Tricks and COMfoolery: How Ursnif (Gozi) Evades Detection
Por um escritor misterioso
Last updated 30 março 2025

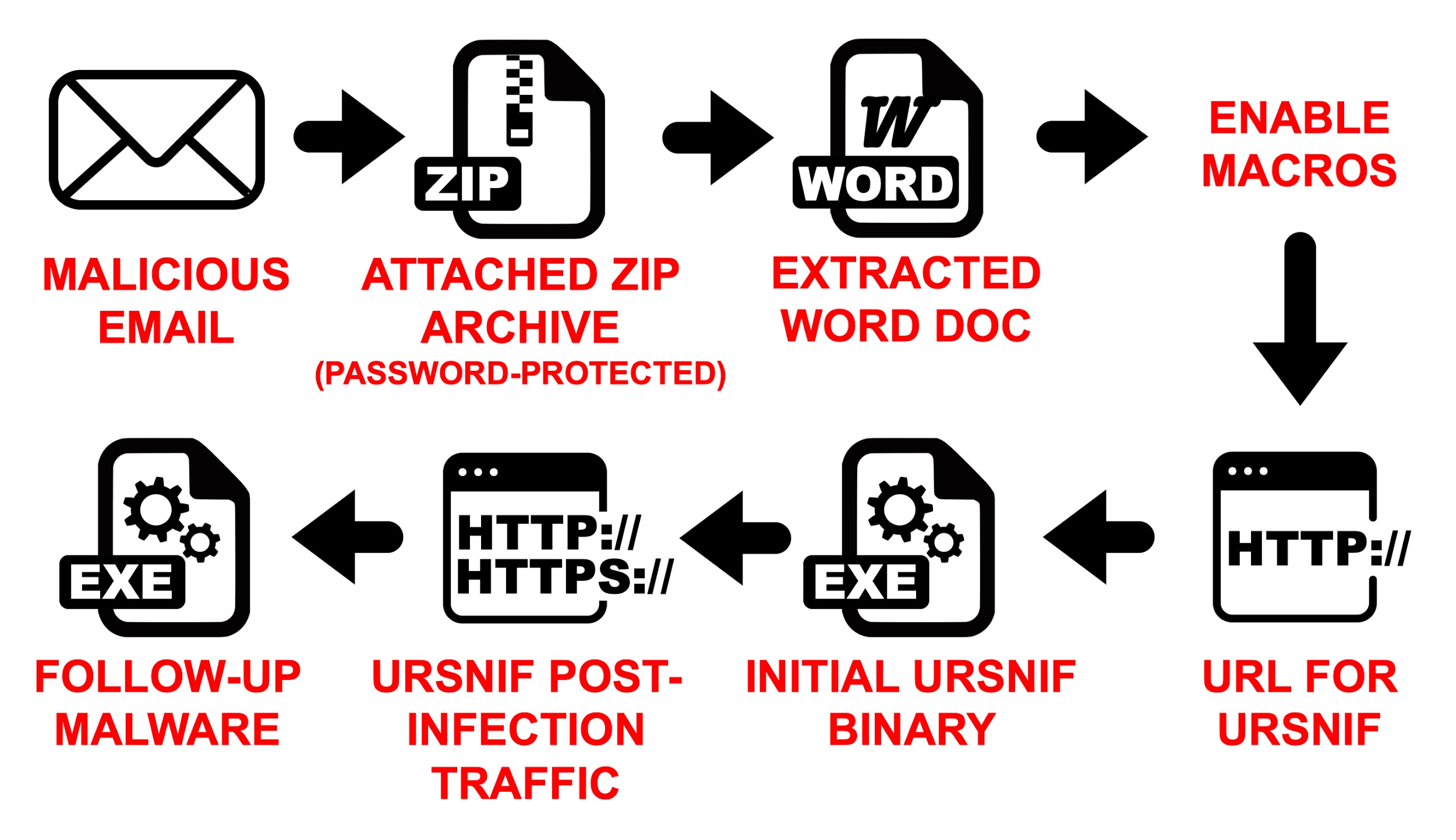
In February we saw a resurgence of Ursnif (also known as Gozi), a credential-stealing Trojan. Learn how Ursnif bypasses an attack surface reduction rule.
