Jump Host Best Practices — Improsec
Por um escritor misterioso
Last updated 28 março 2025

Because a jump host serves at an entry point to privileged resources it is a highly sought target by adversaries. Therefore, it is important to have an increased focus on security. However hardening the jump host itself it not enough, a holistic approach is needed. In this blog, Jakob provides solid
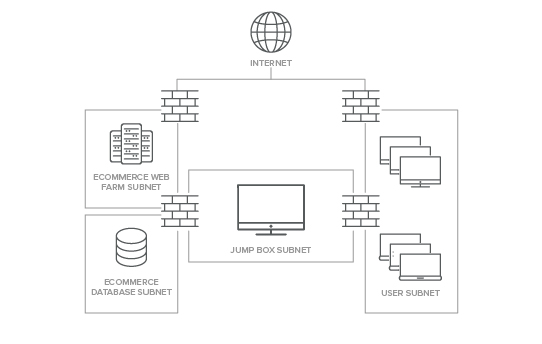
Protecting Critical Systems with Isolation and Jump Boxes

Has Anyone Enabled 2FA for A Domain Controller (Using Duo)? - IT
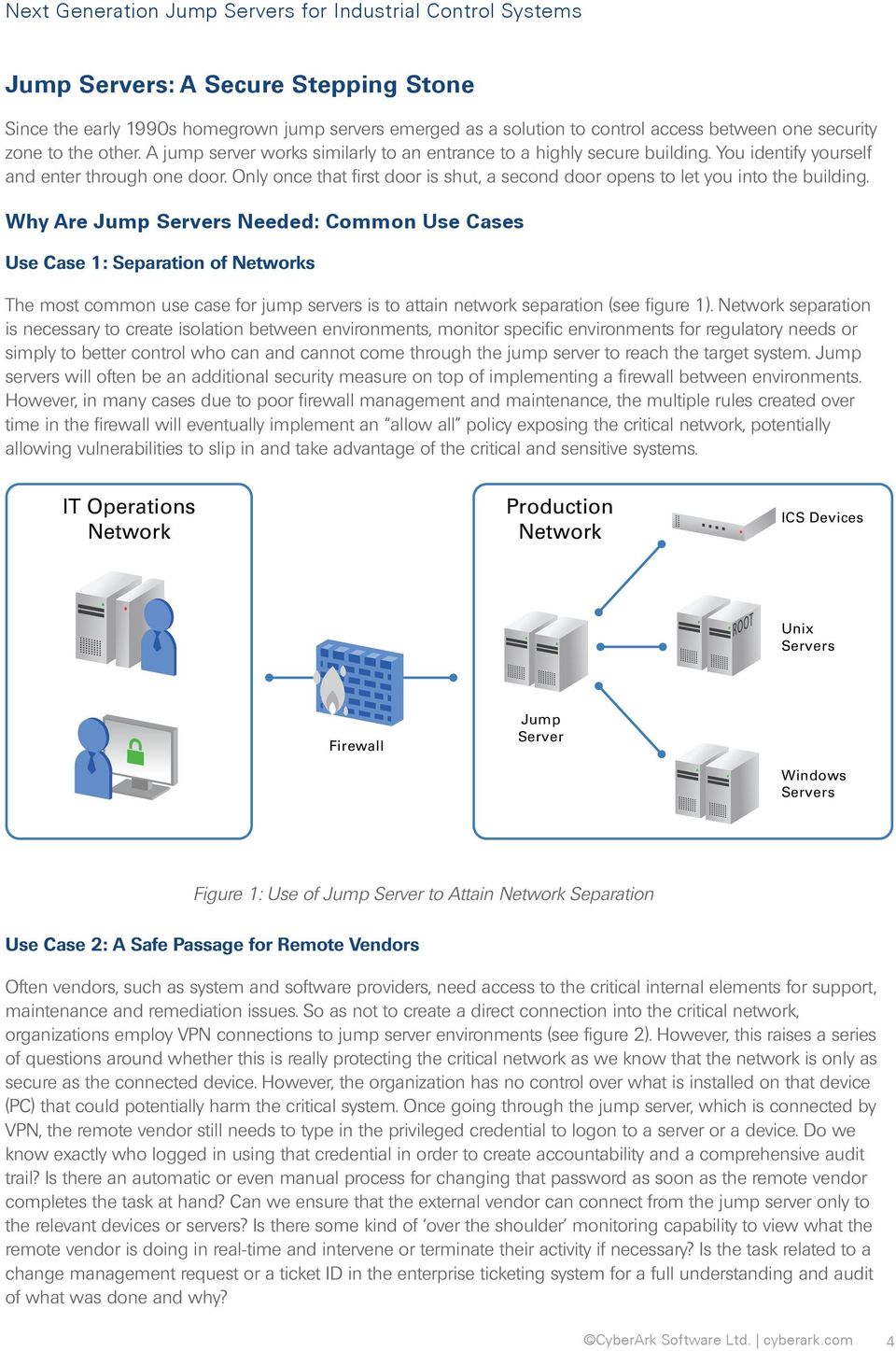
Next Generation Jump Servers for Industrial Control Systems - PDF

Jump Host Best Practices — Improsec

