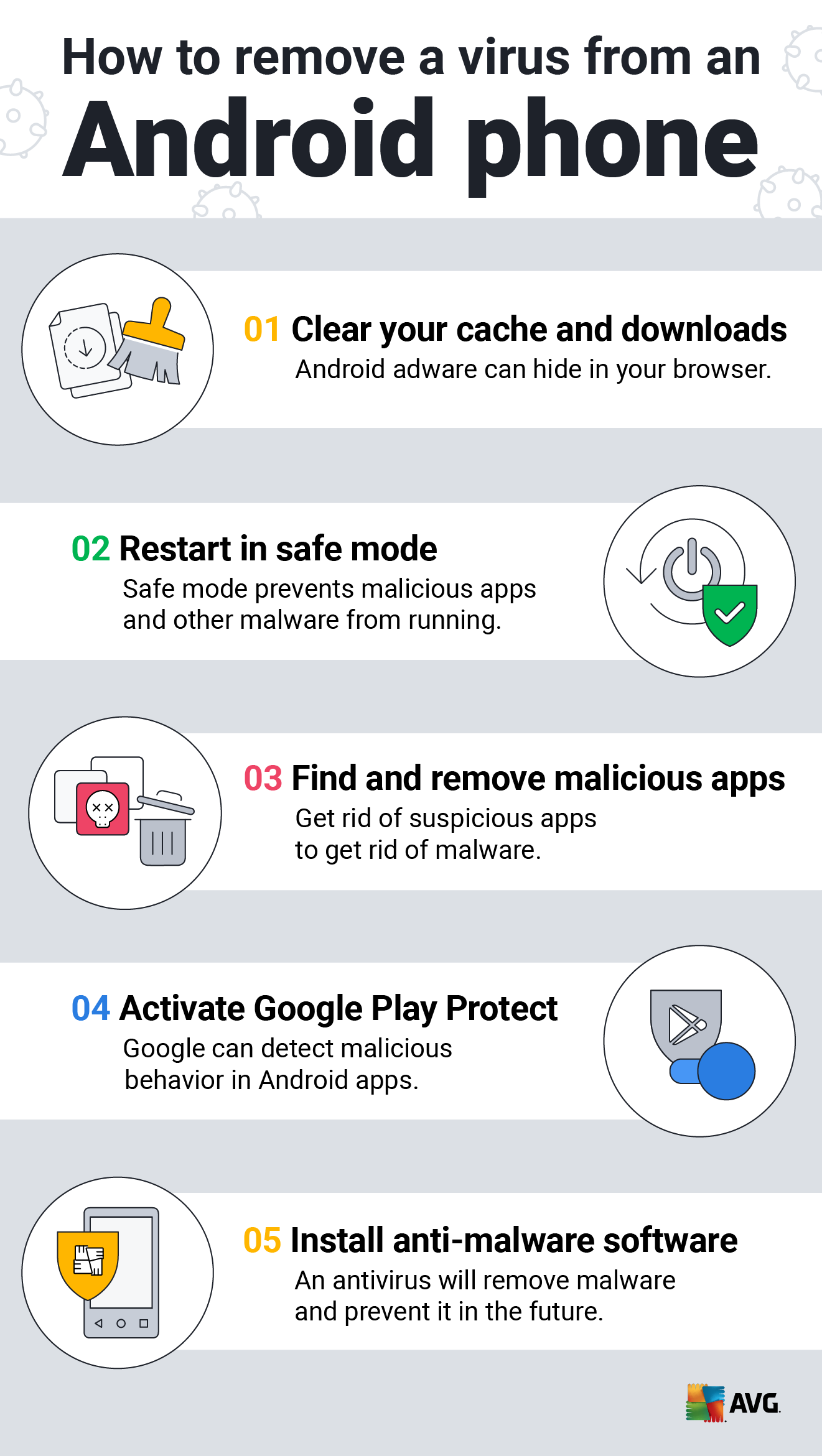
How to Clean an Android or iPhone from Viruses for Free

StopRansomware: Rhysida Ransomware

How to Remove Windows Defender Security Warning Scam
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Unveiling activities of Tropic Trooper 2023 deep analysis of Xiangoop Loader and EntryShell payload

Malware analysis mykey_.rar Malicious activity

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware Analysis: Steps & Examples - CrowdStrike
Interactive Online Malware Sandbox

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
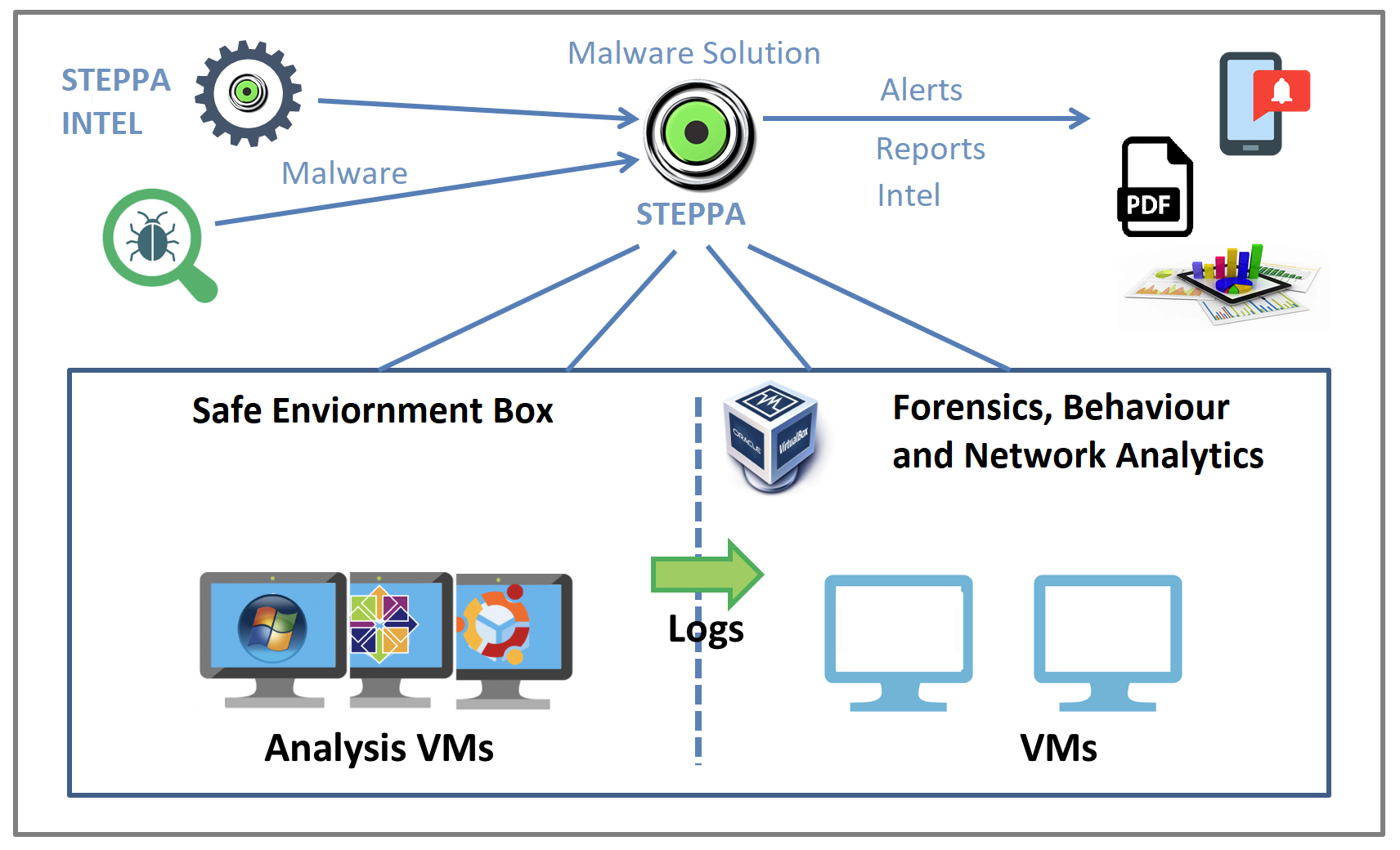
Malware Analysis Solution: Analyze, Detect, and Protect
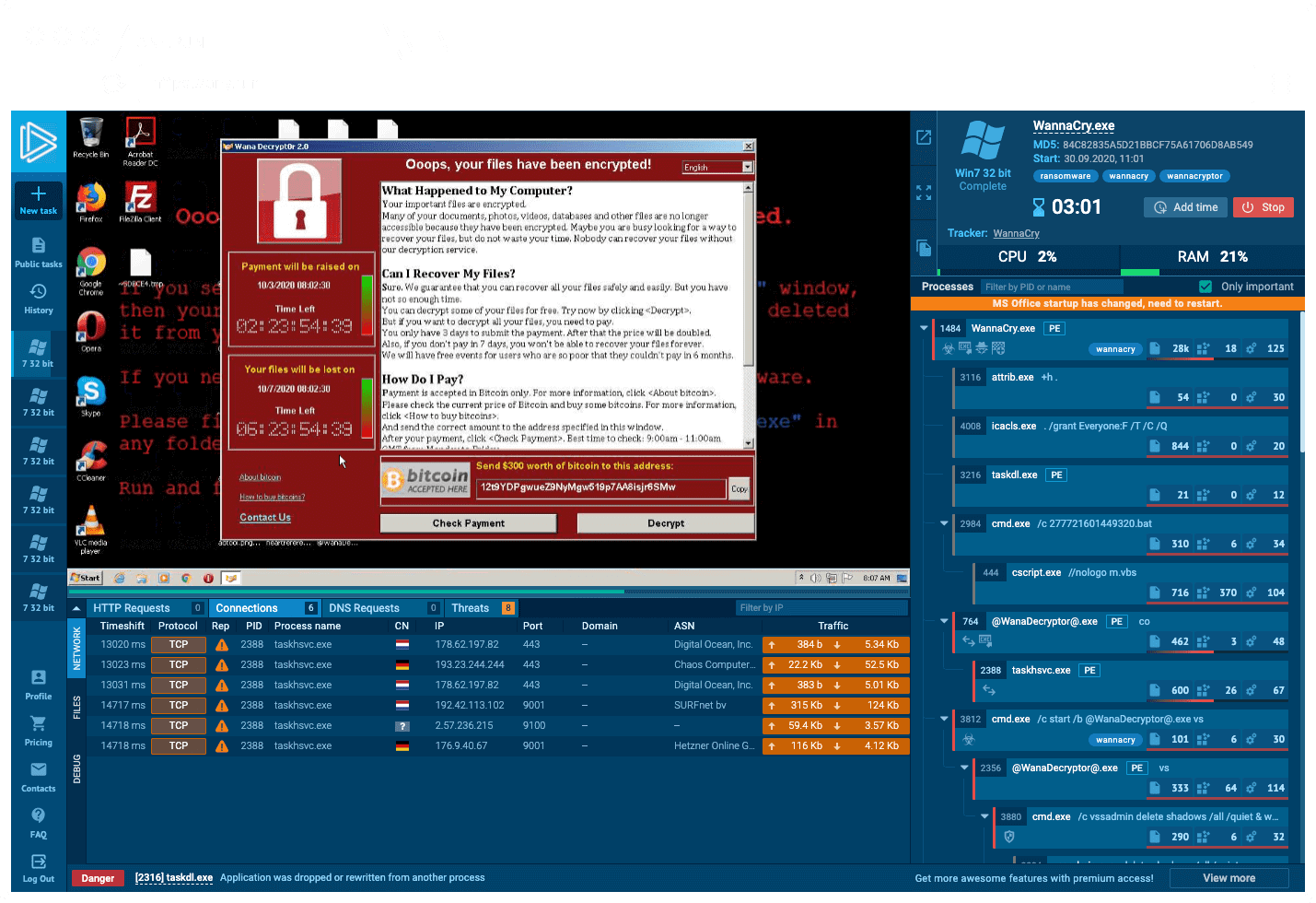
Interactive Online Malware Sandbox
Recomendado para você
-
 site jounin react29 março 2025
site jounin react29 março 2025 -
