Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 31 março 2025

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called
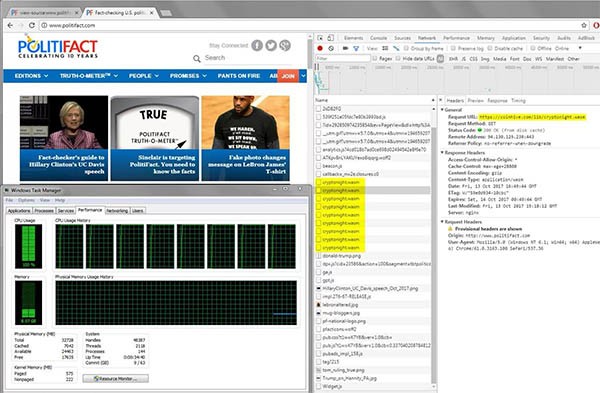
How Hackers Use Cryptojacking Malware to Take Over Computers to
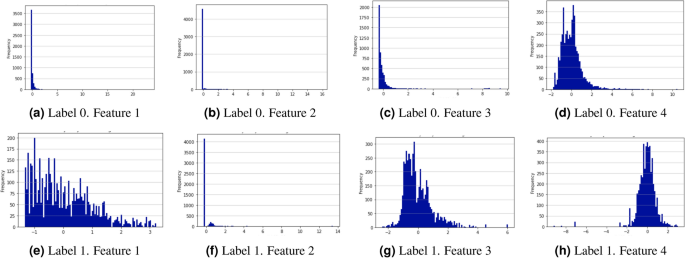
Synthetic flow-based cryptomining attack generation through

Other 3,700 MikroTik Routers compromised in cryptoJacking campaigns
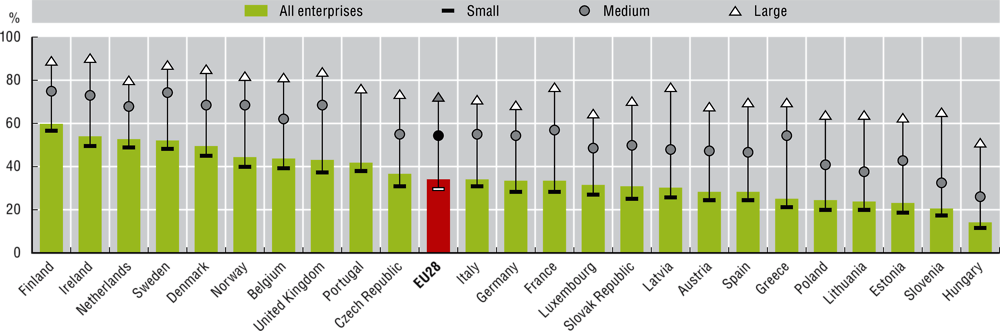
Chapter 7. Digital security OECD Digital Economy Outlook 2020
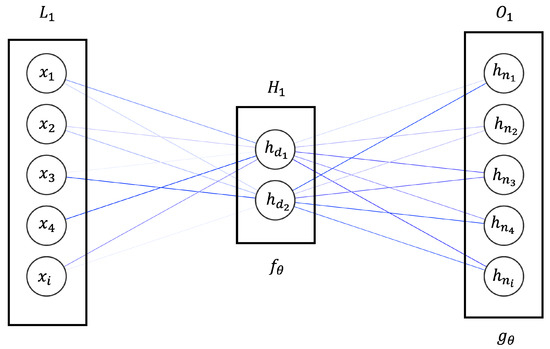
Applied Sciences, Free Full-Text

MrbMiner cryptojacking campaign linked to Iranian software firm

What is cryptojacking?Risks of cryptojacking attacks,Threat, Impacts

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs

30 Docker images downloaded 20M times in cryptojacking attacks
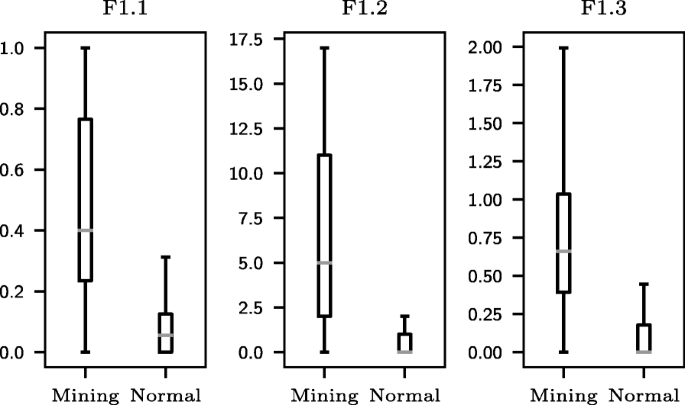
Detection of illicit cryptomining using network metadata
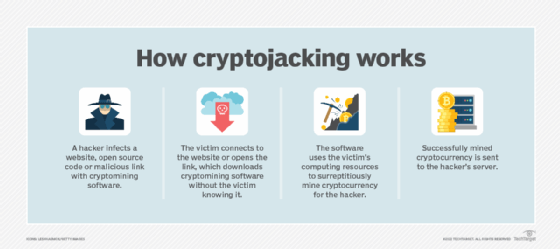
What is Cryptojacking? Detection and Preventions Techniques

