Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 28 março 2025

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
Abusing Exceptions for Code Execution, Part 1

Met Council may add Metro Transit security, enforce code of conduct - Minneapolis / St. Paul Business Journal

Sick leave abuse, poor performance and the disciplinary code - Labour Guide South Africa
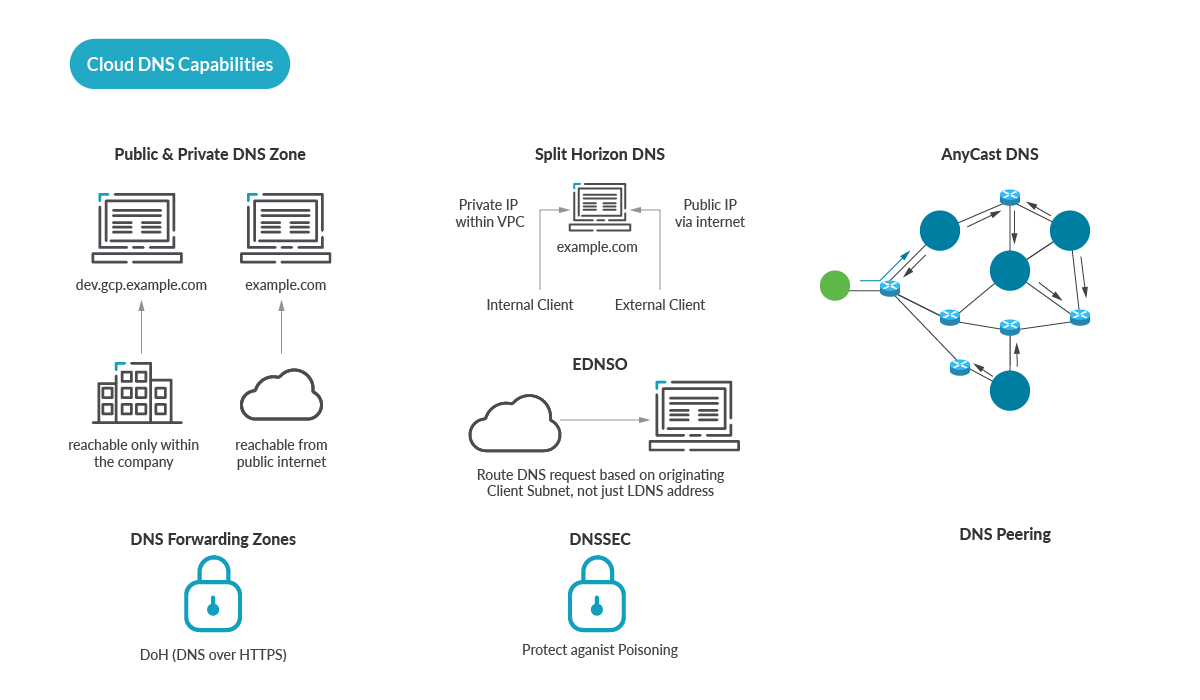
Cloud DNS Security - How to protect DNS in the Cloud – Sysdig

Cybersecurity and digital trade: Getting it right

Project Zero: Injecting Code into Windows Protected Processes using COM - Part 2

Top 10 secure C++ coding practices - Incredibuild

Classification of Web Application Vulnerabilities

Trusted Platform Module - Wikipedia

Patching Perforce perforations: Critical RCE vulnerability discovered in Perforce Helix Core Server

