Malware analysis Malicious activity
Por um escritor misterioso
Last updated 07 abril 2025
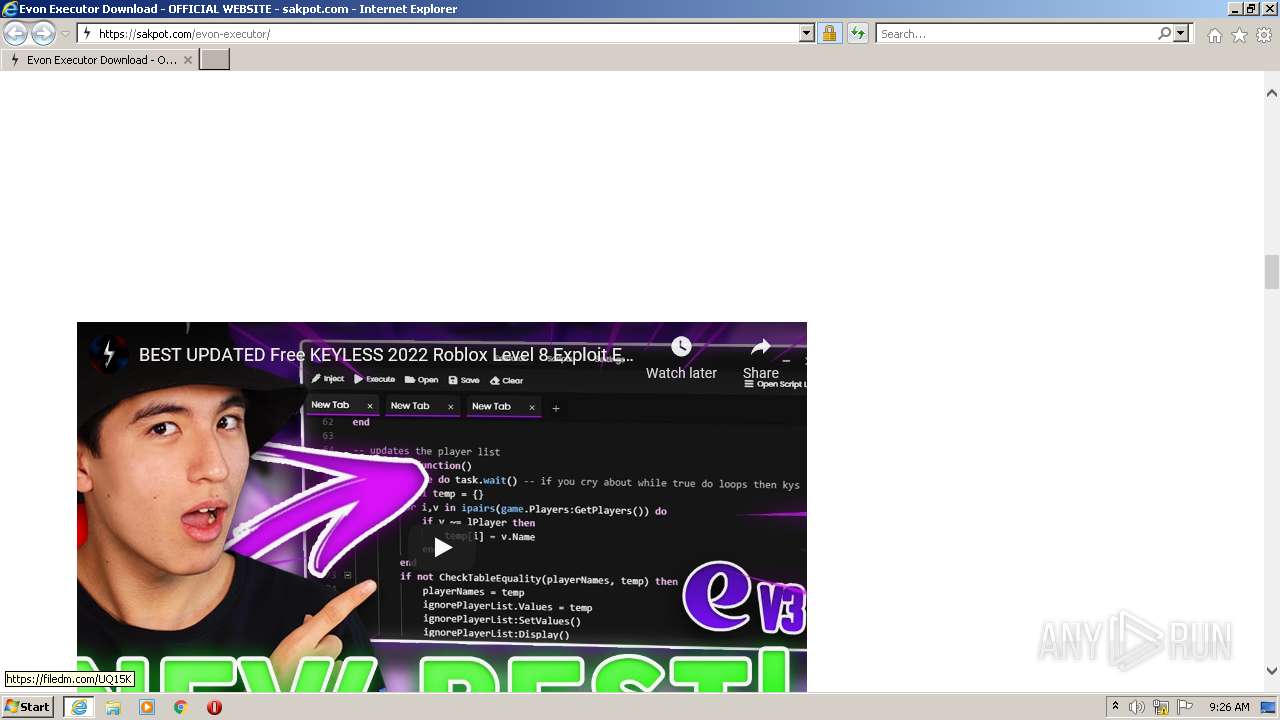
Malware analysis metasploit.bat Malicious activity

Brute Force Attacks: Password Protection
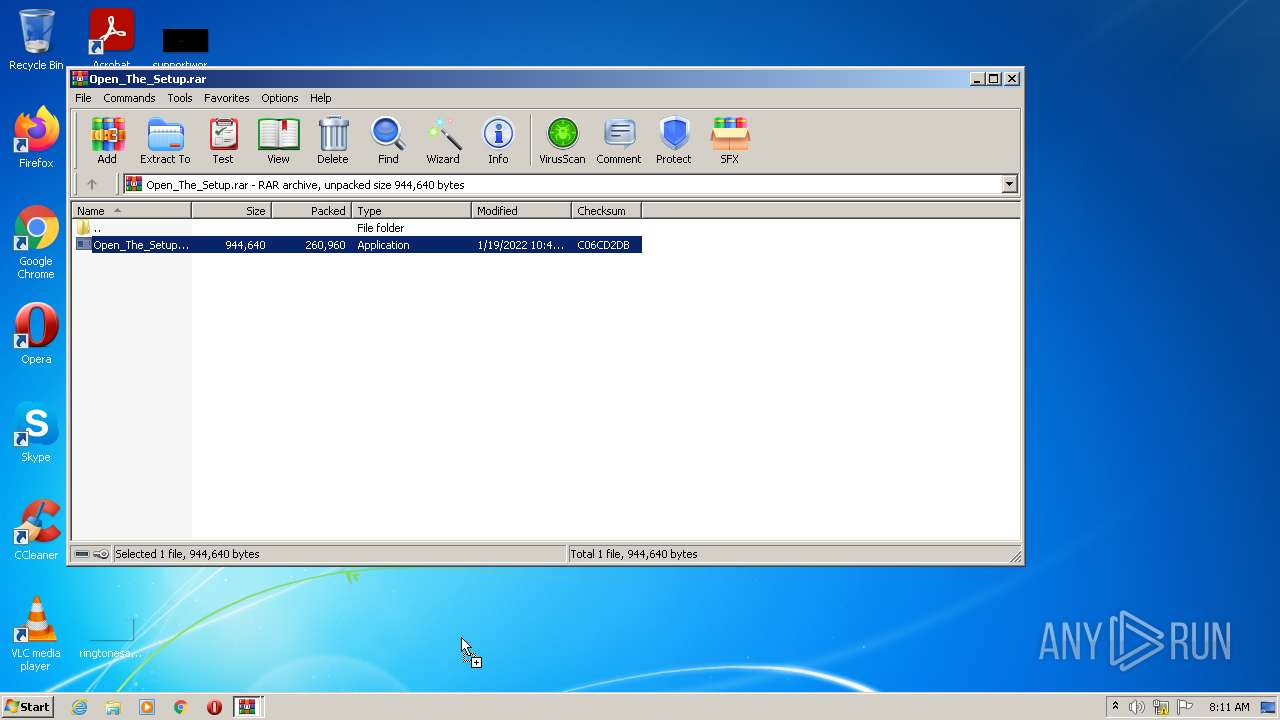
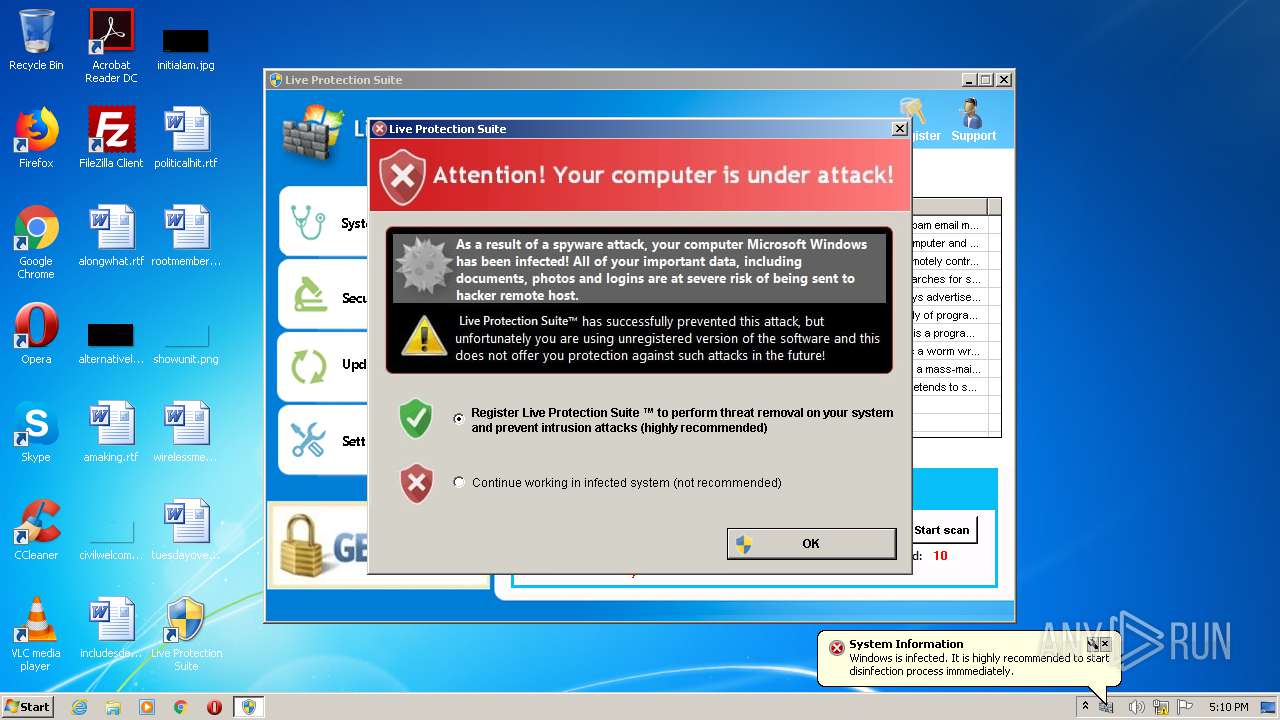
Malware analysis file Malicious activity
Download Free Antivirus Software

AlienVault - Open Threat Exchange

Malware Analysis: Steps & Examples - CrowdStrike
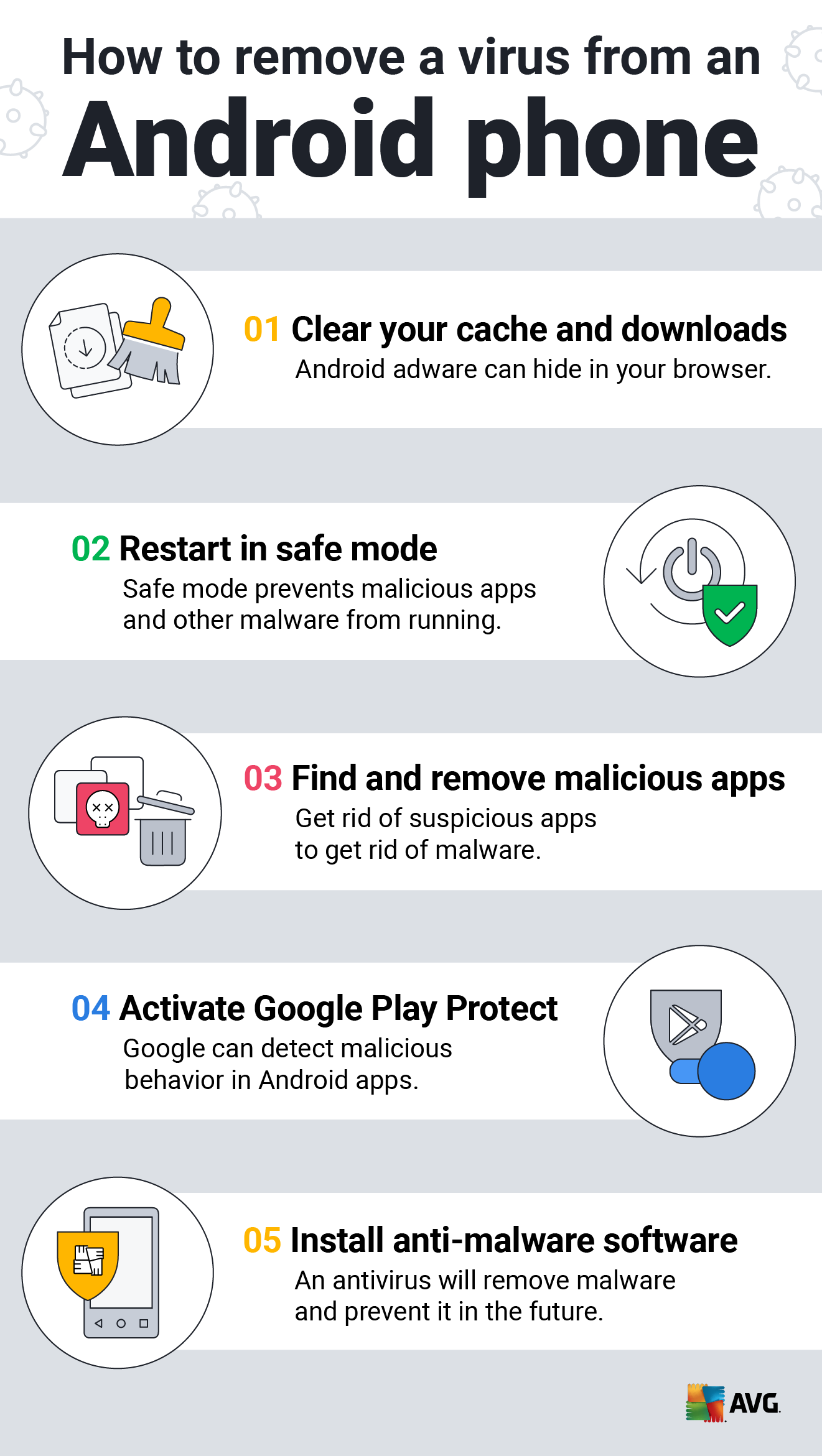
How to Clean an Android or iPhone from Viruses for Free
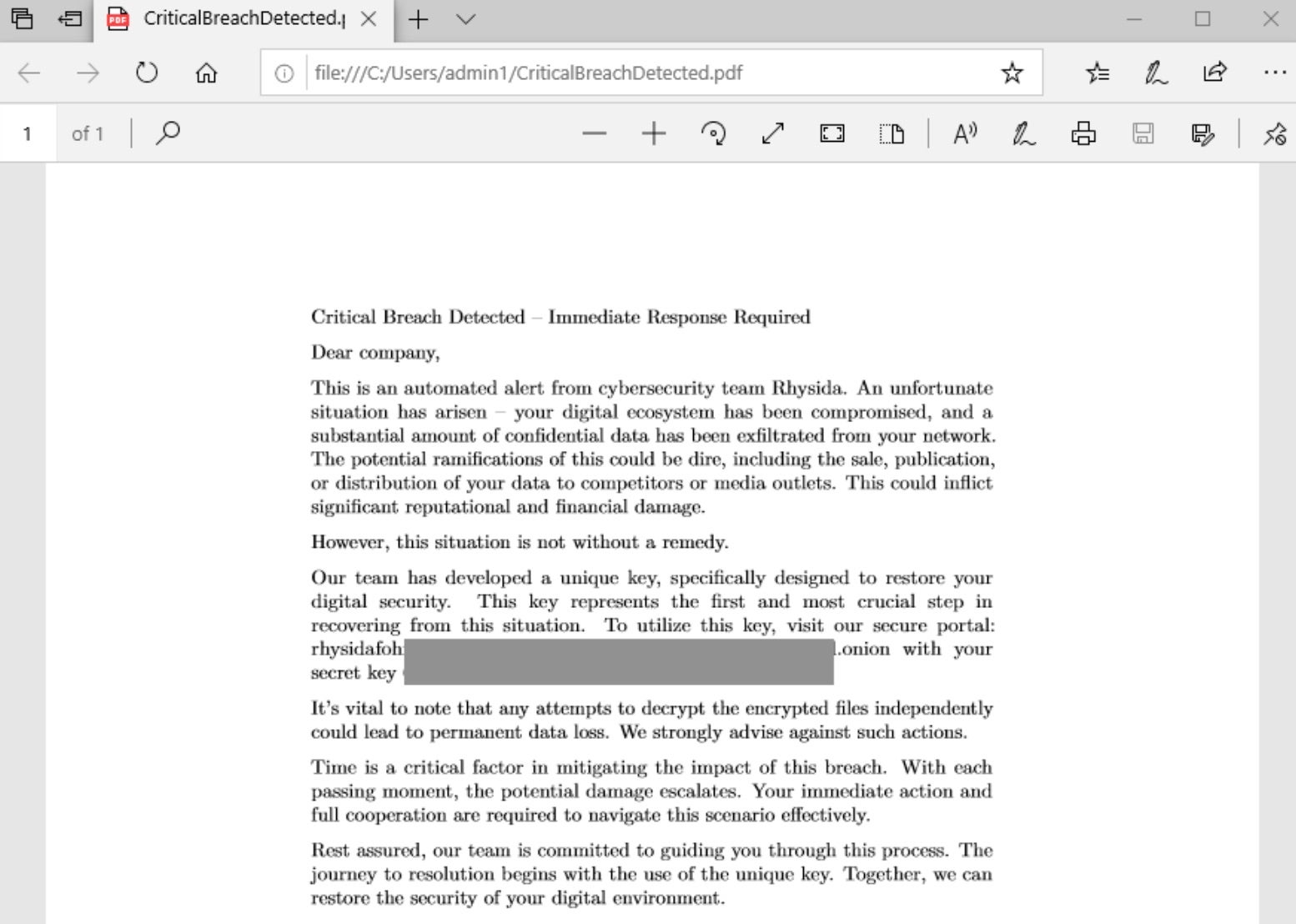
Rhysida - SentinelOne