How not to get milked by the cash cow of cryptojacking
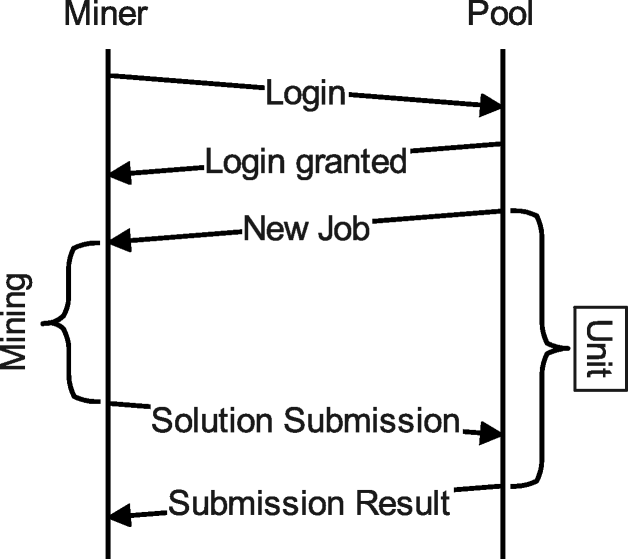
Detection of illicit cryptomining using network metadata

What You Must Know About Cryptojacking in 2022

ETL2020-Cryptojacking e BOOK EN- Enisa Amenaza #15 - From January
Recomendado para você
-
 MinerBlock Alternatives and Similar Apps31 março 2025
MinerBlock Alternatives and Similar Apps31 março 2025 -
 New year, new browser. Opera 50 introduces anti-Bitcoin mining tool - Blog31 março 2025
New year, new browser. Opera 50 introduces anti-Bitcoin mining tool - Blog31 março 2025 -
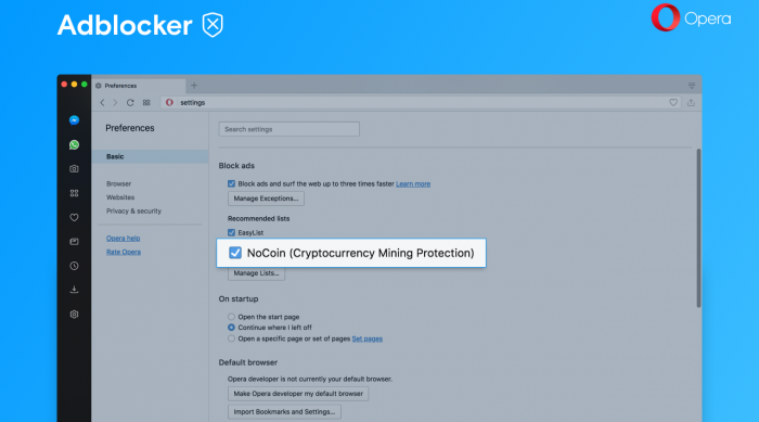 Opera adds anti-cryptocurrency mining feature to mobile browsers31 março 2025
Opera adds anti-cryptocurrency mining feature to mobile browsers31 março 2025 -
 Listen to NASA Helps Design Rescue Capsule for Chilean Miners31 março 2025
Listen to NASA Helps Design Rescue Capsule for Chilean Miners31 março 2025 -
 How Bitcoin Mining Works31 março 2025
How Bitcoin Mining Works31 março 2025 -
 Miner blockers excited about potential record31 março 2025
Miner blockers excited about potential record31 março 2025 -
 Bitcoin Home Mining Network Privacy31 março 2025
Bitcoin Home Mining Network Privacy31 março 2025 -
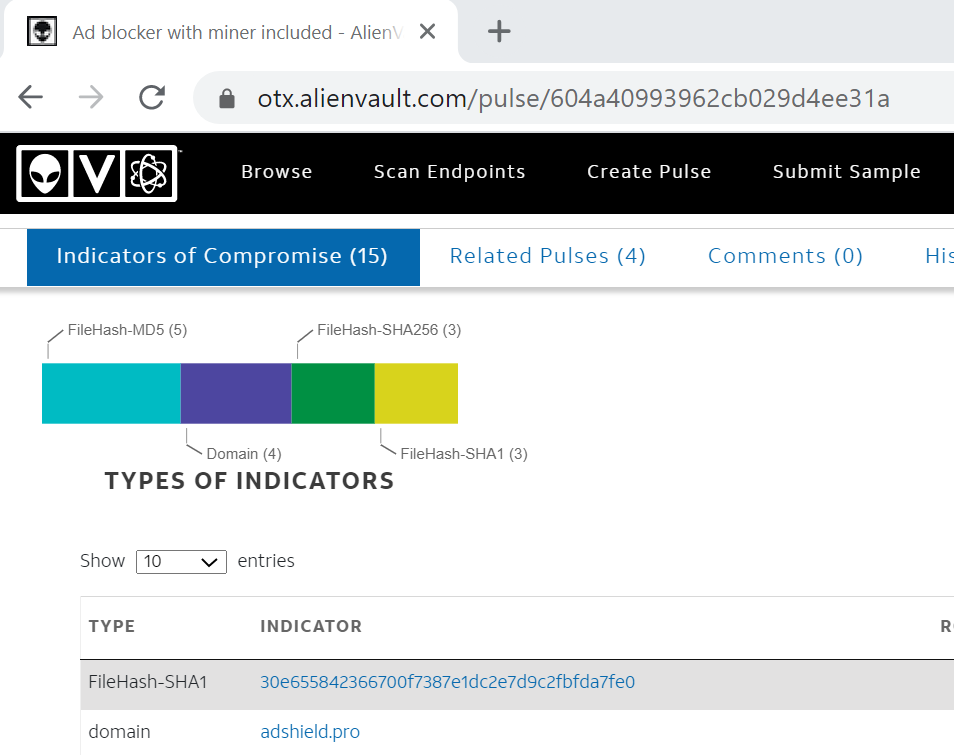 Malware Detection31 março 2025
Malware Detection31 março 2025 -
 Men's Basketball - UTEP Miners31 março 2025
Men's Basketball - UTEP Miners31 março 2025 -
