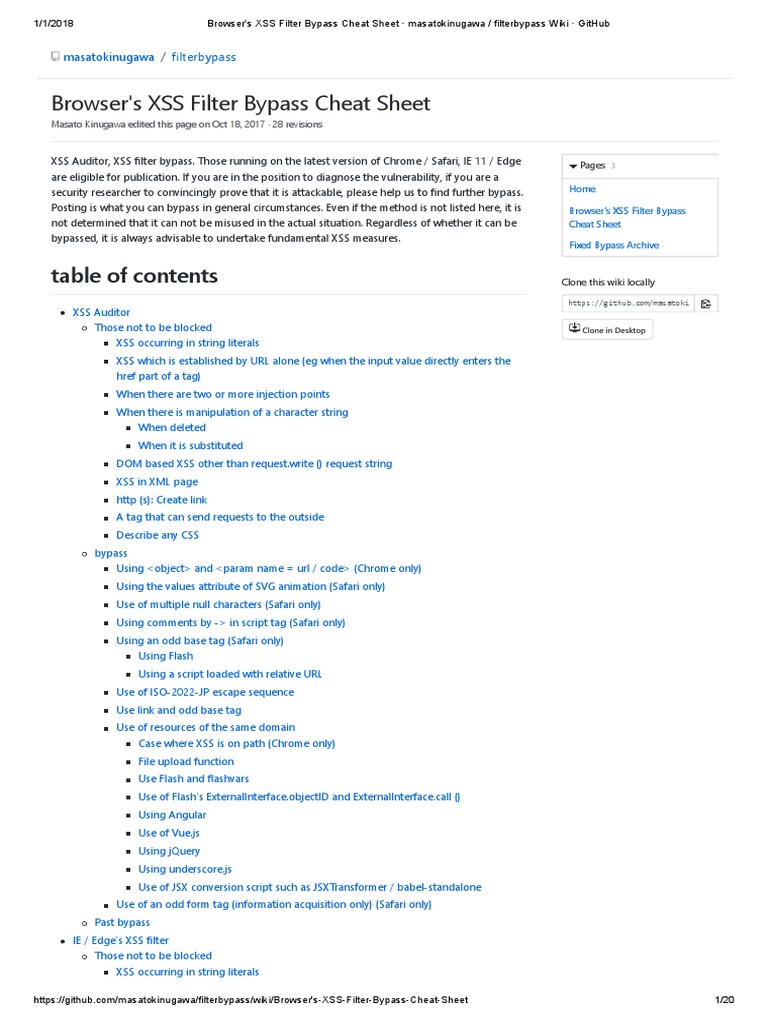
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 31 março 2025
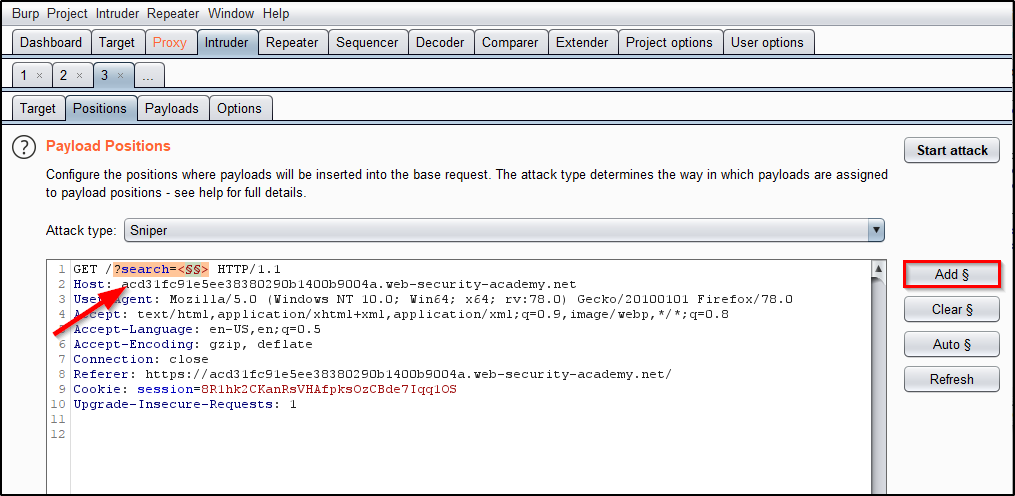
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

XSS and CSRF with HTML5
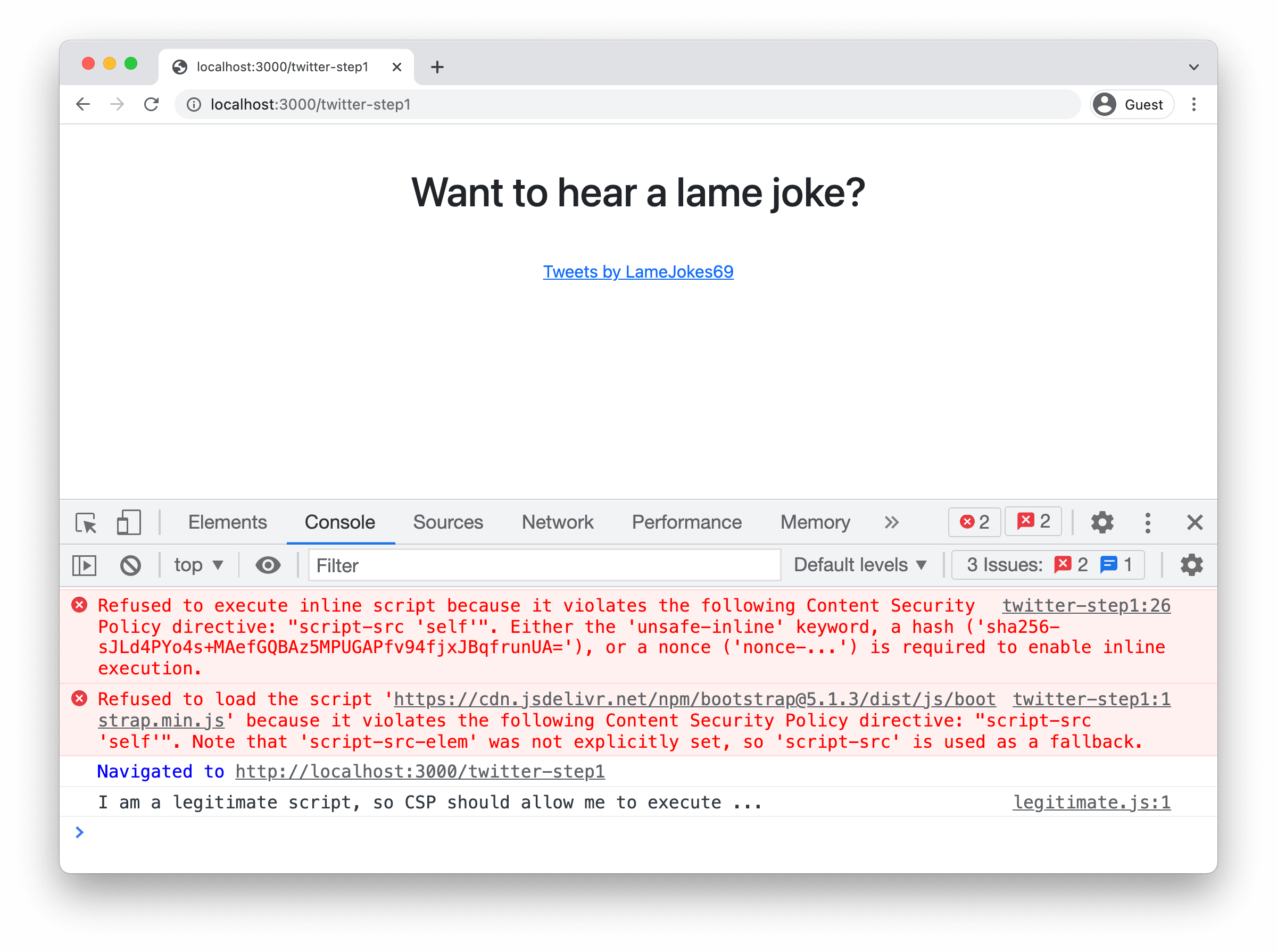
Defending against XSS with CSP

A pen tester's guide to Content Security Policy - Outpost24

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Using an Interactive Cross-site Scripting Backdoor
Google XSS Game Exploit & Patch
Reflected XSS using Double Encoding - HACKLIDO
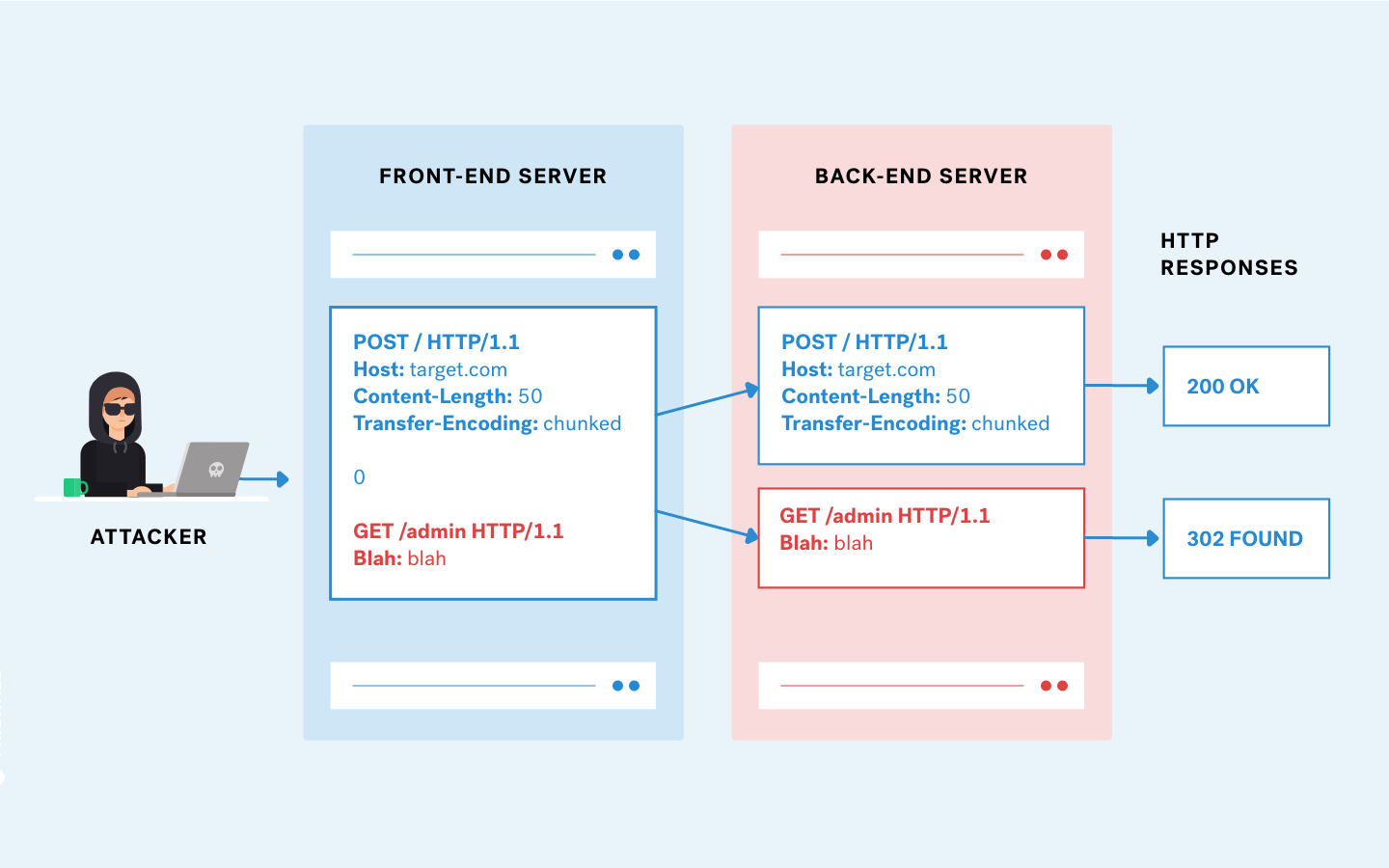
A Pentester's Guide to Cross-Site Scripting (XSS)

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
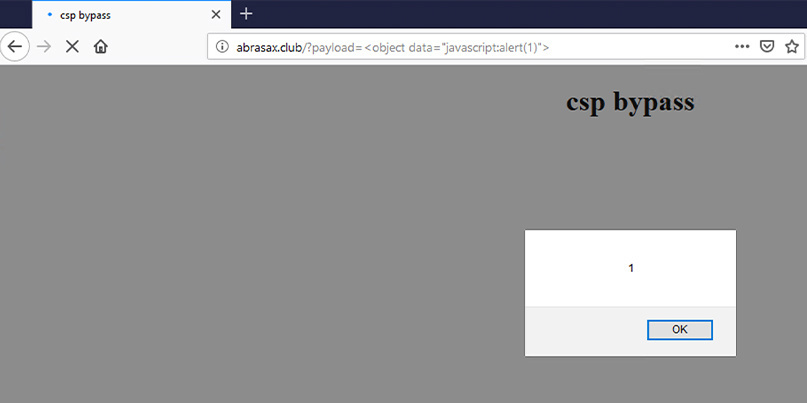