Microsoft Defender Attack Surface Reduction recommendations
Recomendado para você
-
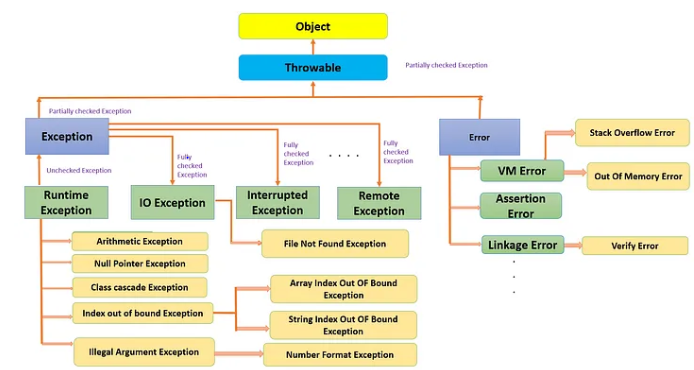
Java Exception Handling - Part I (Exceptions and its types)28 março 2025
-
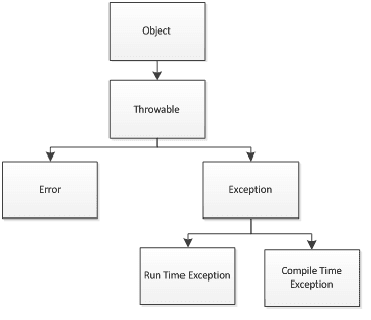 Types of Exceptions - w3resource28 março 2025
Types of Exceptions - w3resource28 março 2025 -
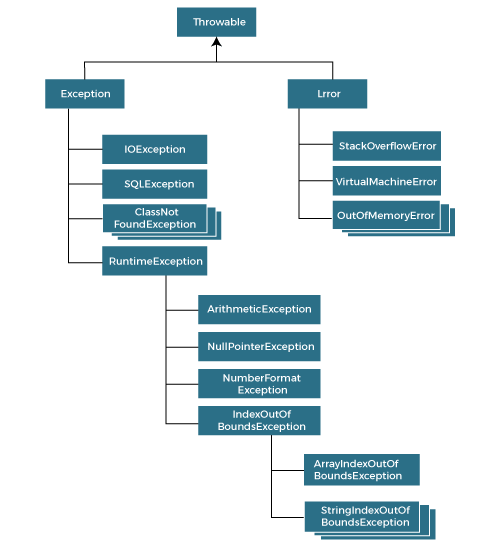 Exception Handling in Java Java Exceptions - javatpoint28 março 2025
Exception Handling in Java Java Exceptions - javatpoint28 março 2025 -
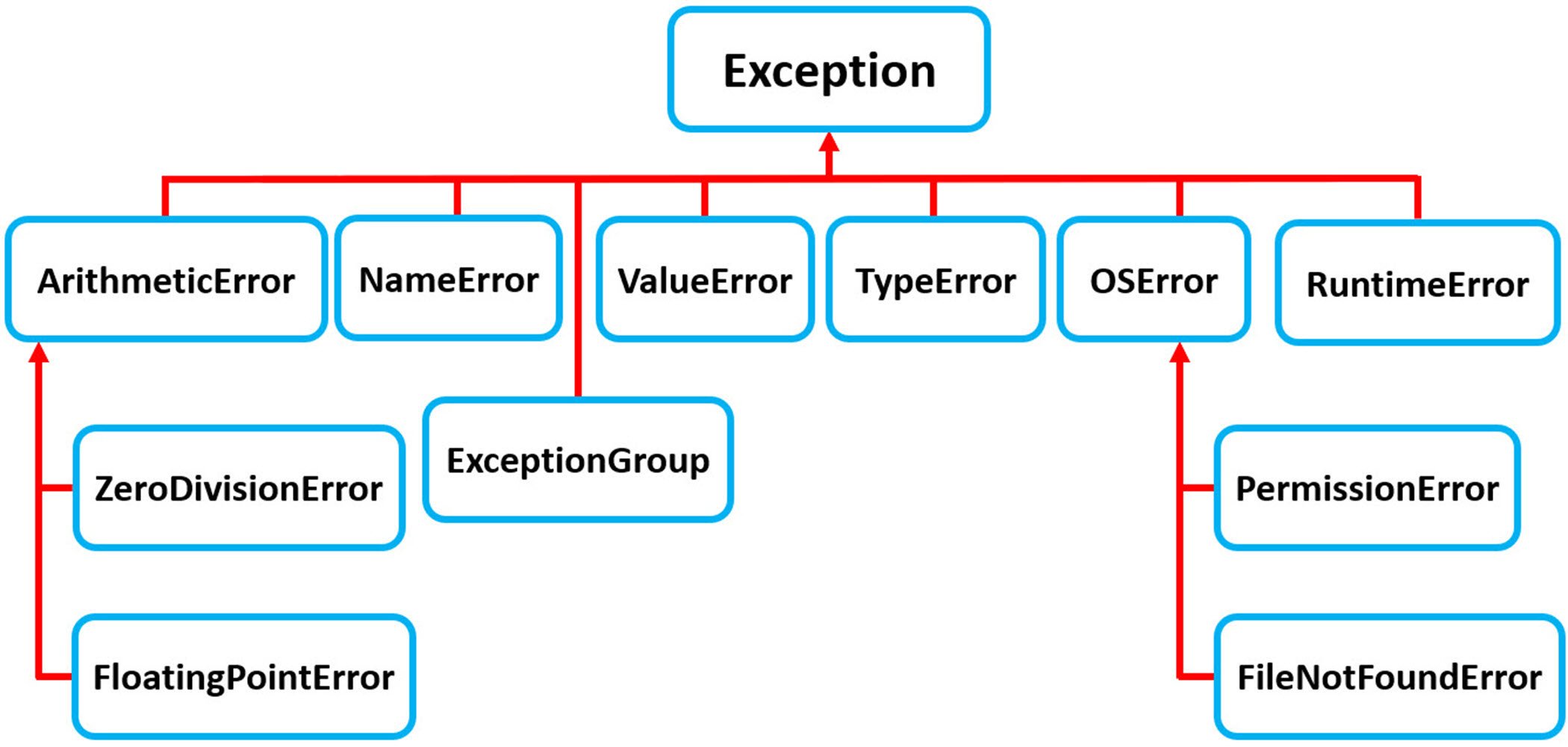 How to Catch Multiple Exceptions in Python – Real Python28 março 2025
How to Catch Multiple Exceptions in Python – Real Python28 março 2025 -
Python Exceptions28 março 2025
-