:format(jpg)/cloudfront-us-east-1.images.arcpublishing.com/coindesk/CRKPUWC5NZDIVJH36AVRGTVNK4.png) Firefox Browser Adds Option to Automatically Block Crypto Mining Scripts - CoinDesk31 março 2025
Firefox Browser Adds Option to Automatically Block Crypto Mining Scripts - CoinDesk31 março 2025
você pode gostar
-
 Trouxe o SOUZONES para o The Long Drive31 março 2025
Trouxe o SOUZONES para o The Long Drive31 março 2025 -
 We SAW JEFF The KILLER in the WOODS!!!31 março 2025
We SAW JEFF The KILLER in the WOODS!!!31 março 2025 -
![Mr.Kitty - After Dark [lyrics]](https://i.ytimg.com/vi/N4BmBd0yUoQ/maxresdefault.jpg) Mr.Kitty - After Dark [lyrics]31 março 2025
Mr.Kitty - After Dark [lyrics]31 março 2025 -
Block Puzzle – Apps no Google Play31 março 2025
-
 False Long Hair31 março 2025
False Long Hair31 março 2025 -
 O que voce diz ser? Cristao? Protestante? Evangelico? - O que respondi31 março 2025
O que voce diz ser? Cristao? Protestante? Evangelico? - O que respondi31 março 2025 -
 Nova moto da Peugeot tem desenho futurista e detalhe de 20831 março 2025
Nova moto da Peugeot tem desenho futurista e detalhe de 20831 março 2025 -
 Puffy – Amiyumi (2022, Clear, Vinyl) - Discogs31 março 2025
Puffy – Amiyumi (2022, Clear, Vinyl) - Discogs31 março 2025 -
 Pop Com's- Princesa Pop, jogo de moda! Jogo de meninas e jogo para meninas31 março 2025
Pop Com's- Princesa Pop, jogo de moda! Jogo de meninas e jogo para meninas31 março 2025 -
LOVE ISLAND US - SEASON 5 EPISODE 25 (HD) - Vídeo Dailymotion31 março 2025