Firefox vulnerable to trivial CSP bypass
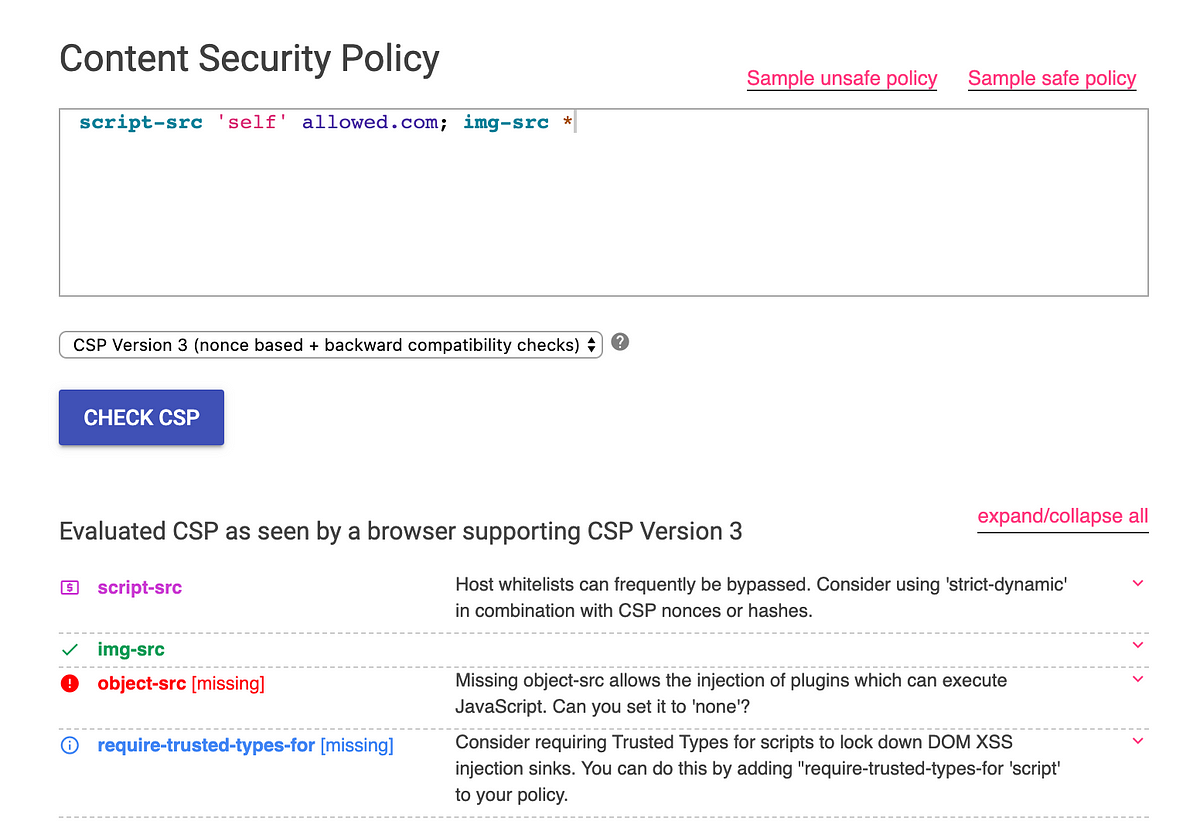
Content Security Bypass Techniques to perform XSS

ZTWeb: Cross site scripting detection based on zero trust - ScienceDirect
Recomendado para você
-
 Cross Site Scripting (XSS) - Payload Generator31 março 2025
Cross Site Scripting (XSS) - Payload Generator31 março 2025 -
XSS (Cross Site Scripting) Prevention Cheat Sheet, PDF, Html31 março 2025
-
 XSS (Cross Site Scripting) Prevention Cheat Sheet at Open Web Application Security Project31 março 2025
XSS (Cross Site Scripting) Prevention Cheat Sheet at Open Web Application Security Project31 março 2025 -
GitHub - PortSwigger/xss-cheatsheet31 março 2025
-