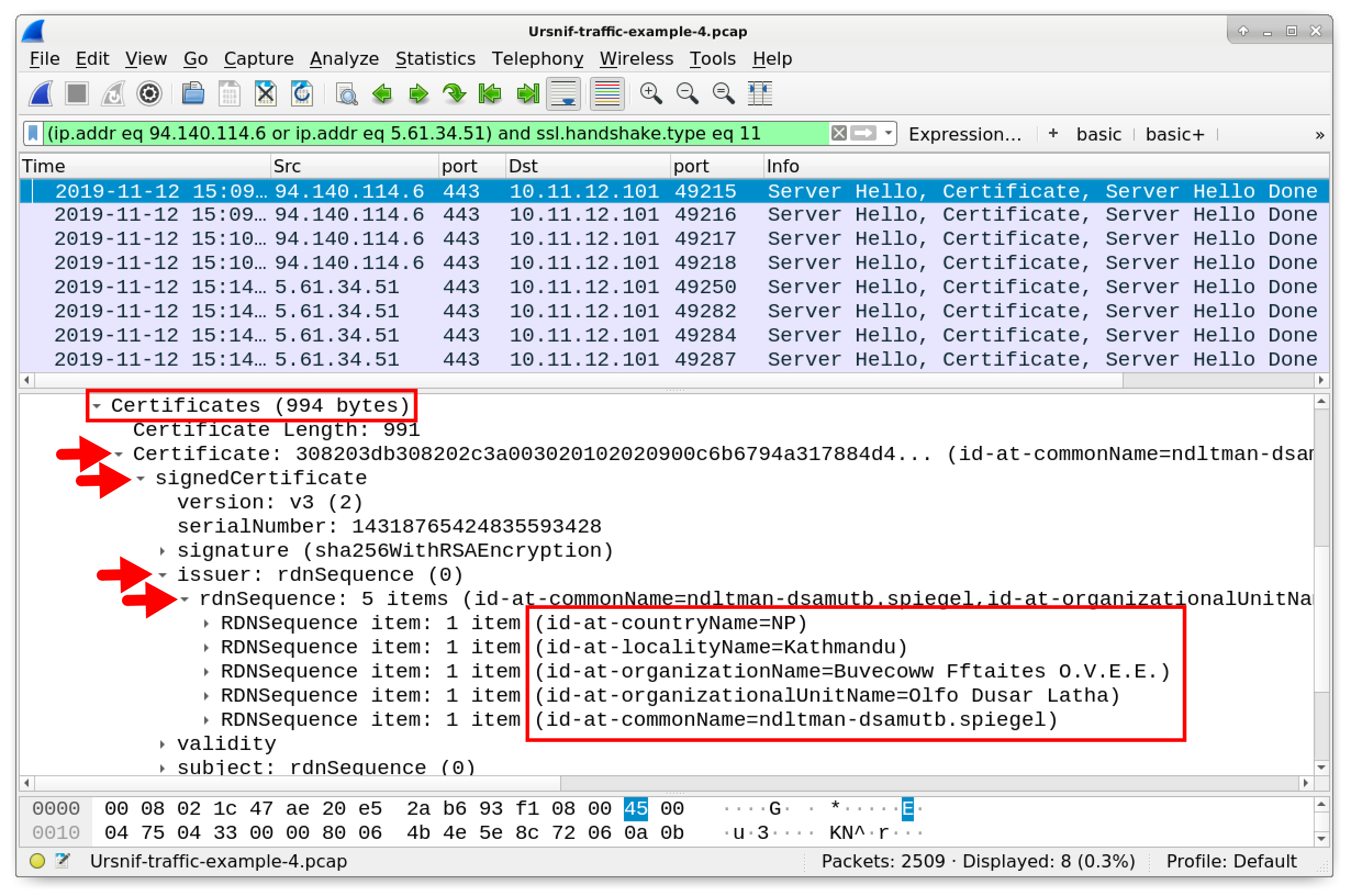
Wireshark Tutorial: Examining Ursnif Infections
Ursnif Trojan - Malware removal instructions (updated)

Windows Management Instrumentation, Technique T1047 - Enterprise
.png)
Ursnif malware switches from bank account theft to initial access
Wireshark Tutorial: Examining Ursnif Infections

Ursnif Trojan - Malware removal instructions (updated)
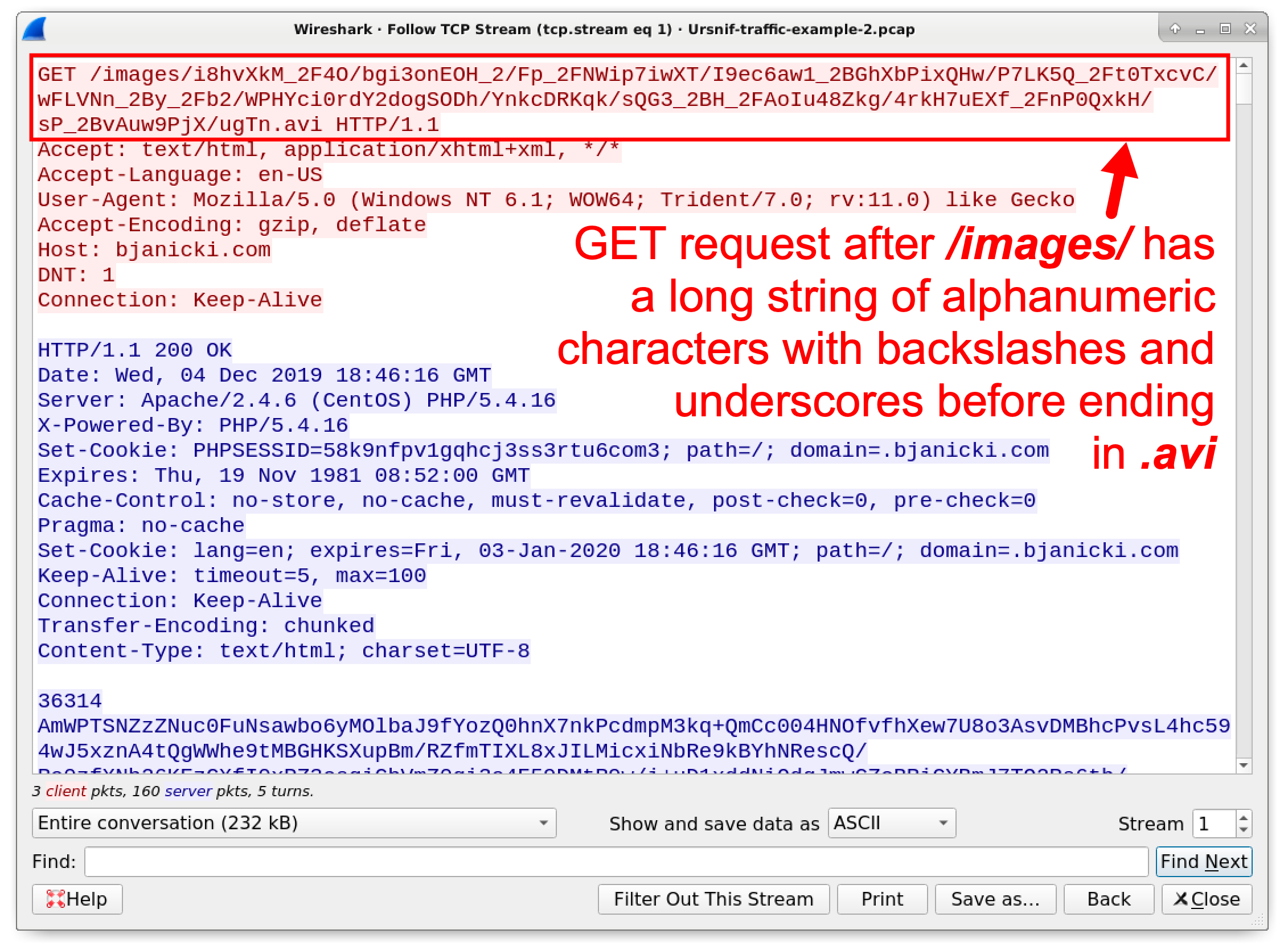
Wireshark Tutorial: Examining Ursnif Infections

Ursnif aka Gozi Malware analysis with ANY.RUN malware sandbox
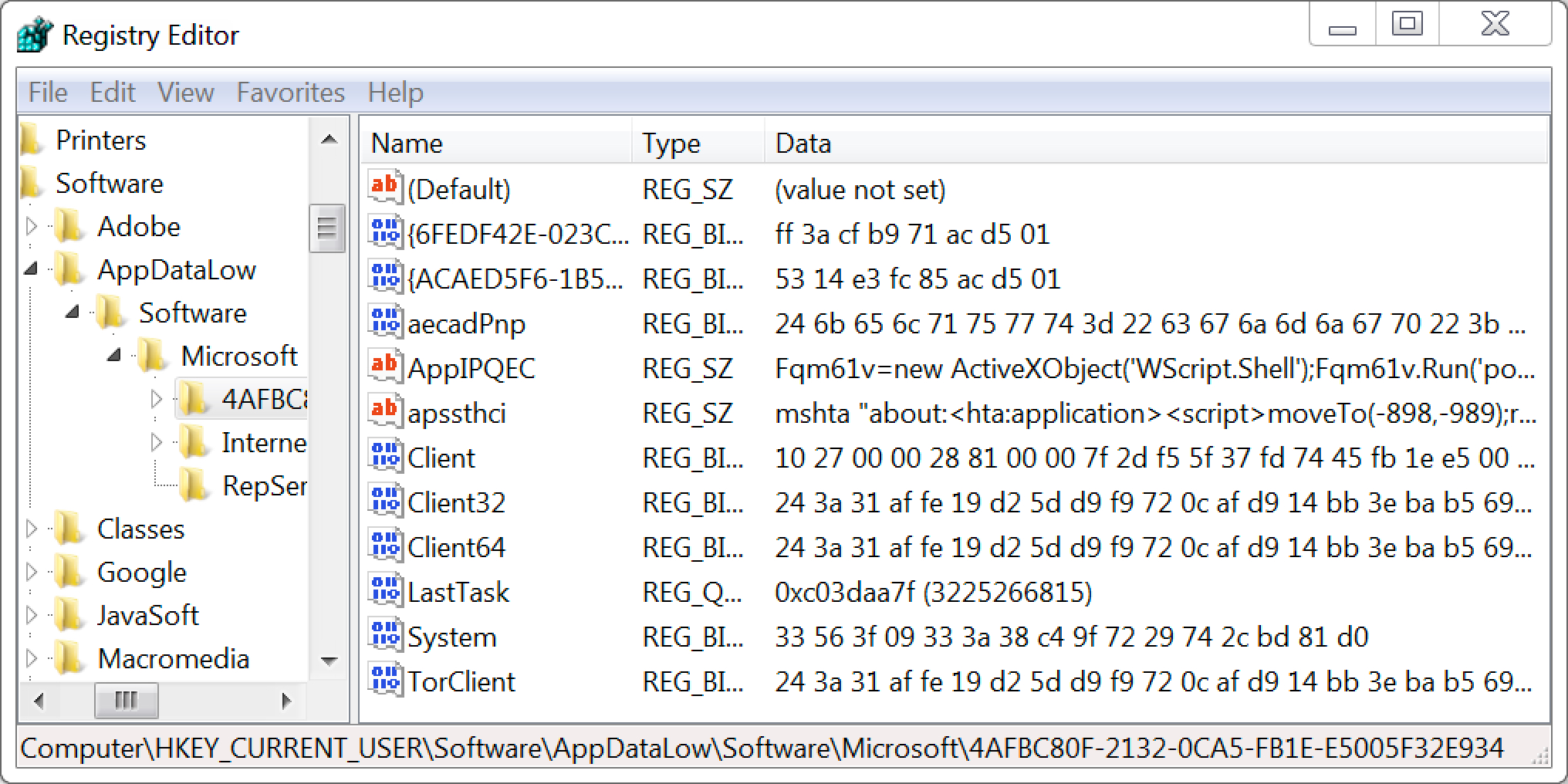
Wireshark Tutorial: Examining Ursnif Infections
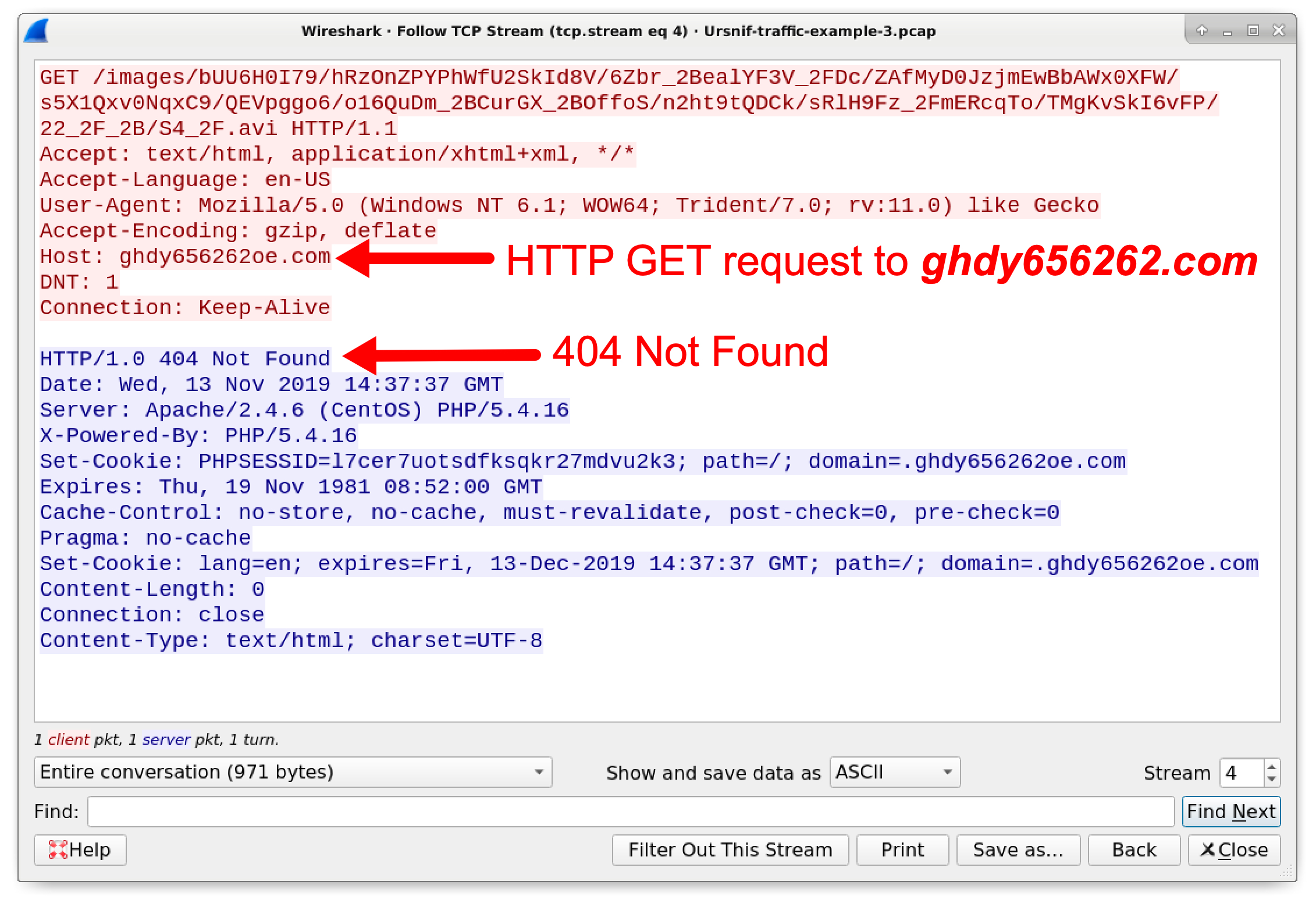
Wireshark Tutorial: Examining Ursnif Infections