 JDBC Exception Handling - How To Handle SQL Exceptions28 março 2025
JDBC Exception Handling - How To Handle SQL Exceptions28 março 2025 -
 Exception Text Card Concept Background Stock Photo by ©dizain 56740635228 março 2025
Exception Text Card Concept Background Stock Photo by ©dizain 56740635228 março 2025 -
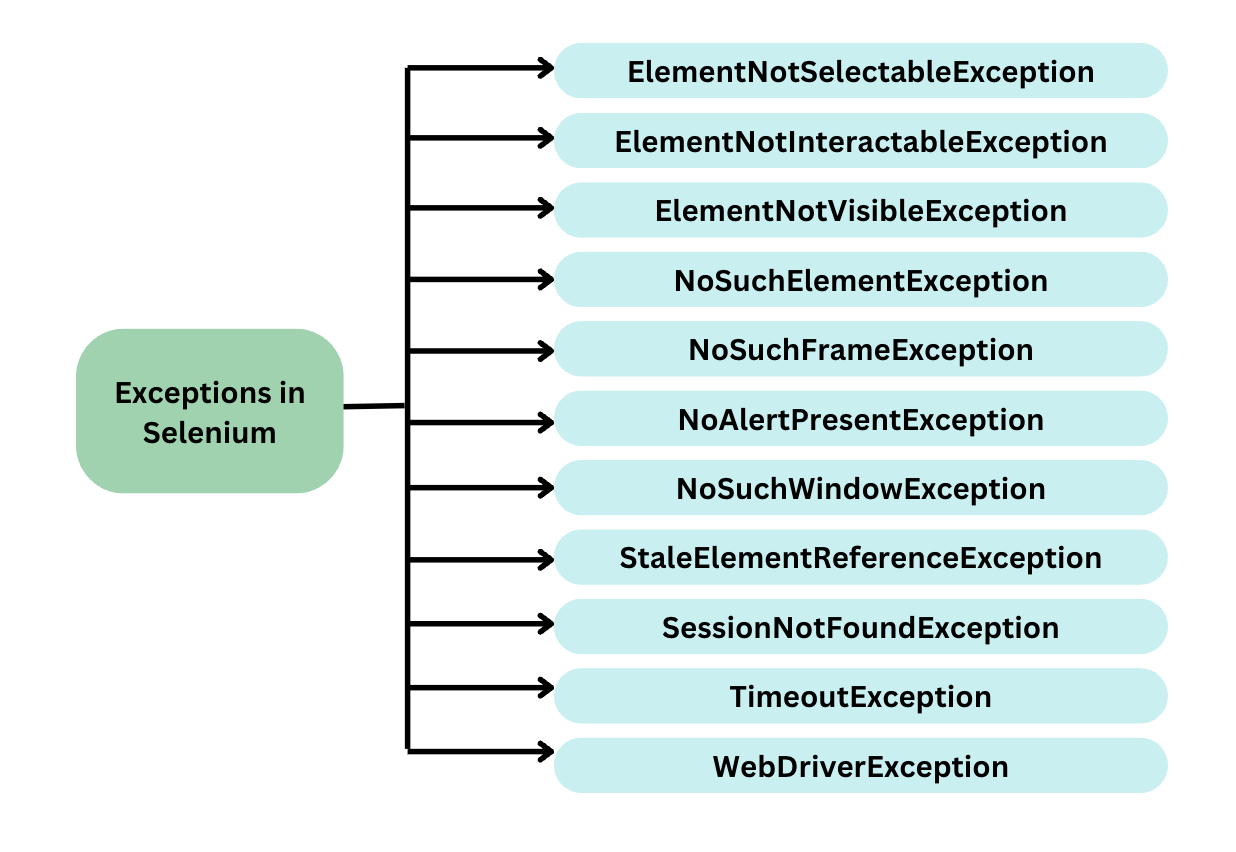 Exceptions in Selenium Webdriver : How to Handle It28 março 2025
Exceptions in Selenium Webdriver : How to Handle It28 março 2025 -
 No Exceptions Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime28 março 2025
No Exceptions Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime28 março 2025 -
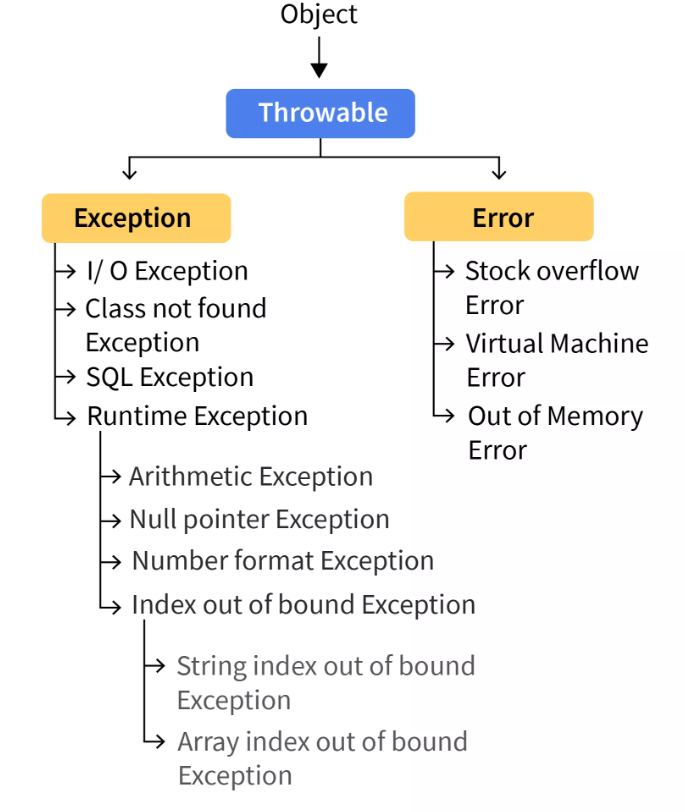 Exception Handling in Java. Exception Handling in Java is one of…, by Abhijeet Verma28 março 2025
