GootBot - Gootloader's new approach to post-exploitation
Por um escritor misterioso
Last updated 31 março 2025
IBM X-Force discovered a new variant of Gootloader — the "GootBot" implant. Learn more about this and how to combat it.

Three Lessons from the Target Hack of Encrypted PIN Data - Security Intelligence

Gootloader's “mothership” controls malicious content – Sophos News
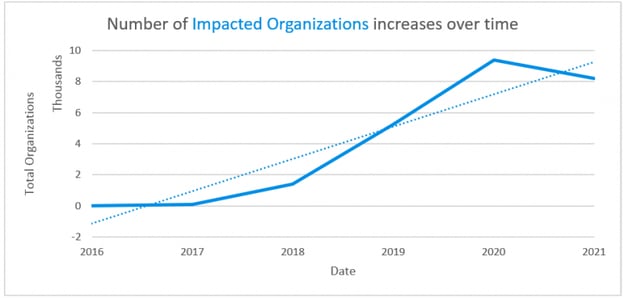
The Rise of Post-Exploitation Attack Frameworks

Episode 002: In the Boardroom - Security Intelligence
38 Million Reasons to use Cryptography for Business - Security Intelligence

Prashant Uniyal on LinkedIn: GootBot – Gootloader's new approach to post- exploitation
GootBot: A Stealthy Game Changer in Malware - PureVPN Blog