What Is a Jump Server? Complete Guide - Veloce
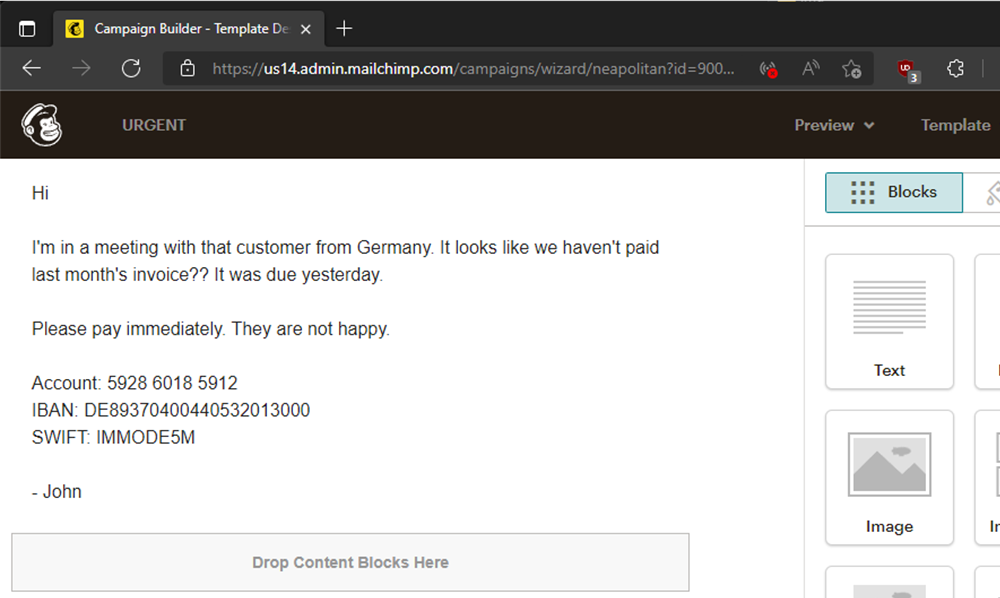
Phish'n'Chimps: mail spoofing via marketing and CRM platforms
GitHub - goldenscale/GS_GithubMirror: A Github Mirror List For GS
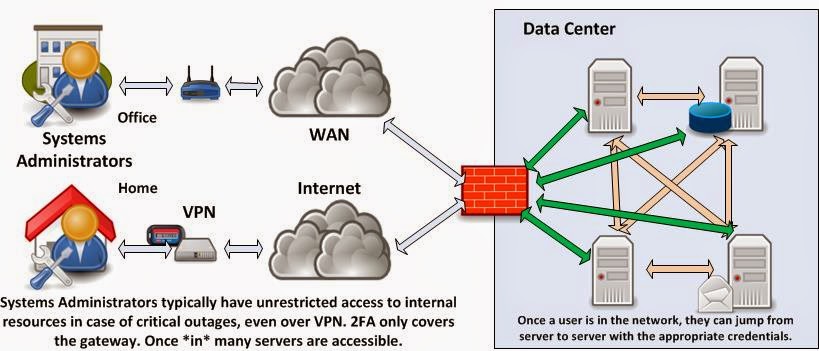
InfoSec Musings: Risk reduction through Jump Servers
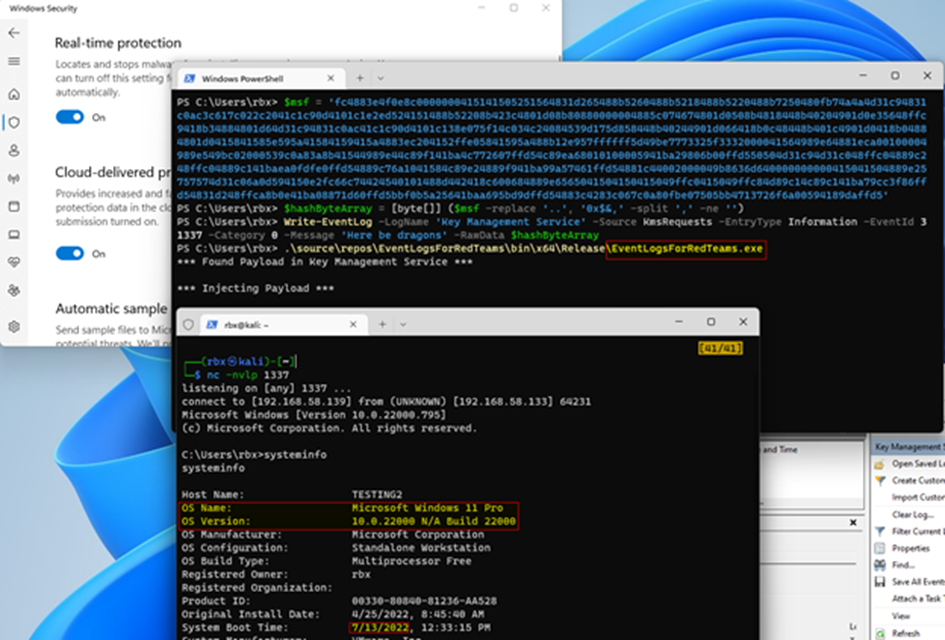
Windows Event Log Basics. Windows event logs contains logs from
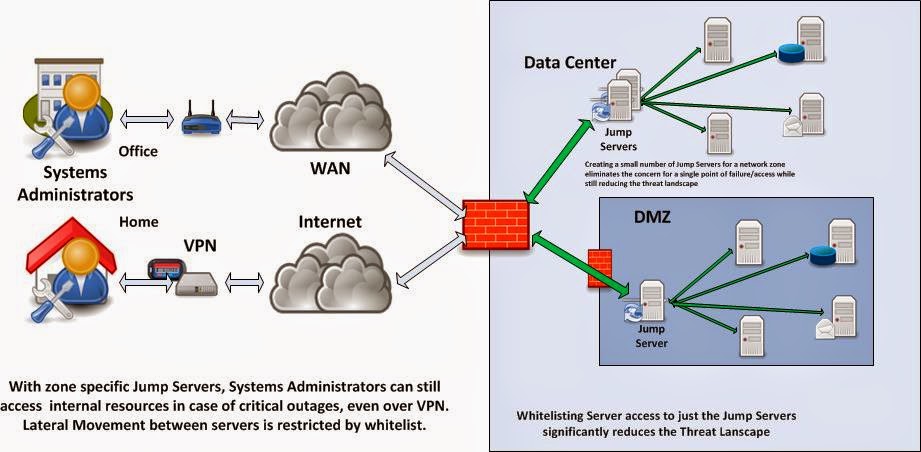
InfoSec Musings: Risk reduction through Jump Servers
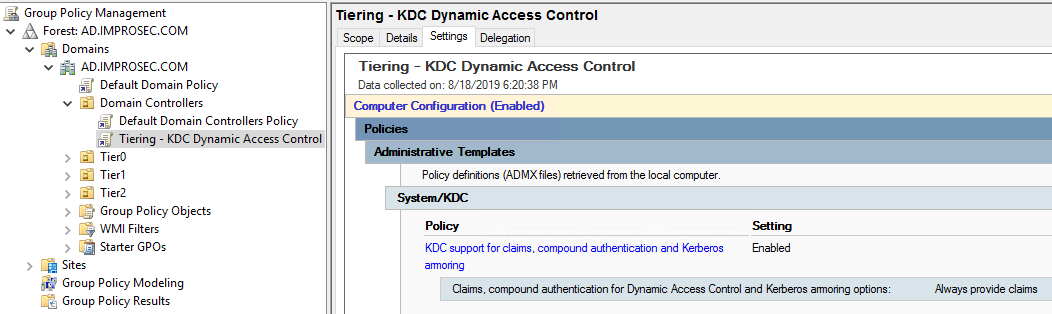
Preventing lateral movement in AD with Authentication Policies
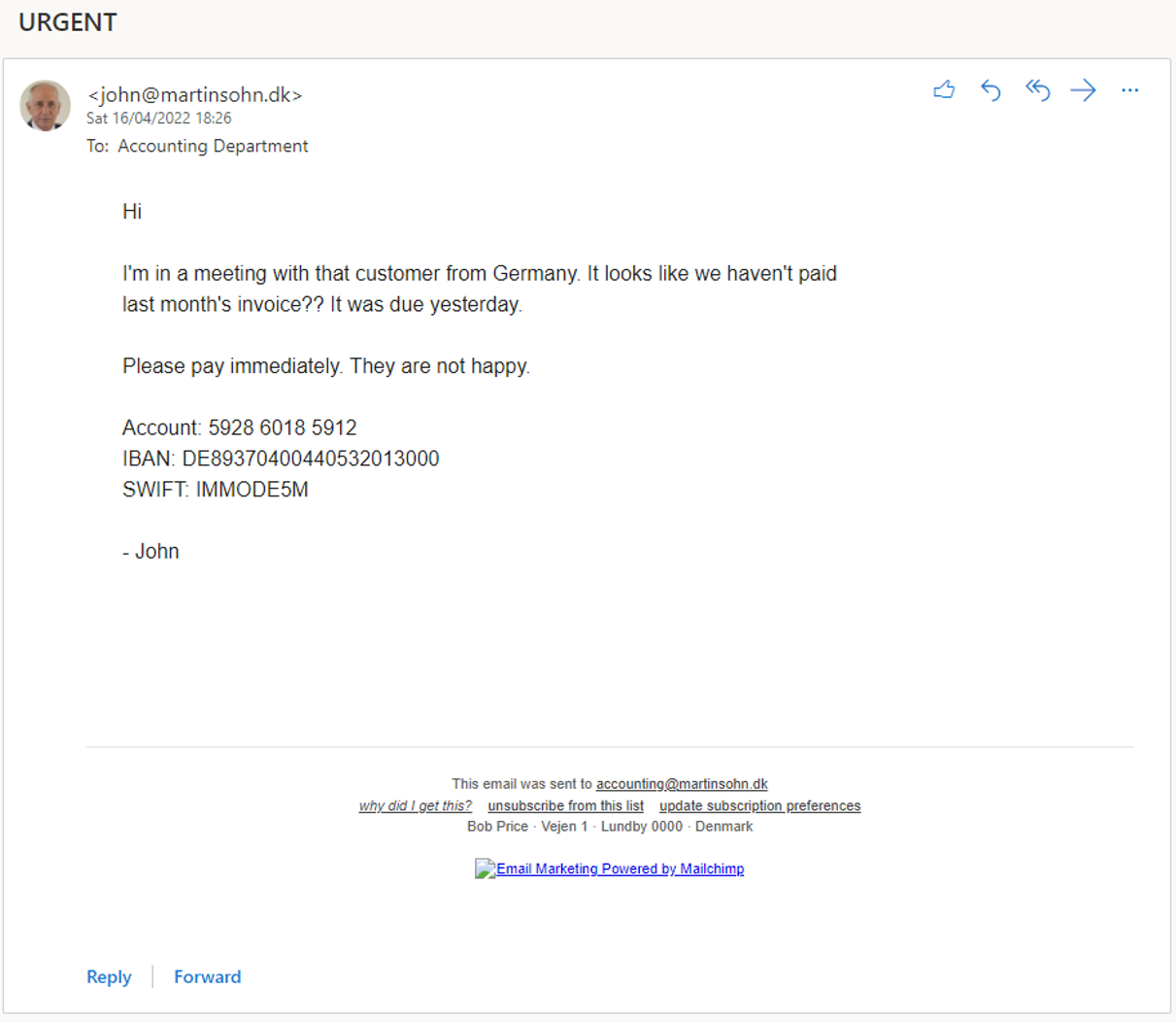
Phish'n'Chimps: mail spoofing via marketing and CRM platforms
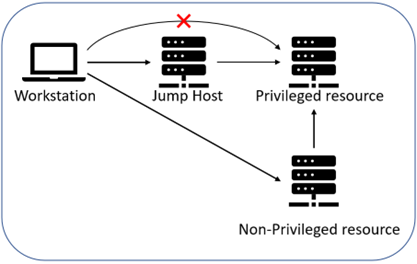