Xss Cheat Sheet 2016, PDF, Html Element31 março 2025
-
 XSS Cheat Sheet V. 201831 março 2025
XSS Cheat Sheet V. 201831 março 2025 -
 Bypassing Modern WAF's XSS Filters - Cheat Sheet - Miscellaneous Ramblings of a Cyber Security Researcher31 março 2025
Bypassing Modern WAF's XSS Filters - Cheat Sheet - Miscellaneous Ramblings of a Cyber Security Researcher31 março 2025 -
Browser's XSS Filter Bypass Cheat Sheet Masatokinugawa - Filterbypass Wiki GitHub, PDF, Html Element31 março 2025
-
 Apache Security Against Cross-Site Scripting31 março 2025
Apache Security Against Cross-Site Scripting31 março 2025 -
 Building Advanced XSS Vectors31 março 2025
Building Advanced XSS Vectors31 março 2025
você pode gostar
-
 What is the Hare Krishna Movement? (ISKCON) – Bishop's Encyclopedia of Religion, Society and Philosophy31 março 2025
What is the Hare Krishna Movement? (ISKCON) – Bishop's Encyclopedia of Religion, Society and Philosophy31 março 2025 -
 The Eye of Glaurung PRINTABLE Art Fantasy Illustration31 março 2025
The Eye of Glaurung PRINTABLE Art Fantasy Illustration31 março 2025 -
Respondendo a @pr3tty.anaa_ 13:51/ id de skins y2k no brookaven a31 março 2025
-
glitch trap|TikTok Search31 março 2025
-
 Desenho de SASUKE VS NARUTO pintado e colorido por Usuário não31 março 2025
Desenho de SASUKE VS NARUTO pintado e colorido por Usuário não31 março 2025 -
 Isekai Meikyuu de Harem wo Episode 5 Sub Indo Uncensored - Nonton Anime ID31 março 2025
Isekai Meikyuu de Harem wo Episode 5 Sub Indo Uncensored - Nonton Anime ID31 março 2025 -
 Getting the most out of the RPCS3 PS3 emulator for GT5 and GT631 março 2025
Getting the most out of the RPCS3 PS3 emulator for GT5 and GT631 março 2025 -
 SEGA SATURN DESIRE Japan JP GAME31 março 2025
SEGA SATURN DESIRE Japan JP GAME31 março 2025 -
 Lords of the Fallen delivers a gameplay overview trailer weeks out from its release — Maxi-Geek31 março 2025
Lords of the Fallen delivers a gameplay overview trailer weeks out from its release — Maxi-Geek31 março 2025 -
 Alfabeto de livro de colorir de animais isolado no fundo branco31 março 2025
Alfabeto de livro de colorir de animais isolado no fundo branco31 março 2025