Ursnif aka Gozi Malware analysis with ANY.RUN malware sandbox
Recomendado para você
-
 Evades.io in 2021.30 março 2025
Evades.io in 2021.30 março 2025 -
GitHub - ThomasGITH/Evades-Javascript-game: A clone of the popular web-game 'Evades.io30 março 2025
-
 Evades, Encantadia Wiki30 março 2025
Evades, Encantadia Wiki30 março 2025 -
Evades30 março 2025
-
 Fox Evades30 março 2025
Fox Evades30 março 2025 -
 Stream No Sin Evades His Gaze music Listen to songs, albums, playlists for free on SoundCloud30 março 2025
Stream No Sin Evades His Gaze music Listen to songs, albums, playlists for free on SoundCloud30 março 2025 -
 How Zika Virus Evades Antiviral Response of Cells30 março 2025
How Zika Virus Evades Antiviral Response of Cells30 março 2025 -
 Evades: Webster's Quotations, Facts and Phrases : : Books30 março 2025
Evades: Webster's Quotations, Facts and Phrases : : Books30 março 2025 -
![Google Looker Evades, Email Scam Collaboration, Firefox Zero-Day Patch Cybersecurity News [September 11, 2023] - DuoCircle](https://www.duocircle.com/wp-content/uploads/2023/09/what-is-dmarc.jpg) Google Looker Evades, Email Scam Collaboration, Firefox Zero-Day Patch Cybersecurity News [September 11, 2023] - DuoCircle30 março 2025
Google Looker Evades, Email Scam Collaboration, Firefox Zero-Day Patch Cybersecurity News [September 11, 2023] - DuoCircle30 março 2025 -
 Bud's Jacket: An American Flyer Evades The Nazis in Occupied France30 março 2025