Jump Host Best Practices — Improsec
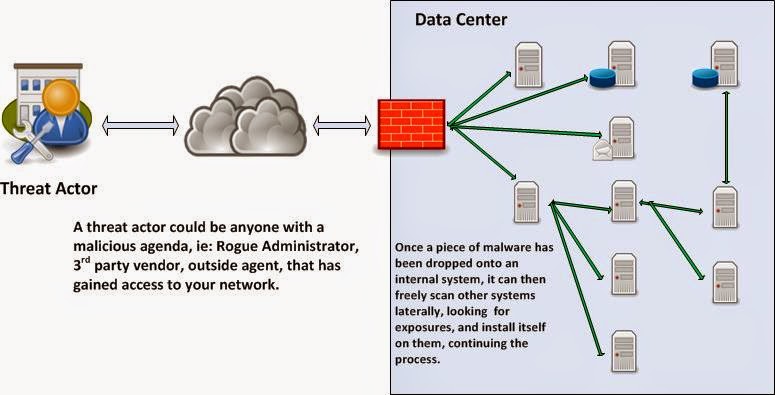
InfoSec Musings: Risk reduction through Jump Servers
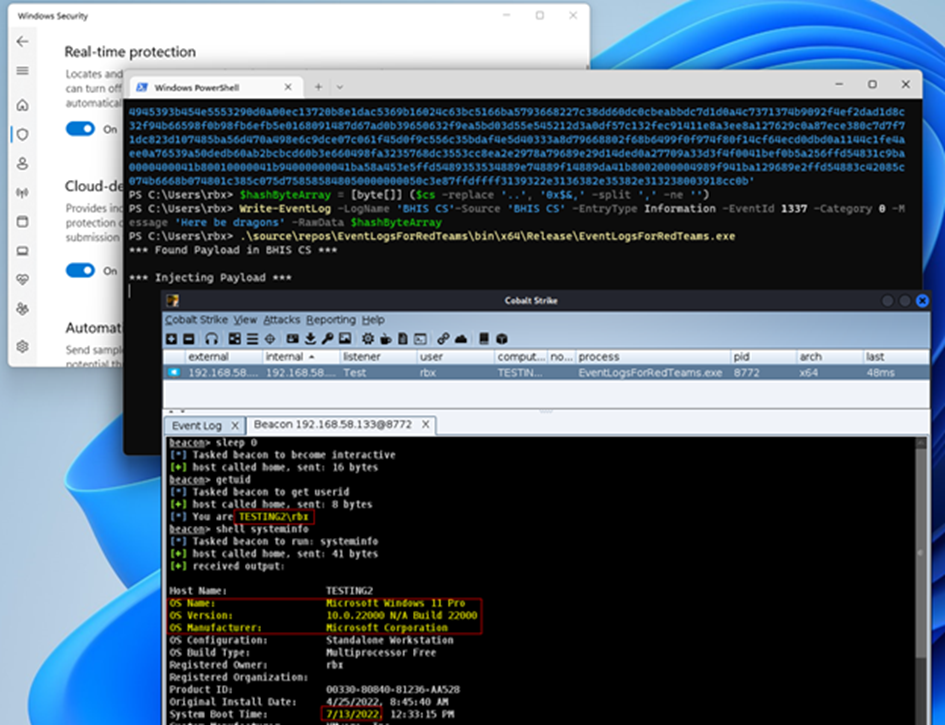
Windows Event Log Basics. Windows event logs contains logs from
Recomendado para você
-
 How to Jump Higher: 6 Exercises and Tips to Improve Your Vertical Jump28 março 2025
How to Jump Higher: 6 Exercises and Tips to Improve Your Vertical Jump28 março 2025 -
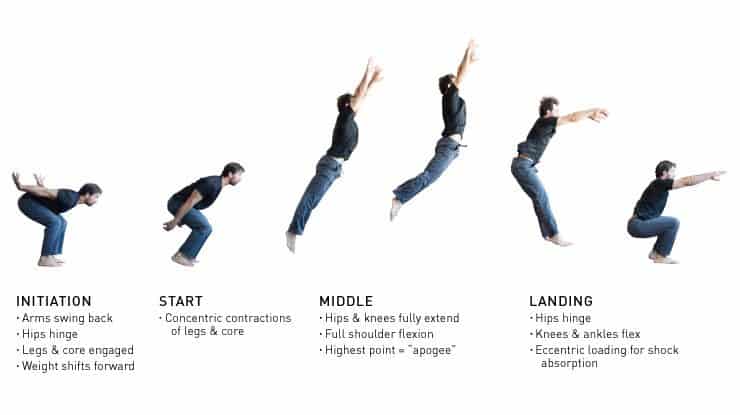 Jump Tutorial For Skill, Precision, And Power28 março 2025
Jump Tutorial For Skill, Precision, And Power28 março 2025 -
 What makes the perfect…long jump?28 março 2025
What makes the perfect…long jump?28 março 2025 -