eSentire GootLoader Expands its Payloads Infecting a Law Firm with…
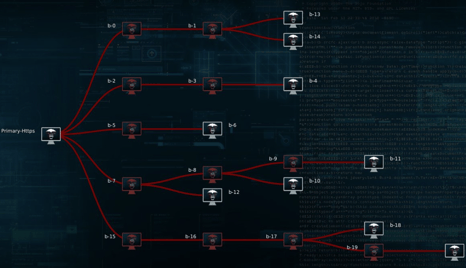
The Rise of Post-Exploitation Attack Frameworks
Recomendado para você
-
 Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG31 março 2025
Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG31 março 2025 -
 Spoofer Redengine Semanal - Others - DFG31 março 2025
Spoofer Redengine Semanal - Others - DFG31 março 2025 -
 James the Red Engine, Movie Spoof Films Wikia31 março 2025
James the Red Engine, Movie Spoof Films Wikia31 março 2025 -
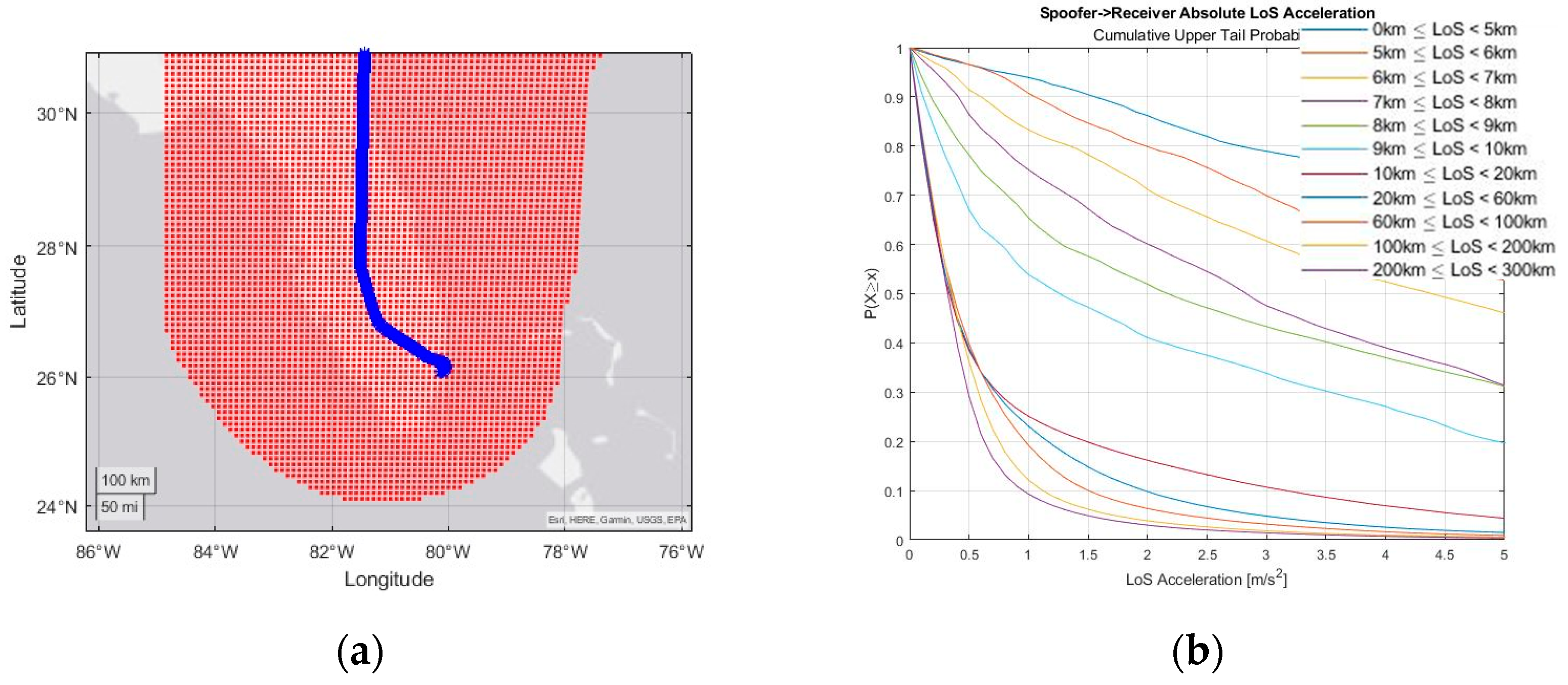 Engineering Proceedings, Free Full-Text31 março 2025
Engineering Proceedings, Free Full-Text31 março 2025 -
Red Engine Un Ban31 março 2025
-
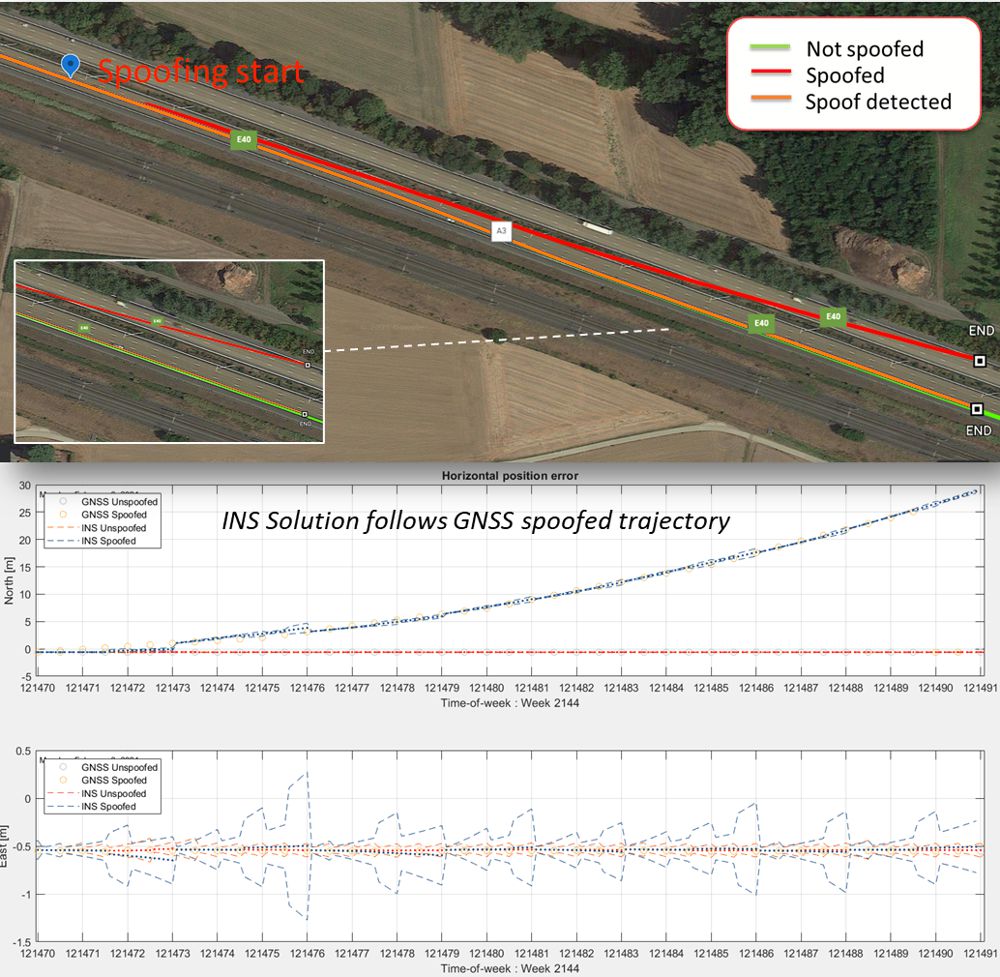 Secure GPS receivers are crucial for GNSS/INS systems - Highways Today31 março 2025
Secure GPS receivers are crucial for GNSS/INS systems - Highways Today31 março 2025 -
![Release] Spoofer](https://imgur.com/7tgB7vv.png) Release] Spoofer31 março 2025
Release] Spoofer31 março 2025 -
Cracked Hwid Spoofer31 março 2025
-
 redENGINE – FiveM Spoofer31 março 2025
redENGINE – FiveM Spoofer31 março 2025 -
 Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's31 março 2025
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's31 março 2025
você pode gostar
-
 Time Travel!!!⏰ - AdriWaterGirl15 - Wattpad31 março 2025
Time Travel!!!⏰ - AdriWaterGirl15 - Wattpad31 março 2025 -
 House of the Dragon' Season 2: Update, Cast & Release Date31 março 2025
House of the Dragon' Season 2: Update, Cast & Release Date31 março 2025 -
Anime Shiroi - Fall 2023 on Instagram: Preview episode 14 anime31 março 2025
-
 League Of Legends League of legends, Topper de bolo, Topo de bolo31 março 2025
League Of Legends League of legends, Topper de bolo, Topo de bolo31 março 2025 -
 Jogos do Bichinho: Como se Divertir com Animais Virtuais31 março 2025
Jogos do Bichinho: Como se Divertir com Animais Virtuais31 março 2025 -
 Barbie 2016: Quem precisa da Barbie, tenha o corpo que tiver?, Opinião31 março 2025
Barbie 2016: Quem precisa da Barbie, tenha o corpo que tiver?, Opinião31 março 2025 -
 Williams Racing Report: Close to points after an unfortunate São Paulo GP31 março 2025
Williams Racing Report: Close to points after an unfortunate São Paulo GP31 março 2025 -
 Pin on Takt Op. Destiny31 março 2025
Pin on Takt Op. Destiny31 março 2025 -
 Crossing Swords - Wikipedia31 março 2025
Crossing Swords - Wikipedia31 março 2025 -
 MINUTO IFBA #8231 março 2025
MINUTO IFBA #8231 março 2025