PROUD-MAL: static analysis-based progressive framework for deep

How to Analyze Malware's Network Traffic in A Sandbox

Malware Analysis: Steps & Examples - CrowdStrike
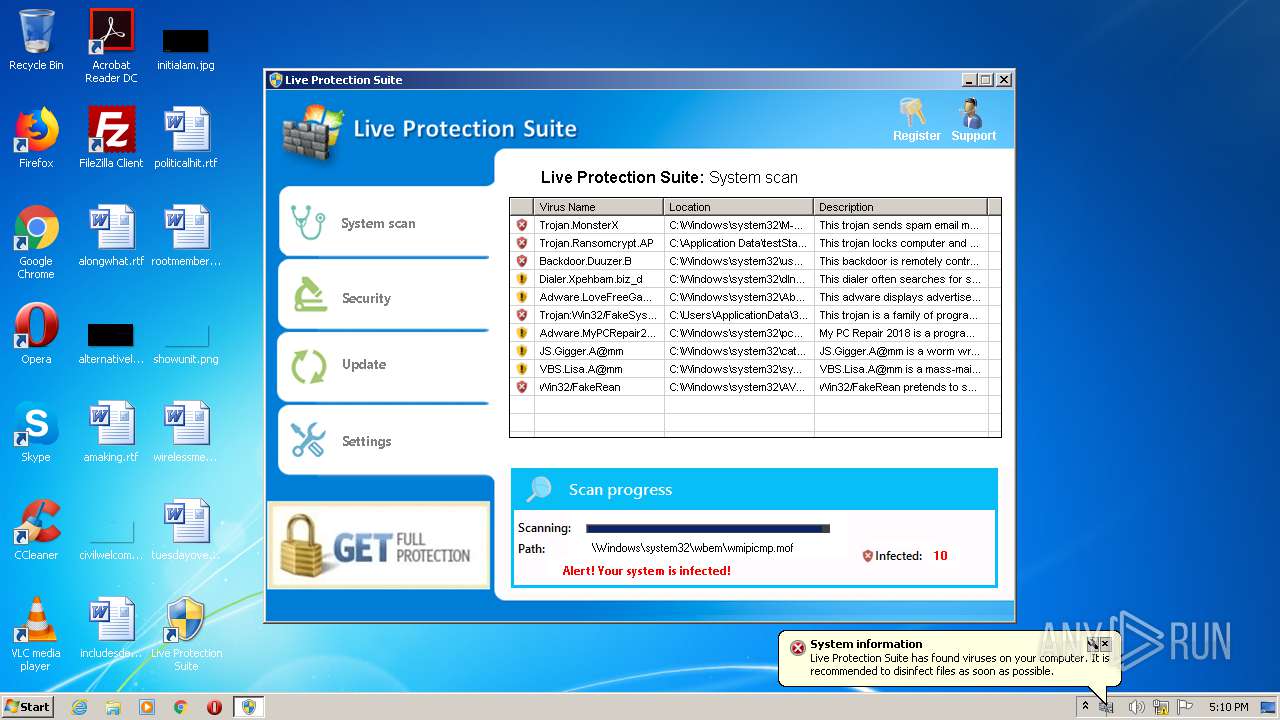
Malware analysis metasploit.bat Malicious activity

What to Include in a Malware Analysis Report
Recomendado para você
-
 Orbit Executor, Best FREE Multi Api Exploit07 abril 2025
Orbit Executor, Best FREE Multi Api Exploit07 abril 2025 -
 How to Develop a Roblox Exploit: 12 Steps (with Pictures)07 abril 2025
How to Develop a Roblox Exploit: 12 Steps (with Pictures)07 abril 2025 -
 Arceus X Neo 1.0.6 Download For Windows PC - Softlay07 abril 2025