 NBA Jump Training: Exercises to improve your vertical jump28 março 2025
NBA Jump Training: Exercises to improve your vertical jump28 março 2025 -
 Womens high jump hi-res stock photography and images - Alamy28 março 2025
Womens high jump hi-res stock photography and images - Alamy28 março 2025 -
 Jumps Images - Free Download on Freepik28 março 2025
Jumps Images - Free Download on Freepik28 março 2025 -
 10 Exercises to Improve Your Vertical Jump - Spooner Physical Therapy28 março 2025
10 Exercises to Improve Your Vertical Jump - Spooner Physical Therapy28 março 2025 -
 How to Jump Rope Like a Boxer28 março 2025
How to Jump Rope Like a Boxer28 março 2025 -
 Active Family Fun & Trampoline Park28 março 2025
Active Family Fun & Trampoline Park28 março 2025 -
 Super Jump Workout28 março 2025
Super Jump Workout28 março 2025
você pode gostar
-
 Bonzi Windows, Mac, Linux game - Indie DB28 março 2025
Bonzi Windows, Mac, Linux game - Indie DB28 março 2025 -
 New UGC Limiteds Introduce Massive Hyper-inflation Into It's28 março 2025
New UGC Limiteds Introduce Massive Hyper-inflation Into It's28 março 2025 -
Shazam! Fury of the Gods Cast Talks Superpowers and Musicals28 março 2025
-
 Here's how to bring the Y2K aesthetic to your next website28 março 2025
Here's how to bring the Y2K aesthetic to your next website28 março 2025 -
 Blazer 1997 uma das configurações de entrada do SUV Chevrolet - Carros Antigos28 março 2025
Blazer 1997 uma das configurações de entrada do SUV Chevrolet - Carros Antigos28 março 2025 -
 Okay Yokuslu: I would only drop to into Championship for West Brom28 março 2025
Okay Yokuslu: I would only drop to into Championship for West Brom28 março 2025 -
 Arsenal left to rue mistakes in 2-2 draw with Tottenham28 março 2025
Arsenal left to rue mistakes in 2-2 draw with Tottenham28 março 2025 -
 Club Penguin Island to Shut Down at the End of the Year28 março 2025
Club Penguin Island to Shut Down at the End of the Year28 março 2025 -
Paper.io 2 Mod Apk (Unlocked/God Mode) Download - StorePlay Apk28 março 2025
-
 The Revisited Meninas - The Incredible Tributes to Velasquez28 março 2025
The Revisited Meninas - The Incredible Tributes to Velasquez28 março 2025