Bud's Jacket: An American Flyer Evades The Nazis in Occupied France30 março 2025
você pode gostar
-
 L.A. Woman (song) - Wikipedia30 março 2025
L.A. Woman (song) - Wikipedia30 março 2025 -
 Ninja Tag – HeyBuddy Club30 março 2025
Ninja Tag – HeyBuddy Club30 março 2025 -
Conjunto de Roupas para Boneca Bebê Reborn Menino com tamanho de30 março 2025
-
 BLACKBEARD SHOWCASE IN ANIME ADVENTURES! - BiliBili30 março 2025
BLACKBEARD SHOWCASE IN ANIME ADVENTURES! - BiliBili30 março 2025 -
 World Champion Carlsen's actions impact reputation of his colleagues, damages game: FIDE President30 março 2025
World Champion Carlsen's actions impact reputation of his colleagues, damages game: FIDE President30 março 2025 -
 Andrew Belle Lyrics30 março 2025
Andrew Belle Lyrics30 março 2025 -
 PISTA INFANTIL CARRINHO ESTACIONAMENTO POSTO GASOLINA HOT WHELLS ELEVADOR HELIPONTO OFICINA EM MADEIRA30 março 2025
PISTA INFANTIL CARRINHO ESTACIONAMENTO POSTO GASOLINA HOT WHELLS ELEVADOR HELIPONTO OFICINA EM MADEIRA30 março 2025 -
 Dead Space' Remake Review - Could Dead Space Be Next Last of Us?30 março 2025
Dead Space' Remake Review - Could Dead Space Be Next Last of Us?30 março 2025 -
 Ajuda com wallpapers Dragon Ball Oficial™ Amino30 março 2025
Ajuda com wallpapers Dragon Ball Oficial™ Amino30 março 2025 -
 Games like Hotel Dash Suite Success • Games similar to Hotel Dash30 março 2025
Games like Hotel Dash Suite Success • Games similar to Hotel Dash30 março 2025