Arceus X Neo 1.0.6 Download For Windows PC - Softlay07 abril 2025 -
Roblox Exploited with Trojans from Scripting Engine07 abril 2025
-
 Download Hydrogen Executor APK 11 for Android07 abril 2025
Download Hydrogen Executor APK 11 for Android07 abril 2025 -
 Ligmund executor|TikTok Search07 abril 2025
Ligmund executor|TikTok Search07 abril 2025 -
 roblox moment : r/robloxhackers07 abril 2025
roblox moment : r/robloxhackers07 abril 2025 -
 Exploiters Altering Game Data - Scripting Support - Developer Forum07 abril 2025
Exploiters Altering Game Data - Scripting Support - Developer Forum07 abril 2025 -
 Release, Kronos v4, More Powerful Then Fluxus07 abril 2025
Release, Kronos v4, More Powerful Then Fluxus07 abril 2025 -
 Malware analysis Malicious activity07 abril 2025
Malware analysis Malicious activity07 abril 2025
você pode gostar
-
 The Sky Is Everywhere (2022) - IMDb07 abril 2025
The Sky Is Everywhere (2022) - IMDb07 abril 2025 -
 Google AdSense: pode esta ser uma forma de renda passiva?07 abril 2025
Google AdSense: pode esta ser uma forma de renda passiva?07 abril 2025 -
 The Queen's Gambit Wallpaper, Beth Harmon and Benny Watts The queen's gambit, Queen's gambit aesthetic, Queen's gambit07 abril 2025
The Queen's Gambit Wallpaper, Beth Harmon and Benny Watts The queen's gambit, Queen's gambit aesthetic, Queen's gambit07 abril 2025 -