Exception Handling in Java. Exception Handling in Java is one of…, by Abhijeet Verma28 março 2025
você pode gostar
-
 trading shadow, venom, gravity, and quake : r/bloxfruits28 março 2025
trading shadow, venom, gravity, and quake : r/bloxfruits28 março 2025 -
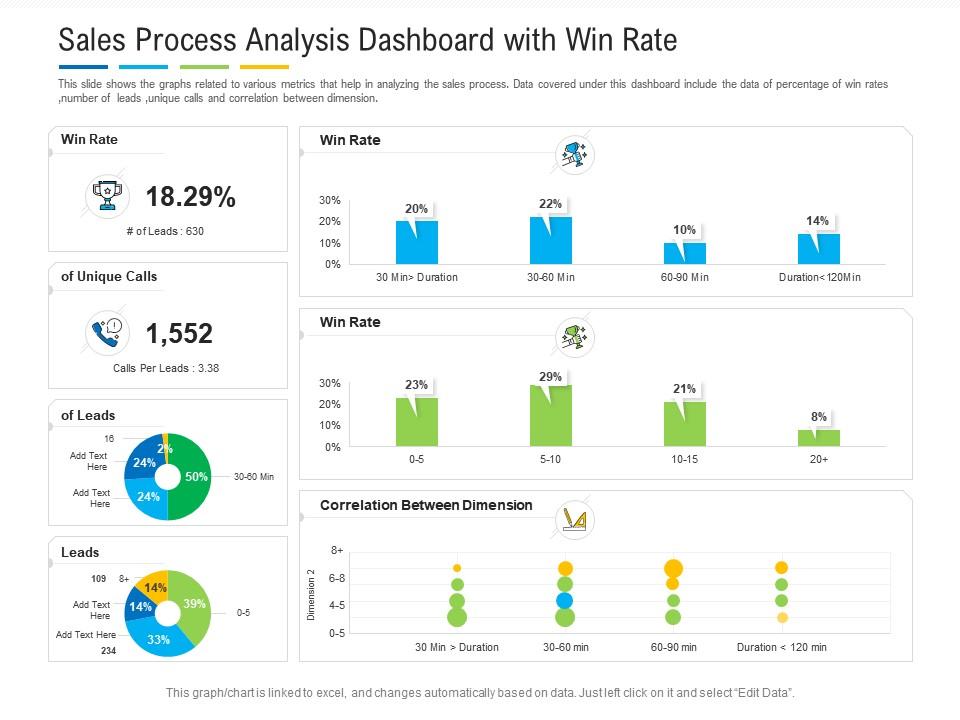 Sales Process Analysis Dashboard With Win Rate Powerpoint Template28 março 2025
Sales Process Analysis Dashboard With Win Rate Powerpoint Template28 março 2025 -
 Download Pro Evolution Soccer 201628 março 2025
Download Pro Evolution Soccer 201628 março 2025 -
 Como estão as consolas servidas de jogos exclusivos?28 março 2025
Como estão as consolas servidas de jogos exclusivos?28 março 2025 -
 Sudoku Mine - Médio28 março 2025
Sudoku Mine - Médio28 março 2025 -
 Drop your hottest take on the series : r/KimetsuNoYaiba28 março 2025
Drop your hottest take on the series : r/KimetsuNoYaiba28 março 2025 -
 20th CENTURY FOX logo. Free logo maker.28 março 2025
20th CENTURY FOX logo. Free logo maker.28 março 2025 -
 Honkai Star Rail players crown the game's best standard character28 março 2025
Honkai Star Rail players crown the game's best standard character28 março 2025 -
 Guilty Gear Strive Creator Shocked at Bridget Controversy #guiltygearstrive #bridget #guiltygear28 março 2025
Guilty Gear Strive Creator Shocked at Bridget Controversy #guiltygearstrive #bridget #guiltygear28 março 2025 -
 Apple iPhone 15 Pro Max 1TB – Smartphones – Loja Online28 março 2025
Apple iPhone 15 Pro Max 1TB – Smartphones – Loja Online28 março 2025