How are Jonin promoted in Naruto? - Quora29 março 2025
-
 naruto jounin xD, hidan, m29 março 2025
naruto jounin xD, hidan, m29 março 2025 -
Jounin29 março 2025
-
 The Orange Sensei - Chapter 1: Naruto the Jounin-sensei - Page 3 - Wattpad29 março 2025
The Orange Sensei - Chapter 1: Naruto the Jounin-sensei - Page 3 - Wattpad29 março 2025 -
 Am I the only person who thinks they all should've been promoted to Jonin by the end of the series? : r/Naruto29 março 2025
Am I the only person who thinks they all should've been promoted to Jonin by the end of the series? : r/Naruto29 março 2025 -
Clan Jounin gakure29 março 2025
-
Who is the weakest Jonin in Naruto? - Quora29 março 2025
-
 Minato Namikaze (Jonin), NarutoOnline Wiki29 março 2025
Minato Namikaze (Jonin), NarutoOnline Wiki29 março 2025 -
![HI3rd Darkbolt Jonin Yae Sakura over Kuki Shinobu [Genshin Impact] [Mods]](https://images.gamebanana.com/img/ss/mods/644751488a095.jpg) HI3rd Darkbolt Jonin Yae Sakura over Kuki Shinobu [Genshin Impact] [Mods]29 março 2025
HI3rd Darkbolt Jonin Yae Sakura over Kuki Shinobu [Genshin Impact] [Mods]29 março 2025
você pode gostar
-
 Ultra Beasts, Nintendo29 março 2025
Ultra Beasts, Nintendo29 março 2025 -
 Qual destes Insetos merece uma Mega Evolução?29 março 2025
Qual destes Insetos merece uma Mega Evolução?29 março 2025 -
 Undisputed: Testamos o jogo que traz retorno do boxe aos games de forma impecável29 março 2025
Undisputed: Testamos o jogo que traz retorno do boxe aos games de forma impecável29 março 2025 -
fairy tail ep 1 dublado português|TikTok Search29 março 2025
-
 Nonton Anime Oshi No Ko Episode 4 Sub Indo, Cek Linknya di Sini29 março 2025
Nonton Anime Oshi No Ko Episode 4 Sub Indo, Cek Linknya di Sini29 março 2025 -
 Seleção da Copa do Mundo de 2022: veja os melhores jogadores29 março 2025
Seleção da Copa do Mundo de 2022: veja os melhores jogadores29 março 2025 -
 Folga para ver jogo do Brasil na Copa precisa ser acordada com o patrão29 março 2025
Folga para ver jogo do Brasil na Copa precisa ser acordada com o patrão29 março 2025 -
 Modern Warfare 2 review: A buggy mess that requires major patchwork - Dexerto29 março 2025
Modern Warfare 2 review: A buggy mess that requires major patchwork - Dexerto29 março 2025 -
Stickman Warriors Mod APK v1.6.729 março 2025
-
 179+ Thousand Chess Pieces Royalty-Free Images, Stock Photos & Pictures29 março 2025
179+ Thousand Chess Pieces Royalty-Free Images, Stock Photos & Pictures29 março 2025