 Bob Marley: One Love, cinebiografia de lenda do reggae, ganha nova data e trailer07 abril 2025
Bob Marley: One Love, cinebiografia de lenda do reggae, ganha nova data e trailer07 abril 2025 -
![ALL CODES] Carrying New Gojo Raid & Giving Prizes to Subscibers](https://static-cdn.jtvnw.net/cf_vods/d1m7jfoe9zdc1j/1ddd1bd4a8dddfcc8fd2_blamspot_42009882489_1699405145//thumb/thumb0-276x155.jpg) ALL CODES] Carrying New Gojo Raid & Giving Prizes to Subscibers07 abril 2025
ALL CODES] Carrying New Gojo Raid & Giving Prizes to Subscibers07 abril 2025 -
 ArtStation - Arisu Sakayanagi07 abril 2025
ArtStation - Arisu Sakayanagi07 abril 2025 -
Plaza Colonia vs Cerro - live score, predicted lineups and H2H stats.07 abril 2025
-
 Taverna do Peregrino: Os 10 Vocalistas Mais Bonitos dos Anos 8007 abril 2025
Taverna do Peregrino: Os 10 Vocalistas Mais Bonitos dos Anos 8007 abril 2025 -
 Advance Wars – Hardcore Gaming 10107 abril 2025
Advance Wars – Hardcore Gaming 10107 abril 2025 -
 História Sodalita - Imagine Kyoujurou Rengoku - O oni do tsuzumi - História escrita por Yashiao - Spirit Fanfics e Histórias07 abril 2025
História Sodalita - Imagine Kyoujurou Rengoku - O oni do tsuzumi - História escrita por Yashiao - Spirit Fanfics e Histórias07 abril 2025